I recently had an colleague who asked me about the virus scanning capabilities of SharePoint and how it would handle situations where a malicious file was uploaded. This wasn’t something I knew off the top of my head so I did a bit of reading and some testing with a SharePoint Online site.
Microsoft Documentation
Information about the built-in virus protection capabilities can be found here:
Built-in virus protection in SharePoint Online, OneDrive, and Microsoft Teams
https://learn.microsoft.com/en-us/defender-office-365/anti-malware-protection-for-spo-odfb-teams-about
What happens if an infected file is uploaded to SharePoint Online?
The Microsoft 365 virus detection engine scans files asynchronously (at some time after upload). If a user tries to download a file in a web browser or from Teams that hasn’t been scanned, a scan is triggered before the download is allowed. All file types are not automatically scanned. Heuristics determine the files to scan. When a file is found to contain a virus, the file is flagged.
Here’s what happens:
- A user uploads a file to SharePoint Online.
- SharePoint Online, as part of its virus scanning processes, later determines if the file meets the criteria for a scan.
- If the file meets the criteria for a scan, the virus detection engine scans the file.
- If a virus is found within the scanned file, the virus engine sets a property on the file that indicates the file is infected.
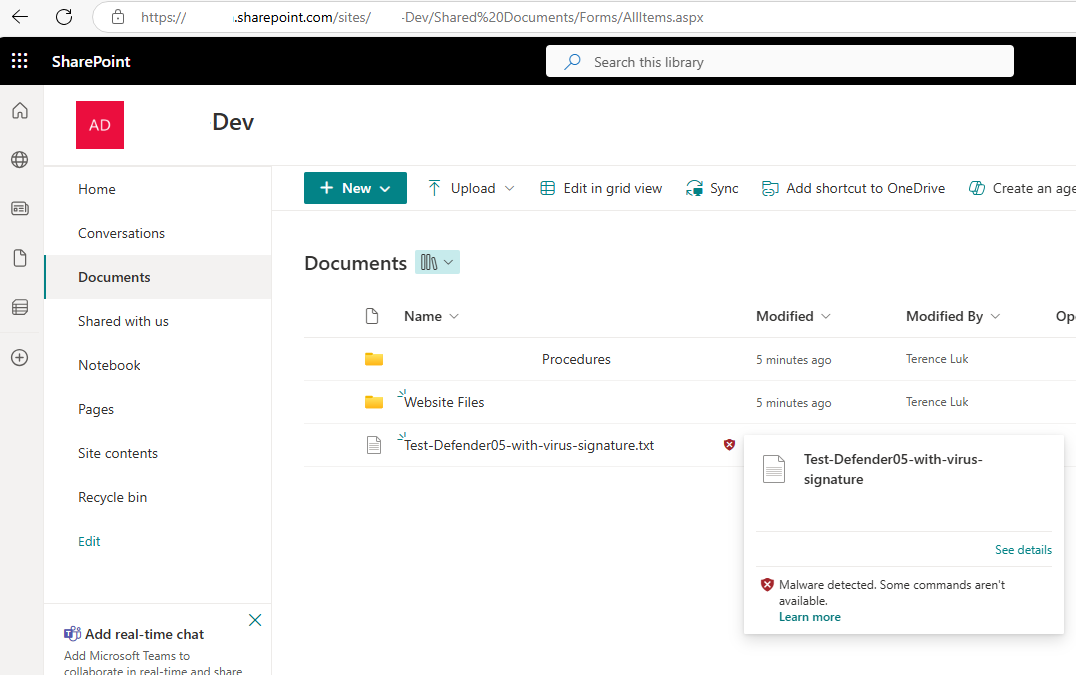
The documentation indicates that files uploaded to SharePoint Online are scanned asynchronously (after some time post upload) and immediately if an attempt is made to download the file. I’ve gone ahead and tested this, and noticed that a test EICAR (https://www.eicar.org/download-anti-malware-testfile/) file I created is usually picked up as being malicious within 5 minutes as shown in the screenshot below:
Malware detected. Some commands aren’t available.
