Problem
You’ve successfully completed configuring Freshservice with your on-premise ADFS so users can use their Active Directory credentials to log into the portal as per the following documentation:
Configuring ADFS for Freshservice with SAML 2.0
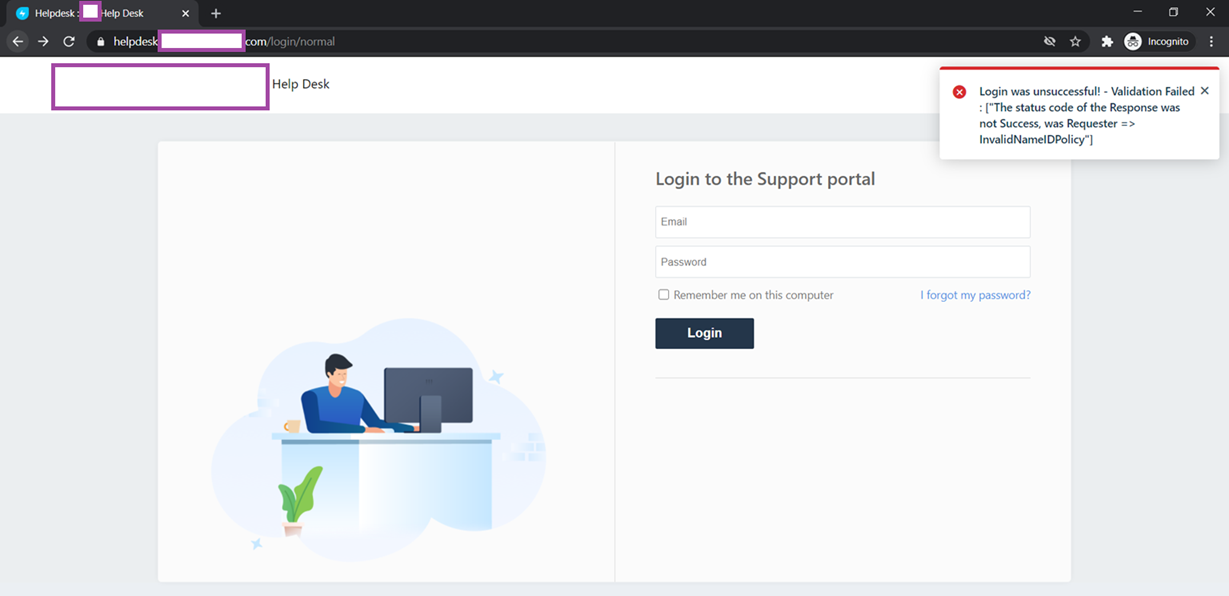
However, upon successfully entering Active Directory credentials to the AD FS login page, the redirect back to the Freshservice portal fails with:
Login was unsuccessful! – Validation Failed : [“The status code of the Response was not Success, was Requester => InvalidNameIDPolicy”]
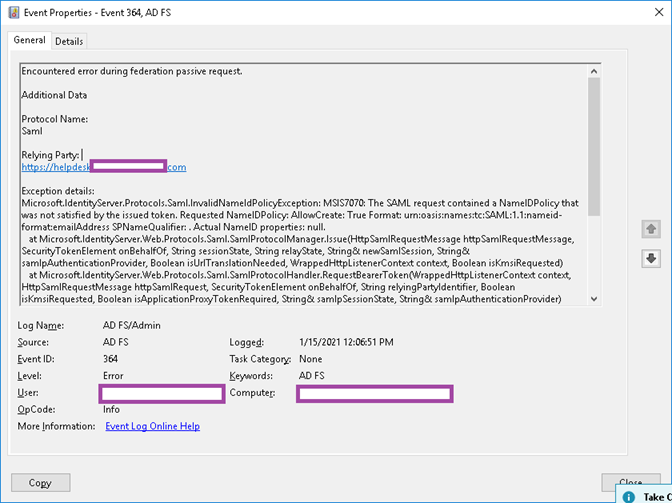
Reviewing the event logs of the AD FS server reveals the following event ID 364 logged:
Encountered error during federation passive request.
Additional Data
Protocol Name:
Saml
Relying Party:
https://helpdesk.contoso.com
Exception details:
Microsoft.IdentityServer.Protocols.Saml.InvalidNameIdPolicyException: MSIS7070: The SAML request contained a NameIDPolicy that was not satisfied by the issued token. Requested NameIDPolicy: AllowCreate: True Format: urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress SPNameQualifier: . Actual NameID properties: null.
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolManager.Issue(HttpSamlRequestMessage httpSamlRequestMessage, SecurityTokenElement onBehalfOf, String sessionState, String relayState, String& newSamlSession, String& samlpAuthenticationProvider, Boolean isUrlTranslationNeeded, WrappedHttpListenerContext context, Boolean isKmsiRequested)
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolHandler.RequestBearerToken(WrappedHttpListenerContext context, HttpSamlRequestMessage httpSamlRequest, SecurityTokenElement onBehalfOf, String relyingPartyIdentifier, Boolean isKmsiRequested, Boolean isApplicationProxyTokenRequired, String& samlpSessionState, String& samlpAuthenticationProvider)
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolHandler.BuildSignInResponseCoreWithSerializedToken(HttpSamlRequestMessage httpSamlRequest, WrappedHttpListenerContext context, String relyingPartyIdentifier, SecurityTokenElement signOnTokenElement, Boolean isKmsiRequested, Boolean isApplicationProxyTokenRequired)
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolHandler.BuildSignInResponseCoreWithSecurityToken(SamlSignInContext context, SecurityToken securityToken, SecurityToken deviceSecurityToken)
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolHandler.Process(ProtocolContext context)
at Microsoft.IdentityServer.Web.PassiveProtocolListener.ProcessProtocolRequest(ProtocolContext protocolContext, PassiveProtocolHandler protocolHandler)
at Microsoft.IdentityServer.Web.PassiveProtocolListener.OnGetContext(WrappedHttpListenerContext context)
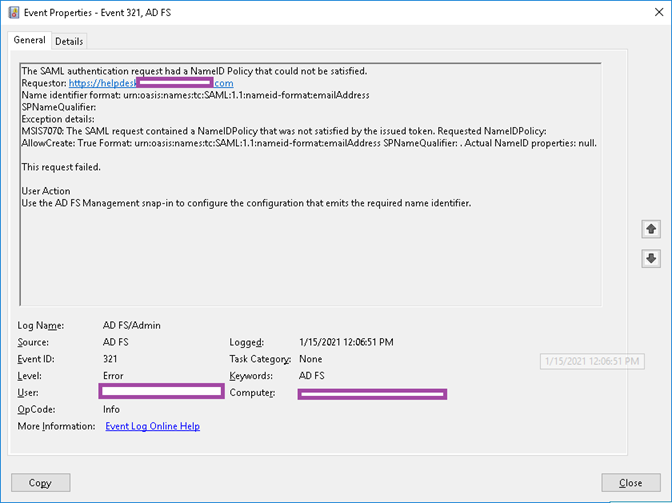
An event ID 321 is also logged:
The SAML authentication request had a NameID Policy that could not be satisfied.
Requestor: https://helpdesk.contoso.com
Name identifier format: urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress
SPNameQualifier:
Exception details:
