I recently had to upgrade 2 Lync Server 2013 Edge servers (one on Windows Server 2008 R2 and the other on Windows Server 2012) and since I haven’t written a blog post demonstrating the process, I went ahead to document one of the deployments for this blog post.
Preparing the Edge Server
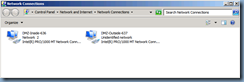
There are quite a few tasks required before you can actually begin installing Edge services onto the server you’ve allocated for this server role and the first item you should turn your attention to is the network interface configuration. Make sure you have 2 NICs for your Edge server as shown in the following screenshot:
More information about NIC interfaces can be found at the following URL:
Set Up Network Interfaces for Edge Servers
https://technet.microsoft.com/en-us/library/gg412847.aspx
The NIC I’ve labeled DMZ-Inside-636 will be the NIC that is used to send traffic into your internal network while the NIC labeled DMZ-Outside-637 will be the NIC that is connected to either your DMZ network or directly to the internet.
How you configure your Edge server’s NICs will depend on your network topology such as whether there are DNS servers available in the perimeter network and how your DMZ network is set up. The official Edge deployment guide for the previous version Lync Server 2010 recommends to use external DNS servers and host records to resolve internal domain servers for the most secure configuration but and while I’ve gone demonstrated in one of my old Lync Server 2010 Edge posts:
Deploying Lync Server 2010 Edge Server
https://blog.terenceluk.com/deploying-lync-server-2010-edge-server/
… this post will set up Edge to use internal DNS servers for name resolution (I always avoid host files whenever I can).
**Note that both of my NIC interfaces on the Edge server is in a true DMZ network segment. This means the internal NIC is not on the same subnet as my Lync Enterprise Pool server.
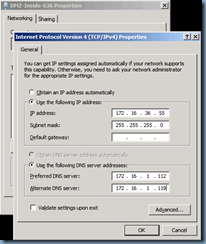
Internal NIC Configuration
This is what the internal NIC settings for the Edge server looks like:
Note that there is no default gateway specified but the DNS servers are filled in with the internal DNS servers.
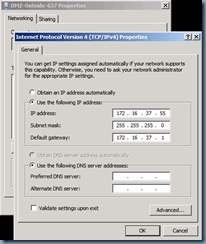
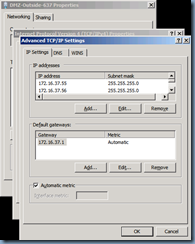
External DMZ NIC Configuration
This is what the DMZ NIC settings for the Edge server looks like:
Note that the default gateway is filled out but the DNS servers isn’t. Two additional IP addresses (total of 3) are assigned to the external interface:
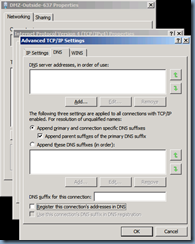
The external interface shouldn’t attempt to register with DNS so the Register this connection’s addresses in DNS is unchecked:
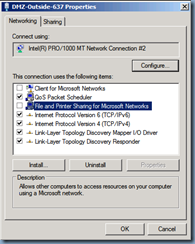
The external interface also does not need Client for Microsoft Networks and File and Printer Sharing for Microsoft Networks enabled:
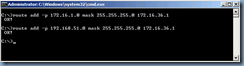
Static Routes
Static routes will also be needed for your Edge server to get to the internal server VLAN and workstations so proceed with documenting what VLANs your Edge will need to have access to and add the static routes onto the server as persistent routes:
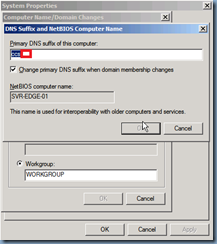
Configure a DNS Suffix for the Edge Server
A DNS suffix is automatically added if a server is joined to the domain but since the Edge server isn’t and shouldn’t be, we will need to manually add it:
Prerequisites for Windows Server 2008 R2
The following packages will need to be installed if you are using Windows Server 2008 R2 as the operating system for your Edge server:
Install Microsoft .NET Framework 4.5:
Proceed with downloading and installing Microsoft .NET Framework 4.5 from the following URL:
https://www.microsoft.com/en-us/download/details.aspx?id=30653
Install PowerShell 3.0:
Continue and PowerShell 3.0 from the following URL: https://www.microsoft.com/en-us/download/details.aspx?id=34595
