Recent Visitor 148
I recently had to remove the federation between an on-prem Active Directory and an Azure Directory so that we could re-federate the on-prem Active Directory to a new Azure Directory. The process is quite easy but there doesn’t appear to be clear documentation for the steps so I thought it would be worth while writing this blog post just in case I ever had to do this again in the future.
Begin by removing the domain from the Azure Directory that you no longer need it to be federated to. The tasks required are as follows:
- Stop the DirSync
- Disable ADFS federation
- Delete the directory (you can’t have the same on-prem directory added to more than one Azure Directory)
Within the new Azure Directory that you are going to federate the on-prem directory to:
- Create a new global admin account for this Azure Directory
- Add the new domain to Azure Directory
- Create the required TXT record to verify the domain
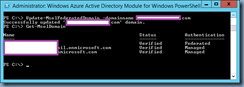
- Launch the WAAD console and execute Connect-MsolService
- Log in with the global admin account for the Azure Directory
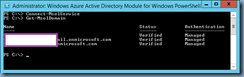
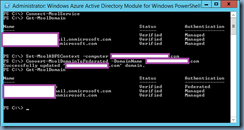
- Execute Get-MsolDomain to ensure that the on-prem domain is listed and the Authentication field is listed as Managed
- Execute Set-MsolADFSContext -computer <yourInternalADFSserverFQDN>
- Execute Convert-MsolDomainToFederated -DomainName <domainToFederateFQDN>
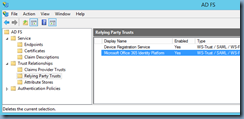
- The federation to the previous Azure Directory would have created a Microsoft Office 365 Identity Platform in the Relying Party Trusts folder in the AD FS console as shown here:
- Proceed by deleting it:
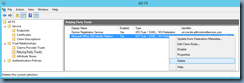
- Then recreating it by executing Update-MsolFederatedDomain -domainname <domainToFederateFQDN>
- Refreshing the Relying Party Trusts folder should now show a recreated Microsoft Office 365 Identity Platform
- Reconfigure and then run DirSync now to synchronize the on-prem Active Directory with the Azure Directory