MSIS7070: The SAML request contained a NameIDPolicy that was not satisfied by the issued token. Requested NameIDPolicy: AllowCreate: True Format: urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress SPNameQualifier: . Actual NameID properties: null.
This request failed.
User Action
Use the AD FS Management snap-in to configure the configuration that emits the required name identifier.
Solution
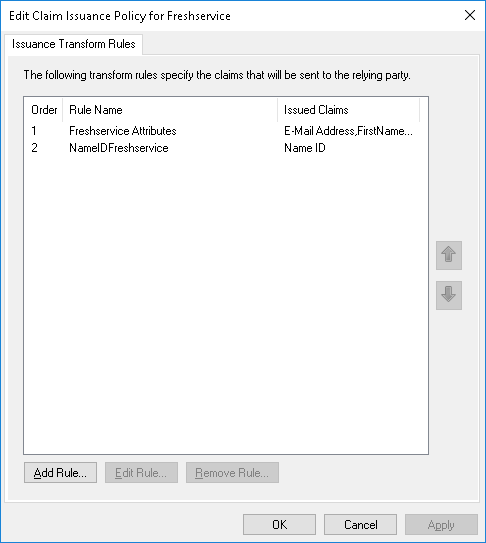
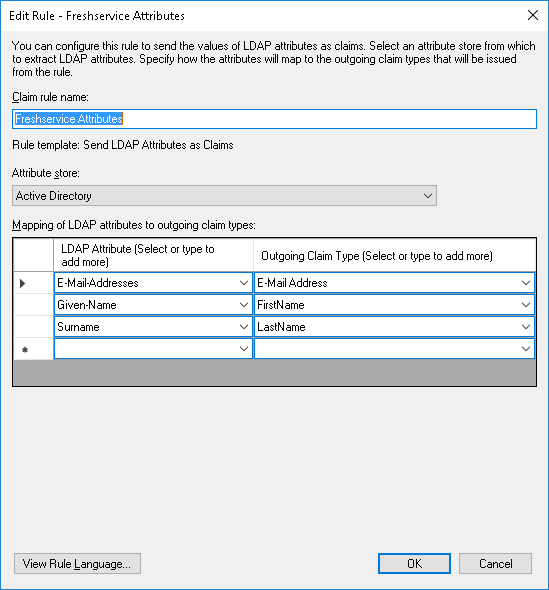
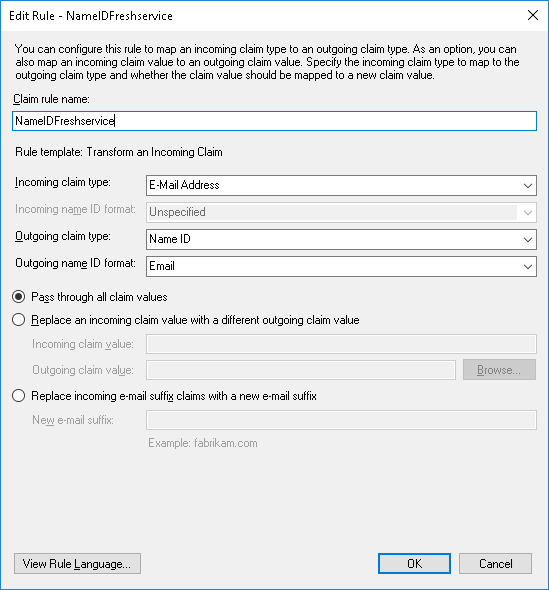
A ticket was opened with Freshservice but the support engineer was unable to resolve the issue so I reviewed the configuration and paid attention to the Issuance Transform Rules:
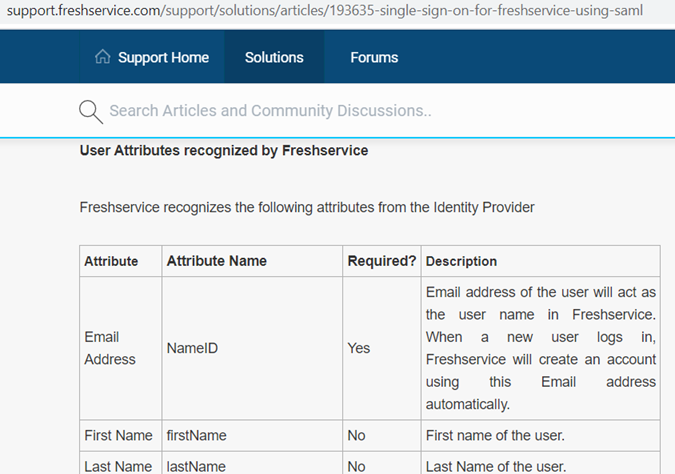
Then read some of the documentation provided by Freshservice, which pointed to the fact that the user’s email address will act as the user name in Freshservice:
| Attribute | Attribute Name | Required? | Description |
| Email Address | NameID | Yes | Email address of the user will act as the user name in Freshservice. When a new user logs in, Freshservice will create an account using this Email address automatically. |
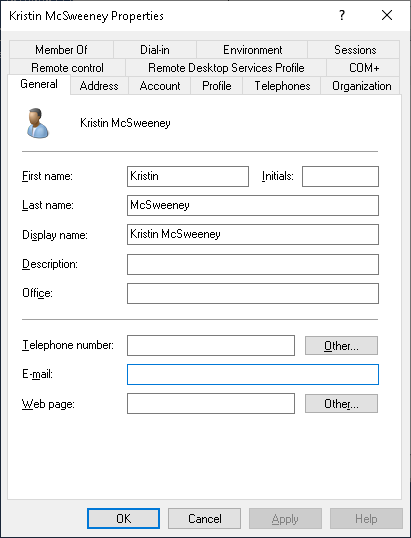
The client for this environment originally had their Office 365 deployed without AD Connect and therefore user accounts in Active Directory did not have the E-mail attribute populated:
This ended up being the reason why the error message was thrown as a blank e-mail address was being passed to Freshservice. Populating the user’s E-mail attribute corrected the issue.
In addition to the issue above, some accounts began displaying the following error message after their E-mail attribute was populated:
If you get a Login Unsuccessful
This ended up being caused by an contact that already existed in Freshservice and could be remediated by navigating to User Management > Contacts and deleting the object: