I recently had to work with a Microsoft support engineer to troubleshoot an Active Directory Certificate Services issue and managed to write down a few commands he used during the troubleshooting process and thought I’d write a blog post so I can refer to them in the future since I’m bound to forget.
Command to collect CA information CRL:
Before starting the troubleshooting, the engineer ran the following commands to collect base information.
The following certutil command lists the Enterprise Root or Subordinate CAs found in Active Directory:
C:>certutil
Entry 0:
Name: `test’
Organizational Unit: `’
Organization: `’
Locality: `’
State: `’
Country/region: `’
Config: `conspschsrv.contosotest’
Exchange Certificate: `’
Signature Certificate: `’
Description: `’
Server: `conspschsrv.contoso’
Authority: `test’
Sanitized Name: `test’
Short Name: `test’
Sanitized Short Name: `test’
Flags: `1′
Web Enrollment Servers: `’
Entry 1:
Name: `CONTOSO ROOT CA’
Organizational Unit: `’
Organization: `’
Locality: `’
State: `’
Country/region: `’
Config: `conCERTSRV.contosoContoso ROOT CA’
Exchange Certificate: `’
Signature Certificate: `’
Description: `’
Server: `conCERTSRV.contoso’
Authority: `CONTOSO ROOT CA’
Sanitized Name: `CONTOSO ROOT CA’
Short Name: `CONTOSO ROOT CA’
Sanitized Short Name: `CONTOSO ROOT CA’
Flags: `1′
Web Enrollment Servers: `’
Entry 2: (Local)
Name: `CONTOSO-Sub-CA’
Organizational Unit: `’
Organization: `’
Locality: `’
State: `’
Country/region: `’
Config: `conSCASRV01.contosoCONTOSO-Sub-CA’
Exchange Certificate: `’
Signature Certificate: `conSCASRV01.contoso_CONTOSO-Sub-CA.crt’
Description: `’
Server: `conSCASRV01.contoso’
Authority: `CONTOSO-Sub-CA’
Sanitized Name: `CONTOSO-Sub-CA’
Short Name: `CONTOSO-Sub-CA’
Sanitized Short Name: `CONTOSO-Sub-CA’
Flags: `13′
Web Enrollment Servers: `’
CertUtil: -dump command completed successfully.
Note that the above output shows that there are currently 3 Enterprise CAs that is found in Active Directory.
——————————————————————————————————————————————————-
The net config rdr command shows how the redirector or workstation is currently configured on your computer. The following output is from a command prompt on the Enterprise Subordinate CA:
C:>net config rdr
Computer name \conSCASRV01
Full Computer name conSCASRV01.contoso
User name TLuk
Workstation active on
NetBT_Tcpip_{4C336E8C-128B-4B8F-99EC-BFD21F1B9E6D} (005056A10F07)
Software version Windows Server 2012 Standard
Workstation domain con-CONTOSO
Workstation Domain DNS Name contoso
Logon domain con-CONTOSO
COM Open Timeout (sec) 0
COM Send Count (byte) 16
COM Send Timeout (msec) 250
The command completed successfully.
——————————————————————————————————————————————————-
The following nltest /dclist:contoso command lists the domain controllers found in Active Directory:
C:>nltest /dclist:contoso
Get list of DCs in domain ‘contoso’ from ‘\DC2.contoso’.
DC2.contoso [DS] Site: Default-First-Site-Name
DC3.contoso [DS] Site: Default-First-Site-Name
DC1.contoso [PDC] [DS] Site: Default-First-Site-Name
The command completed successfully
C:>
——————————————————————————————————————————————————-
Command to dump certificate information CRL:
The support engineer suspected that there was something wrong with the published CRL so the following command was executed to check the start and end validity date of the file (I’ve highlighted this information in red:
C:>certutil -dump Contoso-Root-CA.crl
X509 Certificate Revocation List:
Version: 2
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.10 RSASSA-PSS
Algorithm Parameters:
30 00
Issuer:
CN=Contoso-Root-CA
Name Hash(sha1): b8e12ef9872c9e93d65fbd132a2402fa4b0d0dde
Name Hash(md5): 9fe720a14c52866f8ffb9819659eb114
ThisUpdate: 11/30/2013 3:12 PM
NextUpdate: 11/30/2014 3:32 AM
CRL Entries: 0
CRL Extensions: 5
2.5.29.35: Flags = 0, Length = 18
Authority Key Identifier
KeyID=b2 be 9e 66 df 55 a8 33 b7 72 00 77 a5 2a e5 19 68 6a d9 90
1.3.6.1.4.1.311.21.1: Flags = 0, Length = 3
CA Version
V0.0
2.5.29.20: Flags = 0, Length = 3
CRL Number
CRL Number=02
1.3.6.1.4.1.311.21.4: Flags = 0, Length = f
Next CRL Publish
Saturday, November 29, 2014 3:22:16 PM
1.3.6.1.4.1.311.21.14: Flags = 0, Length = cb
