Problem
Companies federated with your Lync / Skype for Business environment have recently noticed that the status contacts in your organization briefly show as Updating…:
… then eventually changes to Presence unknown:
You’ve confirmed that the services on the Edge server are all Running:
However, reviewing the event logs show numerous errors logged in reference to the Lync Standard Server:
Log Name: Lync Server
Source LS Web Conferencing Edge Server
Event ID: 41987
Level: Error
Web Conferencing Server connection failed to establish.
Over the past 30 minutes Lync Server has experienced incoming TLS connection failures 120 time(s). The error code of the last failure is 0x80096004 (The signature of the certificate cannot be verified.
) and the last connection was from the host “”.
Cause: This can occur if this box is not properly configured for TLS communications with remote Web Conferencing Server.
Resolution:
Check your topology configuration to ensure that both this host and remote Web Conferencing Server can validate each other TLS certificates and are otherwise trusted for communications.
Log Name: Lync Server
Source LS Protocol Stack
Event ID: 14428
Level: Error
TLS outgoing connection failures.
Over the past 86 minutes, Lync Server has experienced TLS outgoing connection failures 15 time(s). The error code of the last failure is 0x80096004(TRUST_E_CERT_SIGNATURE) while trying to connect to the server “svrlyncstd02.domain.internal” at address [10.1.1.66:5061], and the display name in the peer certificate is “Unavailable”.
Cause: Most often a problem with the peer certificate or perhaps the host name (DNS) record used to reach the peer server. Target principal name is incorrect means that the peer certificate does not contain the name that the local server used to connect. Certificate root not trusted error means that the peer certificate was issued by a remote CA that is not trusted by the local machine.
Resolution:
Check that the address and port matches the FQDN used to connect, and that the peer certificate contains this FQDN somewhere in its subject or SAN fields. If the FQDN refers to a DNS load balanced pool then check that all addresses returned by DNS refer to a server in the same pool. For untrusted root errors, ensure that the remote CA certificate chain is installed locally. If you have already installed the remote CA certificate chain, then try rebooting the local machine.
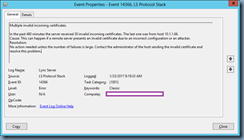
Log Name: Lync Server
Source LS Protocol Stack
Event ID: 14366
Level: Error
Multiple invalid incoming certificates.
In the past 480 minutes the server received 30 invalid incoming certificates. The last one was from host 10.1.1.66.
Cause: This can happen if a remote server presents an invalid certificate due to an incorrect configuration or an attacker.
Resolution:
No action needed unless the number of failures is large. Contact the administrator of the host sending the invalid certificate and resolve this problem.
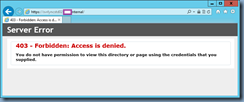
Attempting to browse the the FQDN of the Lync Standard Server from the Edge server displays the following webpage with a certificate warning:
· If you arrived at this page by clicking a link, check the website address in the address bar to be sure that it is the address you were expecting.
· When going to a website with an address such as https://example.com, try adding the ‘www’ to the address, https://www.example.com.
For more information, see “Certificate Errors” in Internet Explorer Help.
Solution
One of the reasons why presence would stop working and the event ID errors above to be thrown is if the Lync Edge server’s internal network interface certificate was recently updated by the issuing Root certificate issuing the updated certificate is not installed onto the Lync Edge server. Note that the Lync Edge server is never joined to the domain so if the internal network interface certificate is issued by an internal CA then the root CA certificate along with the chain must be manually imported into the Trusted Root Certification Authorities certificate store on the Edge server:
Once this has been completed, proceed to restarting the Lync Edge server’s services and confirm that the following informational event logs are written:
Verify that the following page is now displayed when you browse the the FQDN of the Lync Standard Server from the Edge server:












2 Responses
Thank you so much for this article. It is such a simple fix and saves a lot of headache. I've spent hours on the phone with Microsoft trying to find out why the new FE pool coulnt use the Edge resources. Thanks!!!
This comment has been removed by a blog administrator.