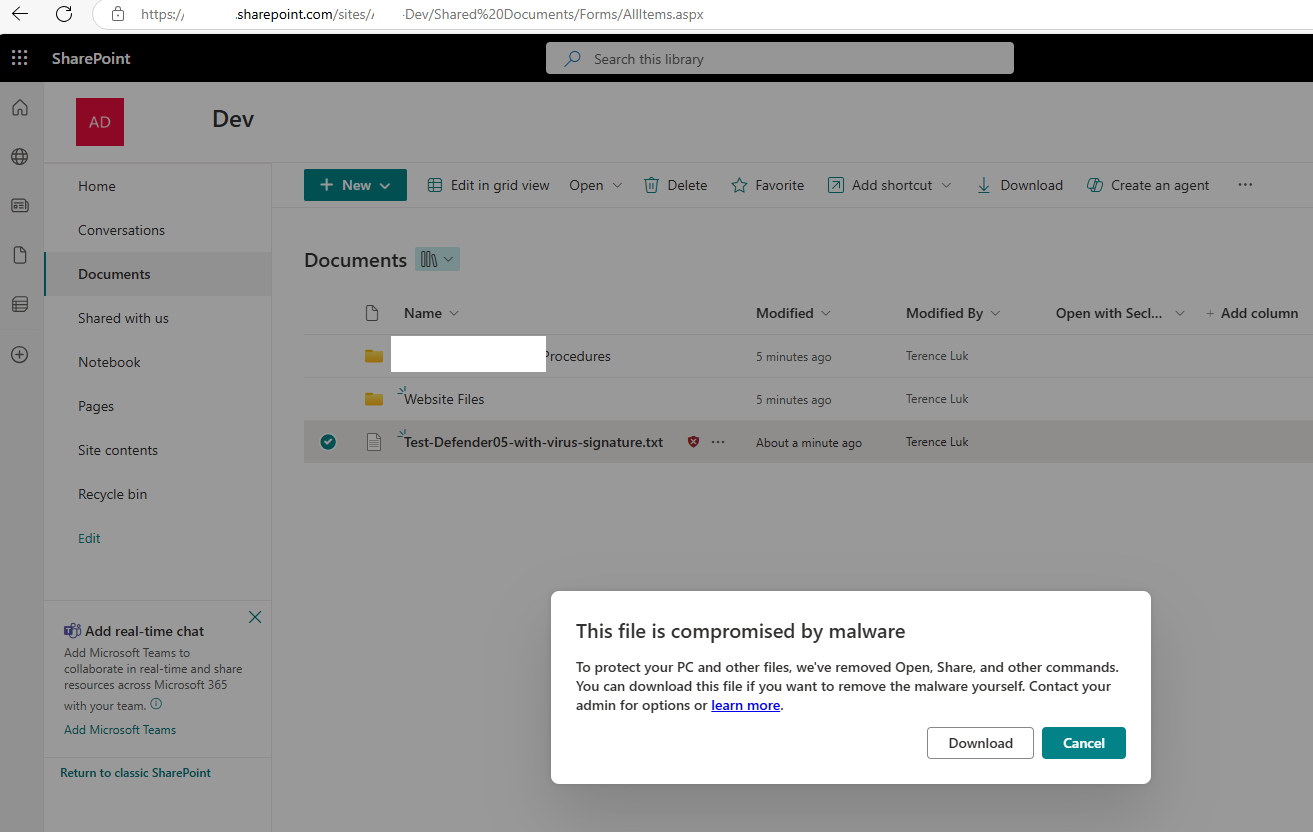
By default, SharePoint Online wouldn’t prevent the user from downloading but it would warn the user when attempted to download:
If there is the desire to prevent the user from downloading the file, this can be changed via the DisallowInfectedFileDownload parameter as described here: https://learn.microsoft.com/en-us/defender-office-365/anti-malware-protection-for-spo-odfb-teams-about#what-happens-when-a-user-tries-to-download-an-infected-file-by-using-the-browser
To change this behavior so users can’t download infected files, even from the anti-virus warning window, admins can use the DisallowInfectedFileDownload parameter on the Set-SPOTenant cmdlet in SharePoint Online PowerShell. The value $true for the DisallowInfectedFileDownload parameter completely blocks access to detected/blocked files for users.