Published CRL Locations
[1]Locations
Distribution Point Name:
Full Name:
URL=ldap:///CN=Contoso-Root-CA,CN=BHLRCASRV01,CN=CDP,CN=Pub
lic Key Services,CN=Services,CN=Configuration,DC=contoso,DC=domain,DC=bm?certificateR
evocationList?base?objectClass=cRLDistributionPoint (ldap:///CN=Contoso-Root-CA,CN
=BHLRCASRV01,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=contoso
,DC=domain,DC=bm?certificateRevocationList?base?objectClass=cRLDistributionPoin
t)
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.10 RSASSA-PSS
Algorithm Parameters:
30 00
Signature: UnusedBits=0
0000 cb e3 84 68 86 fc af 5c 83 6a 1d 5a ef f8 74 11
0010 ae d8 33 c3 0f cf 99 f9 24 d7 47 d6 90 09 24 a9
0020 c9 06 c0 4b 3e 91 bc 96 5b cc ba 87 d5 72 68 1c
0030 60 a7 fc a3 a1 6c 00 b5 5a 76 23 a4 29 89 fe bf
0040 0d 9c 0f 74 57 15 9a 05 39 0f a3 05 39 a5 08 33
0050 c5 b2 31 3d 16 b2 69 dd 16 62 09 db d3 d0 37 db
0060 65 77 bc 4e 06 84 40 0d e9 35 7c 03 c3 a0 36 4a
0070 57 6c c8 3f 9b 07 b2 16 f1 16 43 46 de 27 96 7e
0080 5b 32 e9 6d 24 eb 58 8d 1f 0f e5 ea 41 e4 64 e7
0090 66 8d 46 f0 0c 4c 3c ab 13 12 da 3a f3 ac 2f cb
00a0 37 80 9f a5 1d 6d bf db cc 2e 48 ae 00 b1 56 83
00b0 e3 0e 02 9a 29 e4 55 58 22 4b a1 ba 0f 1f bd 14
00c0 3e 0b 37 dc af b3 35 33 48 ba 1c bc b5 6f 22 47
00d0 49 99 d5 ac e5 68 fd 4f 30 7e ba 63 25 d9 6f 3e
00e0 0c 3e 26 84 0b 29 6c d4 76 7c 44 8f 2b 71 a0 e9
00f0 80 71 e0 2f 11 ec e7 02 62 3e 60 05 3a 27 bb 3d
CRL Hash(md5): 40 65 78 62 9a 86 fa 9f fb 77 57 43 e1 bc 23 66
CRL Hash(sha1): 26 92 02 b6 8e ab 26 41 b3 17 18 76 3f c5 41 45 a6 75 54 5e
CRL Hash(sha256): 6da08e776a532e6b92d1ebe7ffd477606f37b7d3659361661c50b8be9919cc
c3
Signature Hash: 438535ec7850261962dff88f6b73c487ae45633c
CertUtil: -dump command completed successfully.
The CRL file this command references can be found in the following directory:
C:WindowsSystem32certsrvCertEnroll
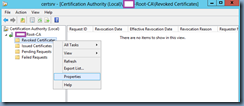
Note that if this is too short, the period can be extended by launching the Certificate Authority administration console:
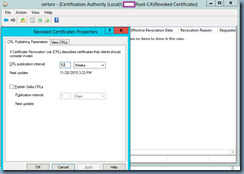
… right clicking on the Revoked Certificates and selecting properties:
… then changing the CRL publication interval to the desired duration:
——————————————————————————————————————————————————-
Command to publish certificate to LDAP
Updating the CRL file for http access is simply copying the CRL file from the Root CA’s C:WindowsSystem32certsrvCertEnroll folder to the same folder on the Subordinate CA but to update the one published through LDAP, the command certuitl -dspublish <Your-Root-CA>.crl <YourSubOrdinateCAServerName is ran on the subordinate CA:
C:>certutil -dspublish Contoso-Root-CA.crl CONSCASRV01
ldap:///CN=Contoso-Root-CA,CN=BHLSCASRV01,CN=CDP,CN=Public Key Services,CN=Service
s,CN=Configuration,DC=contoso,DC=bhl,DC=bm?certificateRevocationList
Base CRL added to DS store.
CertUtil: -dsPublish command completed successfully.
———————————————————————————————————————————————————-
Verifying published CRL paths:
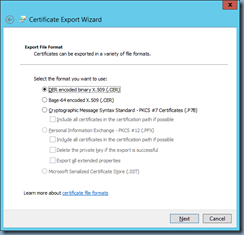
To verify the published CRL paths, simply export the subordinate CA’s certificate without the private key to a DER format file:
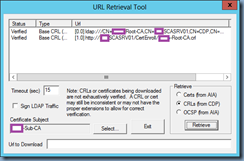
Then launch the URL Retrieval Tool by executing certuilt -url <exportedCA>.cer and use the Retrieve button with CRLs (from CDP) selected to verify the accessibility and validity of the files:
——————————————————————————————————————————————————-
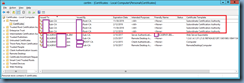
Determining which certificate the current CA is using:
If the certificate for the CA has been renewed several times, you may end up seeing a list similar to the following:
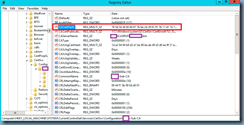
While most of us would probably just look for the certificate with the latest expiry date, another way to do it is to open up the Registry Editor and navigate to the following key:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesCertSvcConfiguration<YourCAName>
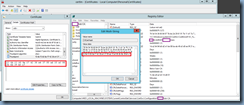
The CACertHash key can be used to identify which certificate is currently in use:
… by comparing it to the certificate’s Thumbprint as such: