I recently received quite a few complaints that users were unable to change settings such as page sizes and colour on printers they used to be able to do so after they were migrated to VMware View virtual desktops. I paid a visit to the client office and noticed that all of the users had the same printer mapped 2 or more times and the redundant mappings were all redirected printers using Thinprint drivers:
From there on, their complaint was no surprise since the Thinprint drivers are no where close to the full blown drivers that the printer manufacturer supplies. The solution was simple—disable these Thinprint redirected printers. The difficulty? The following VMware KB does not appear to work:
Disabling ThinPrint on a VMware View Client
I combed through the KB and made sure I followed the exact instructions but wasn’t able to get Thinprint disabled:
I gave up on the KB after 15 minutes when I realized I probably can’t turn off Thinprint with these registry changes so I decided to simply use GPO to disable the:
- TP AutoConnect Service
- TP VC Gateway Service
… services and the challenge we’ll immediately encounter is that the default security template that is supplied by your domain controllers won’t have an entry for this service since it’s not a standard Windows service. Having ran into a similar situation in the past, I knew I’ll need to create a new security template so the following shows the process of doing this.
**Note: I also understand that we could use batch files to accomplish this but I prefer using GPOs when I’m able to.
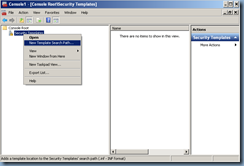
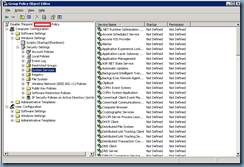
Start by logging onto a virtual desktop with these 2 services and run the Microsoft Management Console:
Add the Security Templates snap-in:
You’ll notice that sometimes you’ll see default security listed and sometimes you won’t. The security templates are usually stored in the C:Windowssecuritytemplates folder but you’ll notice that even if you update the template search path to that folder, you may not see templates listed:
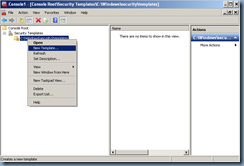
Note that whether you see any templates listed is not important as we’ll be creating a new one anyways so continue by select the path you just created and choose New Template:
Give the new template a name:
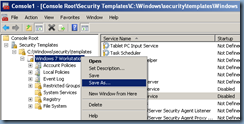
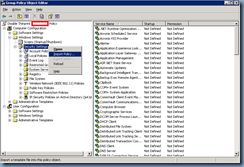
Navigate to the System Services node:
Change the:
- TP AutoConnect Service
- TP VC Gateway Service
… to Disabled.
Proceed with saving the template to somewhere accessible by your domain controller:
Log onto your domain controller and open Group Management Policy Console and create a new policy:
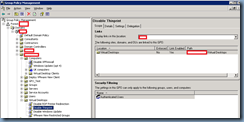
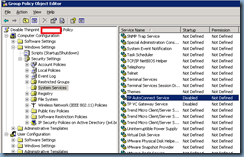
Navigate to Computer Configuration –> Windows Settings –> Security Settings –> System Services:
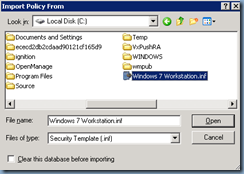
Right click on the Security Settings node and select Import Policy…:
Select the inf file you saved your template as:
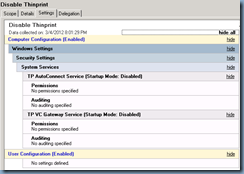
Verify that the
- TP AutoConnect Service
- TP VC Gateway Service
… has been disabled:
Close the GPO and verify the settings:
Test this on one of your desktops by running gpupdate /force and gpresult –r –scope computer to verify that the policy has been applied. Once the policy has been applied, you should now see the Thinprint redirected printers disappear from the Devices and Printers window.

![clip_image002[4] clip_image002[4]](https://lh3.ggpht.com/-9y1ydKZBVHY/T1Qz99J_tiI/AAAAAAAAMro/r4_FPmmWMzg/clip_image002%25255B4%25255D_thumb.jpg?imgmax=800)
![clip_image002[6] clip_image002[6]](https://lh3.ggpht.com/-MDcRv7W6d5U/T1Qz_I0SglI/AAAAAAAAMr8/MbEQF8GV34Q/clip_image002%25255B6%25255D_thumb.jpg?imgmax=800)
![clip_image002[8] clip_image002[8]](https://lh5.ggpht.com/-fF8BkCUeFhA/T1Q0AcRDLvI/AAAAAAAAMsM/wDtMZyX05Vk/clip_image002%25255B8%25255D_thumb.jpg?imgmax=800)
![clip_image002[10] clip_image002[10]](https://lh5.ggpht.com/-YnkOALZZYVw/T1Q0B-VJ99I/AAAAAAAAMsc/dZTNMenE9OA/clip_image002%25255B10%25255D_thumb.jpg?imgmax=800)
![clip_image002[12] clip_image002[12]](https://lh3.ggpht.com/-GVGTt01alDY/T1Q0DasVCeI/AAAAAAAAMss/uSakJJ3xv7Q/clip_image002%25255B12%25255D_thumb.jpg?imgmax=800)
![clip_image002[14] clip_image002[14]](https://lh3.ggpht.com/-gki8pBNwc00/T1Q0EodY-3I/AAAAAAAAMs8/yPCWsQ9bBfs/clip_image002%25255B14%25255D_thumb.jpg?imgmax=800)
![clip_image002[16] clip_image002[16]](https://lh3.ggpht.com/-7Oo7w1t04RA/T1Q0F4MDTLI/AAAAAAAAMtM/icc1TDluXnM/clip_image002%25255B16%25255D_thumb.jpg?imgmax=800)
![clip_image002[18] clip_image002[18]](https://lh4.ggpht.com/-mX0wR1-tdNY/T1Q0HHjbkpI/AAAAAAAAMtc/1WqzmIYnUig/clip_image002%25255B18%25255D_thumb.jpg?imgmax=800)
![clip_image002[20] clip_image002[20]](https://lh4.ggpht.com/-u51XXzRX970/T1Q0JSIq7GI/AAAAAAAAMt8/-eD696yuj-M/clip_image002%25255B20%25255D_thumb.jpg?imgmax=800)
![clip_image002[22] clip_image002[22]](https://lh3.ggpht.com/-m_t8zM00pZE/T1Q0KbvJHGI/AAAAAAAAMuM/sLzDcudnfQI/clip_image002%25255B22%25255D_thumb.jpg?imgmax=800)
![clip_image002[24] clip_image002[24]](https://lh3.ggpht.com/-JojovgSOy1g/T1Q0MT71wPI/AAAAAAAAMus/MxgsIeRHKrc/clip_image002%25255B24%25255D_thumb.jpg?imgmax=800)
![clip_image002[26] clip_image002[26]](https://lh5.ggpht.com/-nCZX8H-JUkY/T1Q0Nub24gI/AAAAAAAAMu8/_VUqxHBPZyM/clip_image002%25255B26%25255D_thumb.jpg?imgmax=800)
![clip_image002[28] clip_image002[28]](https://lh4.ggpht.com/-cShIskBhbfI/T1Q0OmzdJ5I/AAAAAAAAMvM/RwThgGfxfCM/clip_image002%25255B28%25255D_thumb.jpg?imgmax=800)
![clip_image002[30] clip_image002[30]](https://lh5.ggpht.com/-HlVs29CU0oE/T1Q0PtGGWJI/AAAAAAAAMvc/9MLfUy-dU7o/clip_image002%25255B30%25255D_thumb.jpg?imgmax=800)
![clip_image002[32] clip_image002[32]](https://lh3.ggpht.com/-Hw-OkwYNoFM/T1Q0Q9F38iI/AAAAAAAAMvs/gt3bA3oyDEY/clip_image002%25255B32%25255D_thumb.jpg?imgmax=800)
![clip_image002[34] clip_image002[34]](https://lh4.ggpht.com/-RW6cUGXfhvo/T1Q0SrfFzlI/AAAAAAAAMv8/_nY0tHH9zyc/clip_image002%25255B34%25255D_thumb.jpg?imgmax=800)
![clip_image002[36] clip_image002[36]](https://lh3.ggpht.com/-C0WjJtA7S3E/T1Q0U1eHGOI/AAAAAAAAMwc/KZMyF9yBgWI/clip_image002%25255B36%25255D_thumb.jpg?imgmax=800)


2 Responses
Helped me. Thanks! +1
Sweet! That helped us a lot!