There’s a list for 4 items for download and the way to determine which one you’re supposed install is actually noted at the bottom. Since we’re installing PowerShell 3.0 onto a Windows Server 2008 R2 SP1 server, proceed by downloading the following file:
WINDOWS6.1-KB2506143-x64.MSU
Install Windows Identity Foundation:
Continue and Windows Identity Foundation from the following URL: https://www.microsoft.com/en-us/download/details.aspx?id=17331
Windows6.1-KB974405-x64.msu
Prerequisites for Windows Server 2012
The only package you’ll need to install when using Windows Server 2012 as the operating system is the Windows Identity Foundation which can be added via the following cmdlet in PowerShell:
Add-WindowsFeature Windows-Identity-Foundation
Defining the Edge Topology
Once the Edge server has been configured, the next step is to define and then publish the topology:
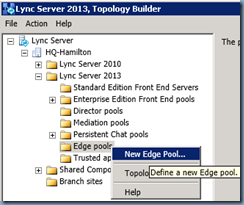
Fire up Topology Builder:
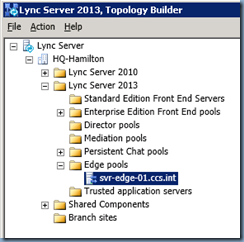
Right click on the Edge pools folder and select New Edge Pool…:
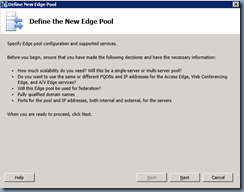
The wizard to define a new edge pool will launch:
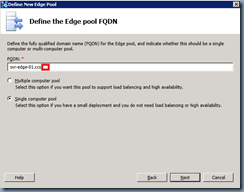
This example will demonstrate how to define a single computer pool:
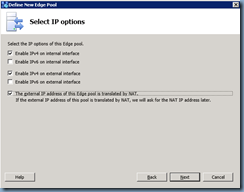
Select the settings as it pertains to your environment:
**Note that the Edge server external IPs I’ll be using are NAT-ed IPs which is why the “The external IP address of this Edge pool is translated by NAT.” is selected.
**Note for more information about the Use a single FQDN & IP Address checkbox, see my previous post: https://blog.terenceluk.com/should-i-use-use-single-fqdn-ip-address/
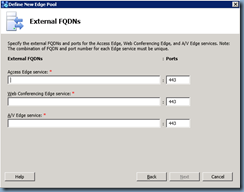
For the purpose of this example, the Use a single FQDN & IP Address checkbox was not checked so fill in the appropriate FQDNs:
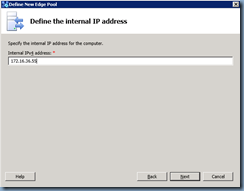
Specify the internal interface’s IP address:
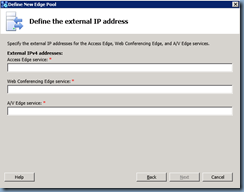
Specify the Edge server’s external IP addresses (these will be my NAT-ed internal IP addresses):
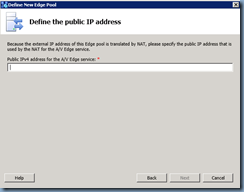
Since I selected The external IP address of this Edge pool is translated by NAT checkbox earlier, I will need to provide the true external IP address for my A/V Edge service:
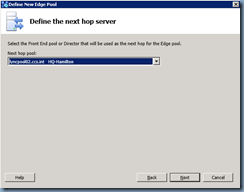
Select the Next hop pool:
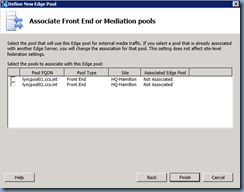
Select the front end pools you would like to associate the Edge server with. Note that I have 2 pools listed because I have a 2010 and 2013 pool:
Clicking the Finish button will bring you back to the Topology Builder:
With the new topology defined, proceed with publishing it:
Exporting the Topology for the Edge Install
Since the Edge server is not a part of the domain, there is no easy way for it to download the topology during the install which is why we will need to manually export the topology on your front-end server and copy it over to the Edge server:
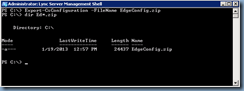
Open up the Lync Server Management Shell and execute:
Export-CsConfiguration -FileName <fileNameOfYourChoice.zip>
Copy the zip package to your Edge server:
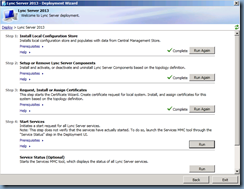
Installing Edge Server
Launch setup.exe from the Lync installation binaries:
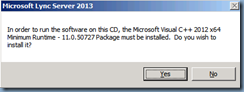
Setup will automatically install Microsoft Visual C++ 2012 x64 Minimum Runtime – 11.0.50727:
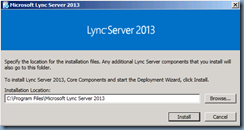
Choose Install or Update Lync Server System from the Deployment Wizard:
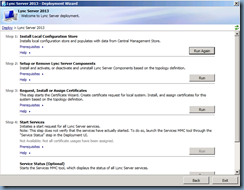
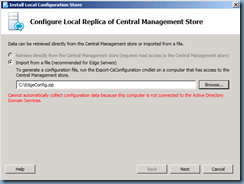
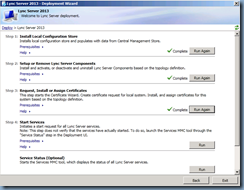
Install Local Configuration Store:
Select Install Local Configuration Store:
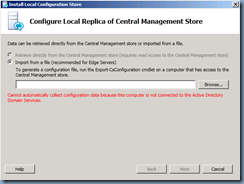
There is no option to retrieve the topology from the CMS because the Edge server is not joined to the domain so choose Import from a file and locate the zip package we copied over from the front-end server:
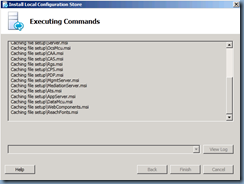
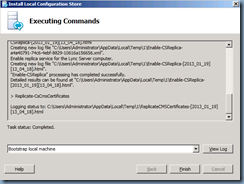
Setup Lync Server Components:
Once the local configuration store has been installed, proceed with installing the Lync Server Components:
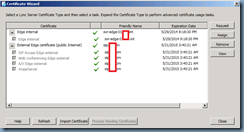
Request, Install or Assign Certificates:
Proceed with requesting and assigning the certificates for the Edge server’s internal and external interfaces:
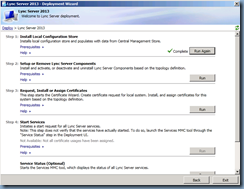
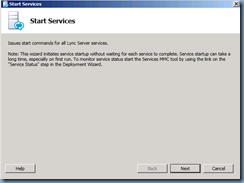
Start Services:
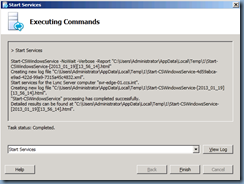
With the certificates issued and assigned, proceed with starting the services:
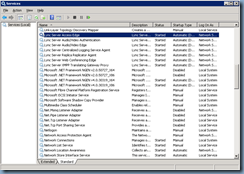
Check Service Status:
Every though the last step Service Status is listed as option, it’s always best to perform it anyways to ensure that all the services are listed as Started:
Once the services have been verified to be started, proceed with testing remote connectivity, federation and other Edge services.



13 Responses
Great work! I respect consultants like you who don't hide their work and not teach others.
hi Terence
thanks for the past. do you think you can elaborate on why external interface should "register this connection's address in dns" box unchecked.
Great post that covers the essentials for an edge without HLBs. I would like to add be careful with antivirus on the edge servers as we have had a big problem with Trend AV which was a nightmare to find.
Hey,
Great Blog!!!
I've followed the steps to configure my Edge server.
In the Step when the wizard asks for the public IP address for the AV edge I've specified the the Public IP for AV Edge. What about the remaining two public IP?
I have three DMZ (External facing) private IP natted with three public IP.
Where can I specify the IP for SIP and Webconf?
Kindly Help.
This comment has been removed by the author.
This comment has been removed by the author.
This comment has been removed by the author.
Great job, just one question. I have a single public IP and not possible to get more than 1. It's also not possible in my region to get a static IP. Our IP changes every so often. During the Edge topology build, I see the builder wants my public IP. What happens when that public IP changes? Thank you
Anonymous no need to swear. The reason why Static IP is preferred so that you dont have to go back and make changes to the Ip address. If you IP chnages you are going to have to manually change it in the Topology and run the cmmand enable-csTopology all the time.
I am wondering the same thing as Shrikant, how do you specify the other two NAT'ed public IPs? For access and web conf? It only asks for the NAT IP fo A/V? Thanks in advance.
Terence,
Thanks. I discovered your blog early this month when I started an assignment to deploy the Access Edge service for a firm with a functioning internal Lync 2013 system up and running. Followed your guide with other sources.
I've run into an issue with the RTCMEDIARELAY service failing to start. Most sources say this indicates an incomplete SAN listing in the public cert, but ours lists the sip, web conf and a/v URLs. Do the lyncdiscover, dialin and meet URLs need to be listed too? Your example/image only list sip, web conf and a/v. Your advice will be very helpful.
Thanks,
Dawud
Hi, i have successfully configured lync with edge but when i m going to sign in from externally i m getting error , can’t sign into lync we’re having trouble connecting to the server, any suggestion,
Hi, great article love your work,
I'm struggling with setting up my static route. Internal nic has ip 192.168.36.228/24 and no gateway.
My internal network is 192.168.0/24 what is the correct command for the static route?
I've tried many times but I don't seem to be able to ping the internal lan