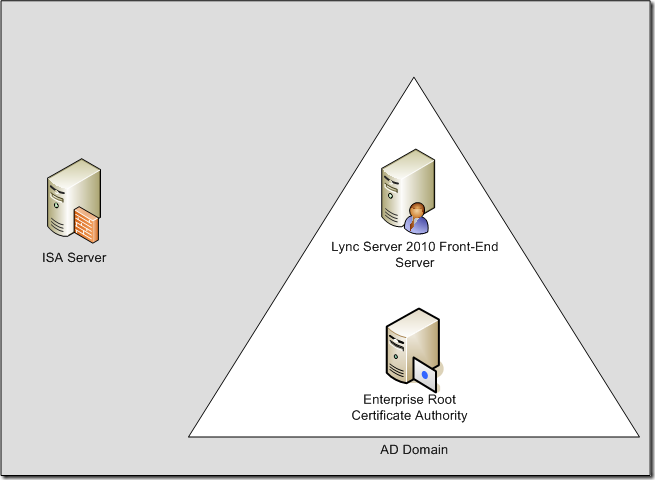
While this particular problem isn’t specific to OCS 2007 R2 or Lync Server 2010, I happened to come across it during one of my deployments. Let’s first start by providing some background information on the servers involved:
ISA 2006 Server – Serves as a reverse proxy server using a web publishing rule to publish a IIS site from our Lync Server 2010 server.
Lync Server 2010 – Serves as the front-end server that requires ISA to publish one of the directories served from IIS 7.0.
Internal Enterprise Root CA – Serves as a certificate authority for Active Directory and is used to issue certificates for the Lync Server 2010 front-end server to use for the published IIS 7.0 sites.
As shown in the diagram above, the ISA server used for reverse proxy isn’t apart of the domain. This means that when we’re publishing a site on the Lync Server 2010 front-end server using SSL bridging on ISA, we need to import the enterprise root CA certificate onto the ISA server or else when the Lync Server 2010 server presents its certificate to ISA, ISA will not trusted it.
What’s interesting about the problem I encountered is that we’ve recently refreshed out internal root CA because it was going to expire but we had forgotten to re-import the new root CA to our ISA server. What ended up happening was that whenever I used ISA to browse the https webpage the Lync Server 2010 presented, I would get a message about the certificate not being valid:
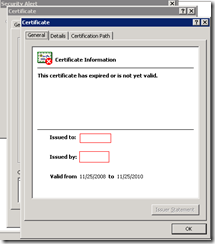
The security certificate has expired or is not yet valid.
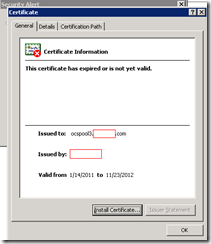
During the troubleshooting process when I didn’t know we forgot to update the root CA on the ISA server’s Trusted Root Certification Authorities, I would see the following details about the certificate:
This certificate has expired or is not yet valid.
What’s confusing about what I saw was that the Valid from date was correct because the date when I was experiencing this issue was January 22, 2011 and it was between the valid from range. This also initially steered me away from realizing that the new root certificate was not imported onto this ISA server.
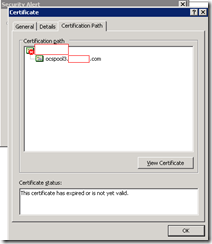
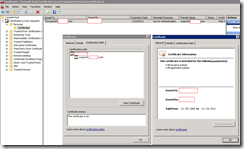
As I continued to navigate deeper into the certificate’s information, I noticed that the information for the root certificate was incorrect:
I knew for a fact that the root CA was renewed sometime in November 2010 it was odd that the ISA server would receive such a certificate from the internal Lync Server 2010 front-end server. To confirm what certificate the front-end was presenting, I logged on to it to check:
As shown in the above screenshot, when I review the certificate that the Lync Server 2010 front-end server was presenting to ISA, the root CA had the correct Valid from date range. After stopping and thinking about what might be causing this, I finally realized that the renewed internal root certificate was not imported to the to the ISA server that was not a part of the domain so I went ahead to export the certificate and imported it onto ISA. From there on, the warning message was gone.
Basically what I learned from all this was this:
If you have a server that isn’t a part of your domain and has an expired root certificate issued by your enterprise root CA, any certificates issued by that enterprise root CA will always have the imported root certificate listed as the issuing authority. Whew, that sounds extremely confusing and I don’t think there’s really an easy way to explain this so I hope the above screenshots with descriptions will help mystify all this.



One Response
I don't know how many issues I have encountered with non domain joined machines and the *time/date* is always to blame. This being said, I did not check the time and date this time round (again) and came to your post. Thank you for saving such a frustrating morning!
Appreciate it!