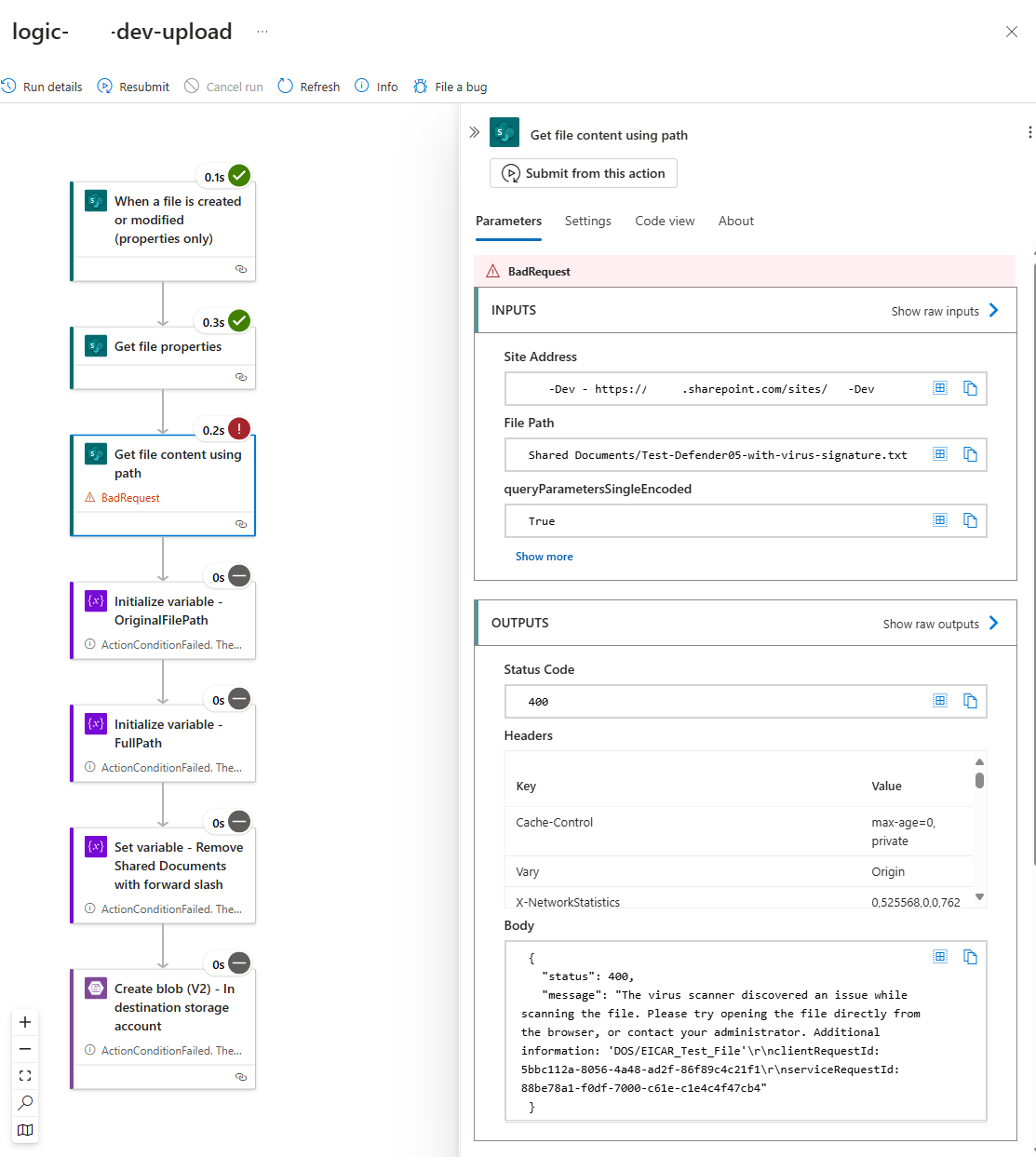
I’ve also tested this with a Logic App that attempts to copy the malicious file to a storage account and can confirm that the step where it attempts to Get file content using path would fail with a BadRequest:
I hope this provides a demonstration of the virus scanning capability and behavior for SharePoint Online.