One of the features I’ve liked a lot when I was able to work with clients who had Azure AD Premium 2 or Enterprise Mobility + Security (EMS) E5 licenses is the Privileged Identity Management (PIM). This feature has a lot of offer when it comes to one of the most neglected operations that every organization should have:
managing privileged access. In this post, I will describe attempt to describe the benefits of it as well as demonstrate some of its features.
What is Azure Privileged Identity Management (PIM)?
Let me begin by saying that Microsoft provides an excellent write up and video about PIM, which can be found here:
What is Azure AD Privileged Identity Management?
https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-configure
When I am asked this question, I usually provide the following:
The short and condensed explanation of Azure’s Privileged Identity Management (PIM) is that provides you with the tools to manage, control, monitor, and audit access to resources in the organization. An example of this could be a consultant is engaged in a project with your organization and I need administrative rights in Azure because I need to add or manage another domain so this I am granted the global admin role but the role then never gets removed. The use of a consultant can easily be interchanged with any administrator on the team who was granted the global admin role and never gets removed, which is very similar to, say, the Enterprise Admins or Domain Admins group in an on-premise Active Directory. Another example could be that we do not want administrators to have persistent administrative permissions whenever they log into Azure so we would like them to have the ability to elevate their permissions. Lastly, another example could be that there is suspicion the account used to sign up for the Azure tenant had its password reset at some point and is being used so an audit of the history is required.
The following are the key features taken straight from the Microsoft documentation:
- Provide just-in-time privileged access to Azure AD and Azure resources
- Assign time-bound access to resources using start and end dates
- Require approval to activate privileged roles
- Enforce multi-factor authentication to activate any role
- Use justification to understand why users activate
- Get notifications when privileged roles are activated
- Conduct access reviews to ensure users still need roles
- Download audit history for internal or external audit
Leveraging the features above can allow any organization to better manage privileged access to Azure AD, Azure, and other Microsoft Online Services such as Microsoft 365 or Microsoft Intune.
Active vs Eligible Roles for Privileged Identity Management
With Azure Privileged Identity Management, there are two types of assignments that can be made to roles and they are:
- Eligible assignments require the member of the role to perform an action to use the role. Actions might include performing a multi-factor authentication (MFA) check, providing a business justification, or requesting approval from designated approvers.
- Active assignments don’t require the member to perform any action to use the role. Members assigned as active have the privileges assigned to the role at all times.
It is generally advised to use eligible as much as you can so you can avoid having an account that always has permissions. If an account needs to have the an active assignment for scenarios such as hiring a consultant for a full day of review, specify an active assignment with an assignment start and end date/time.
Licensing Requirements
The official Microsoft provided licensing requirements for using PIM can be found here:
License requirements to use Privileged Identity Management
To summarize, if you are strictly purchasing Azure AD Premium P2 licenses for PIM then you will only need as many employees that will be performing the following tasks:
- Users assigned as eligible to Azure AD or Azure roles managed using PIM
- Users who are assigned as eligible members or owners of privileged access groups
- Users able to approve or reject activation requests in PIM
- Users assigned to an access review
- Users who perform access reviews
Azure AD Premium P2 licenses are not required for the following tasks:
- No licenses are required for users who set up PIM, configure policies, receive alerts, and set up access reviews.
Examples of usage scenarios can be found here: https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/subscription-requirements#example-license-scenarios
The following is what happens with the license examples:
If an Azure AD Premium P2, EMS E5, or trial license expires, Privileged Identity Management features will no longer be available in the directory:
- Permanent role assignments to Azure AD roles will be unaffected.
- The Privileged Identity Management service in the Azure portal, as well as the Graph API cmdlets and PowerShell interfaces of Privileged Identity Management, will no longer be available for users to activate privileged roles, manage privileged access, or perform access reviews of privileged roles.
- Eligible role assignments of Azure AD roles will be removed, as users will no longer be able to activate privileged roles.
- Any ongoing access reviews of Azure AD roles will end, and Privileged Identity Management configuration settings will be removed.
- Privileged Identity Management will no longer send emails on role assignment changes.
Note that Azure AD Premium P2 also provides the Identity protection feature for accounts (https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/overview-identity-protection), which would enable the following:
- Vulnerabilities and risky accounts detection
- Risk events investigation
- Risk-based Conditional Access policies
If these features are designed for the organization then everyone will need to be licensed.
With an overview of PIM provided, I will proceed to demo each of the key features provided in the Microsoft documentation:
- Provide just-in-time privileged access to Azure AD and Azure resources
- Assign time-bound access to resources using start and end dates
- Require approval to activate privileged roles
- Enforce multi-factor authentication to activate any role
- Use justification to understand why users activate
- Get notifications when privileged roles are activated
- Conduct access reviews to ensure users still need roles
- Download audit history for internal or external audit
Deploy PIM
I find that many administrators typically skip through the Deploy PIM section of the Microsoft documentation (https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-deployment-plan) as the section does not actually contain any configuration instructions but I’d like to stress how important it is to read through all the items that Microsoft outlines to successfully plan for a PIM deployment. I would highly recommend going through the documentation before jumping into the next configuration section.
No more “Consent to PIM”
Those who have worked with PIM in the past or written the older AZ-500 exam may remember how administrators need to “consent to PIM” prior to using the feature. The process of consenting to PIM has been removed so there is no need to perform this step anymore and the console now has the following banner inserted into the Quick start page:
You are using the updated Privileged Identity Management experience for Azure AD roles.
The changes that Microsoft made as per the documentation https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-getting-started#prerequisites is as such:
When a user who is active in a privileged role in an Azure AD organization with a Premium P2 license goes to Roles and administrators in Azure AD and selects a role (or even just visits Privileged Identity Management):
- We automatically enable PIM for the organization
- Their experience is now that they can either assign a “regular” role assignment or an eligible role assignment
When PIM is enabled it doesn’t have any other effect on your organization that you need to worry about. It gives you additional assignment options such as active vs eligible with start and end time. PIM also enables you to define scope for role assignments using Administrative Units and custom roles. If you are a Global Administrator or Privileged Role Administrator, you might start getting a few additional emails like the PIM weekly digest. You might also see MS-PIM service principal in the audit log related to role assignment. This is an expected change that should have no effect on your workflow.
Start Using PIM with Wizard
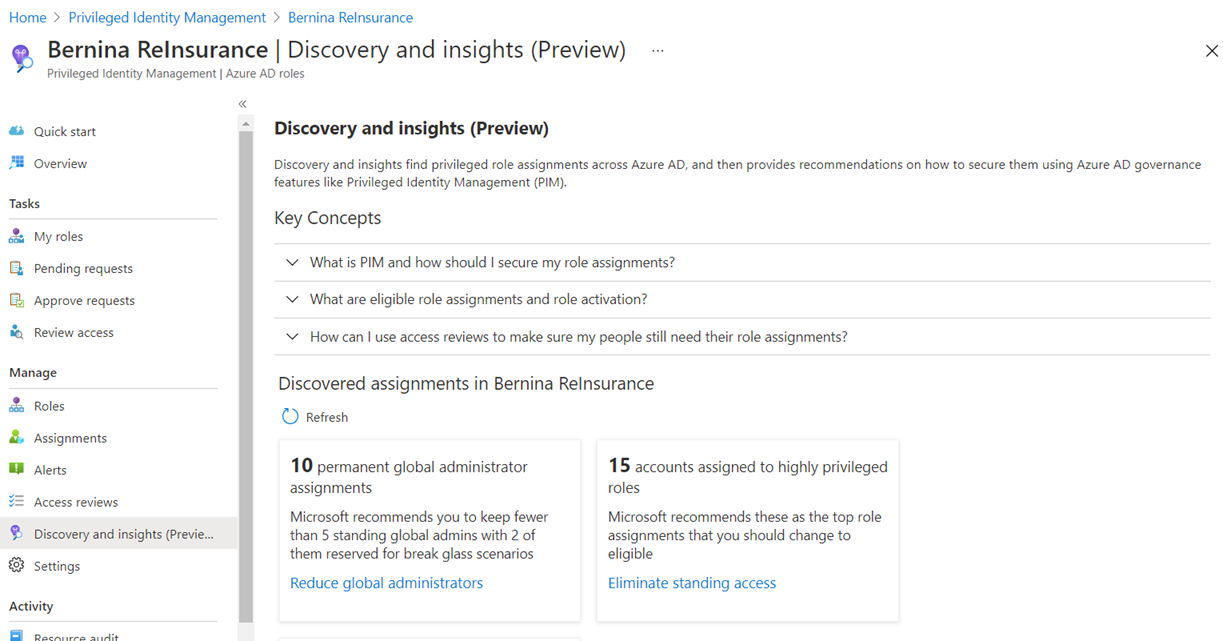
If you’re new to PIM and need to quickly start using the features with minimal configuration, using the security wizard (https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-security-wizard) would be a great start. The Discovery and insights (Preview) feature in the Privileged Identity Management blade provides the easy to use wizard to begin leveraging PIM features:
Configuring a PIM Administrator with an Active Assignment
If you already have a deployment plan created then our first step would be to assign the planned account to Privileged Role Administrator role for PIM administration. Navigate to Azure AD roles under Manage:
Then Roles and type in Privileged Role Administrator to list the PIM role, then select it:
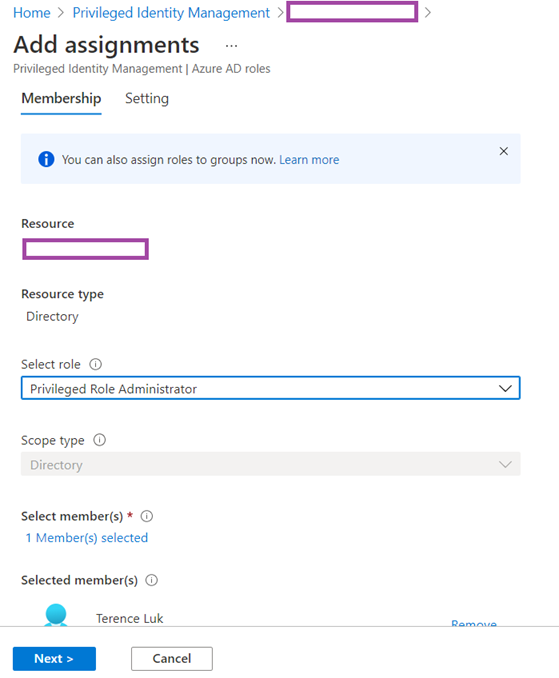
Once in the properties of the role, proceed to use the Add assignments button to add a user into the role. I will add my own account for the purpose of this example.
**Note that as of the time of writing this post, the Microsoft documentation dated on 08/06/2020 specifies that we should click on the Add Member button (https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-how-to-give-access-to-pim#delegate-access-to-manage-pim) but this button is no longer available on 4/3/2021.
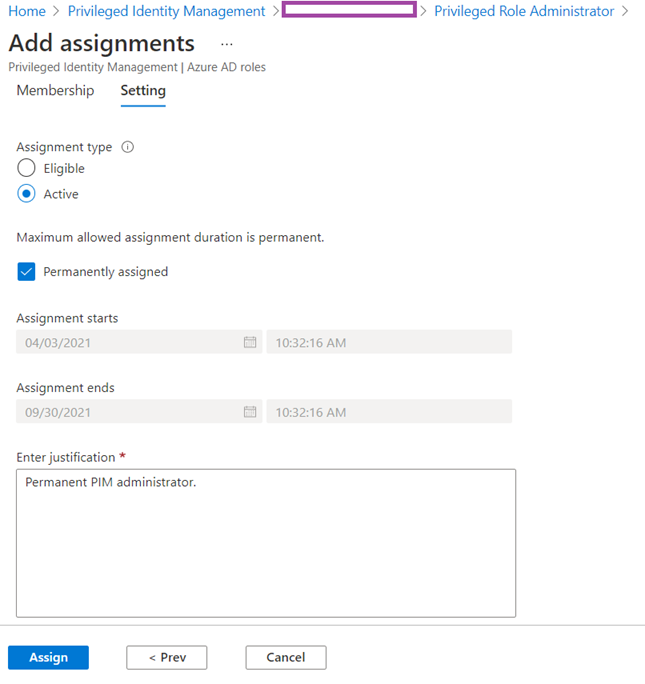
I will configure this assignment to be active and permanently assigned but note that it is generally advised that most active assignments should be configured with a start and end time/date if possible.
The account specified should now be displayed under the Active assignments tab:
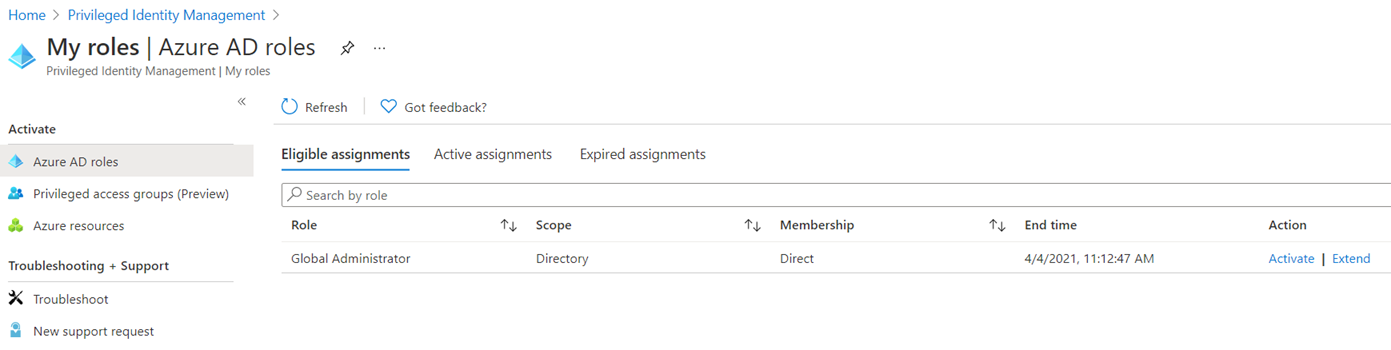
Navigating back to the Privileged Role Management page and selecting My roles:
Then under Azure AD roles and Active Assignments should display the roles I am currently a part of (Global Administrator and Privileged Role Administrator):
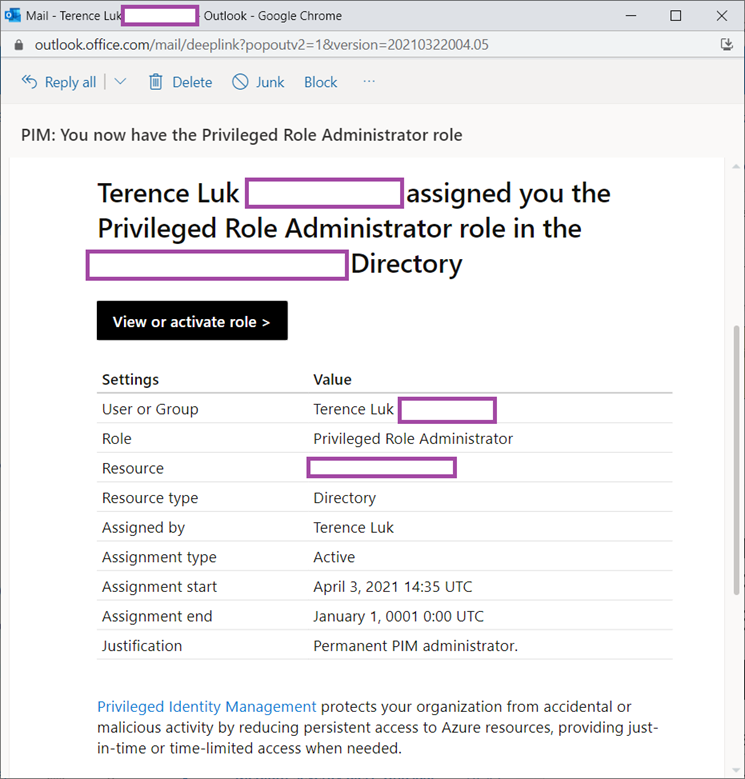
Note that the act of granting my account the Privileged Role Administrator role will send the following notification to my email address about the assignment.
Privileged Identity Management Alerts
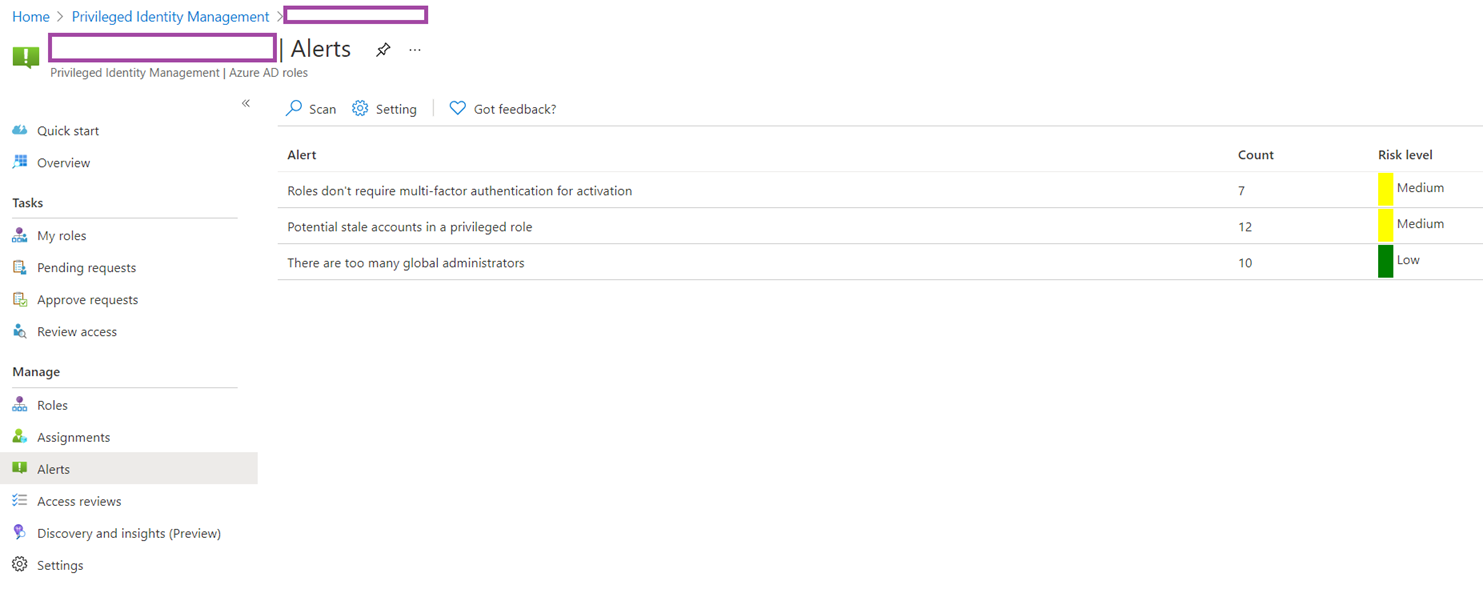
You can instantly view a list of issues as identified by PIM by clicking on the Alerts under the Manage settings:
Note the 3 alerts that are raised for this environment:
- Roles don’t require multi-factor authentication for activation
- Potential stale accounts in a privileged role
- There are too many global administrators
The first two are fairly obvious while the second one lists accounts that have not changed their password in the past 90 days and clicking into the line item will bring up the details:
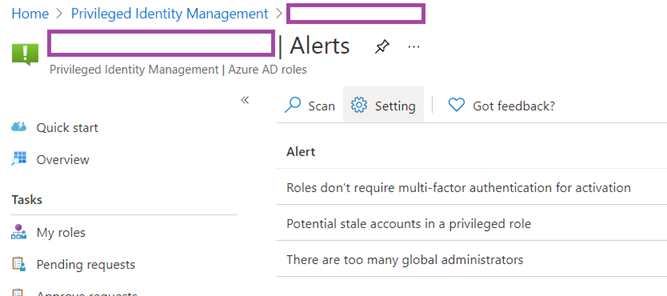
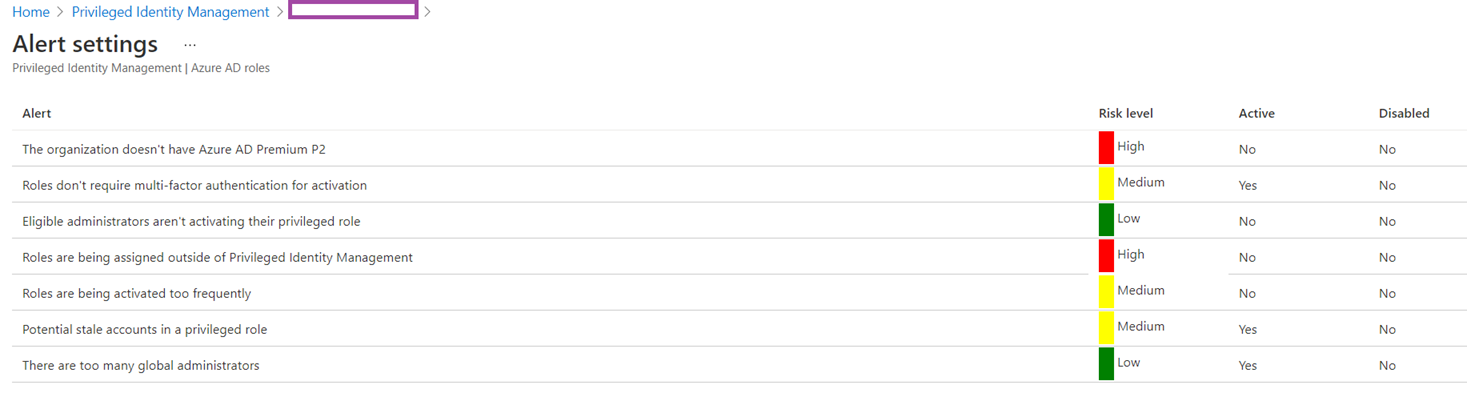
Clicking on the Settings button will bring us into configuration set for identifying these risks:
You can click on each of the alerts to see what configuration changes you can make as well as whether to disable them:
Assigning a User with Eligible Role (J.I.T)
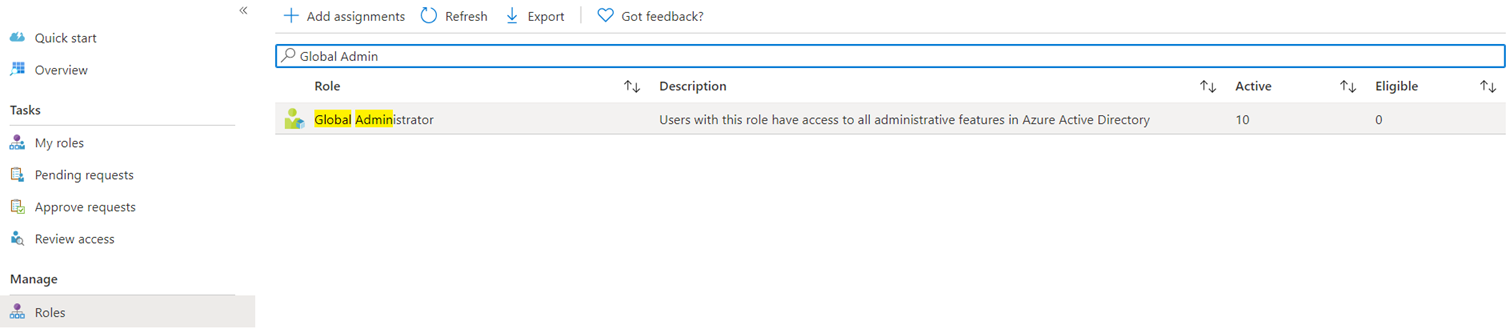
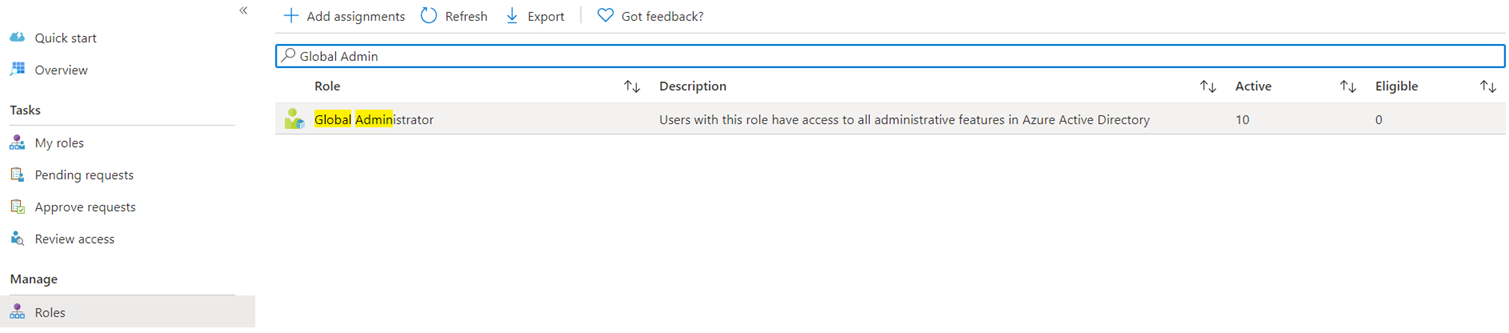
With the initial configuration and walk through of the alerts out of the way, let’s proceed to assigning a user with the eligible role for the Global Admin role. Begin by navigating to Azure AD roles under Manage:
Then Roles and type in Global Admins to list the PIM role, then select it:
Click on Add assignments:
I’ll be using a account named John Smith as the example:
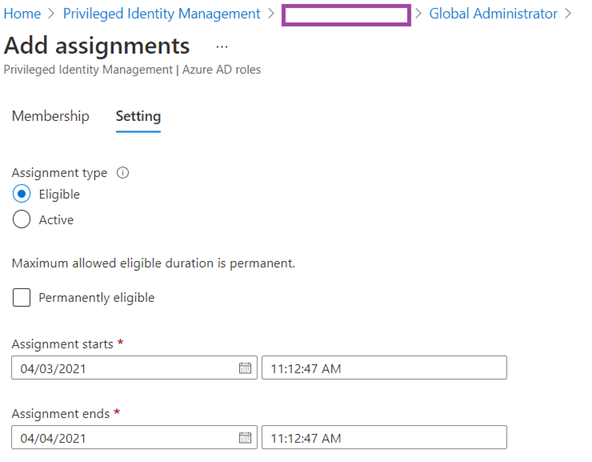
In the Setting tab, we will configure the Assignment type as Eligible with Permanently eligible disabled and a Assignment starts and Assignment ends date/time specified to be one day:
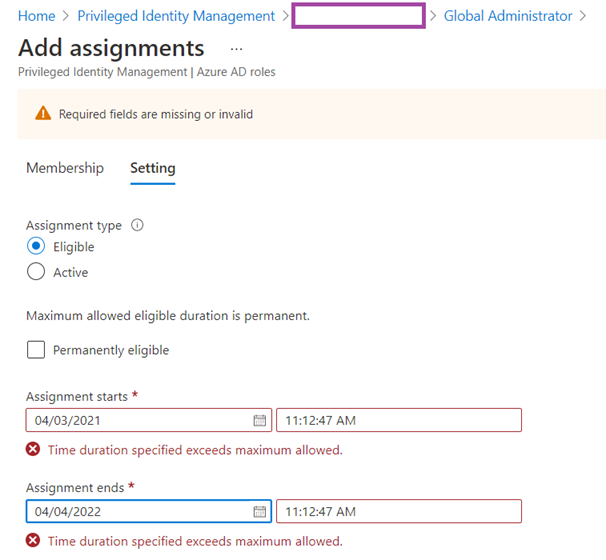
Note that the Assignment starts and Assignment ends date/time cannot exceed more than a year or the message Time duration specified exceeds maximum allowed. will be displayed:
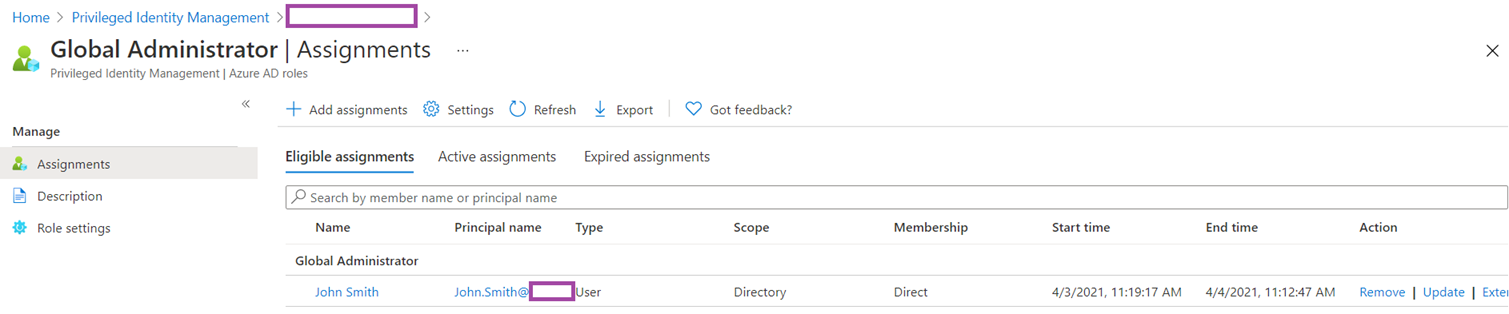
The role assignment should now be displayed under the Eligible assignments tab:
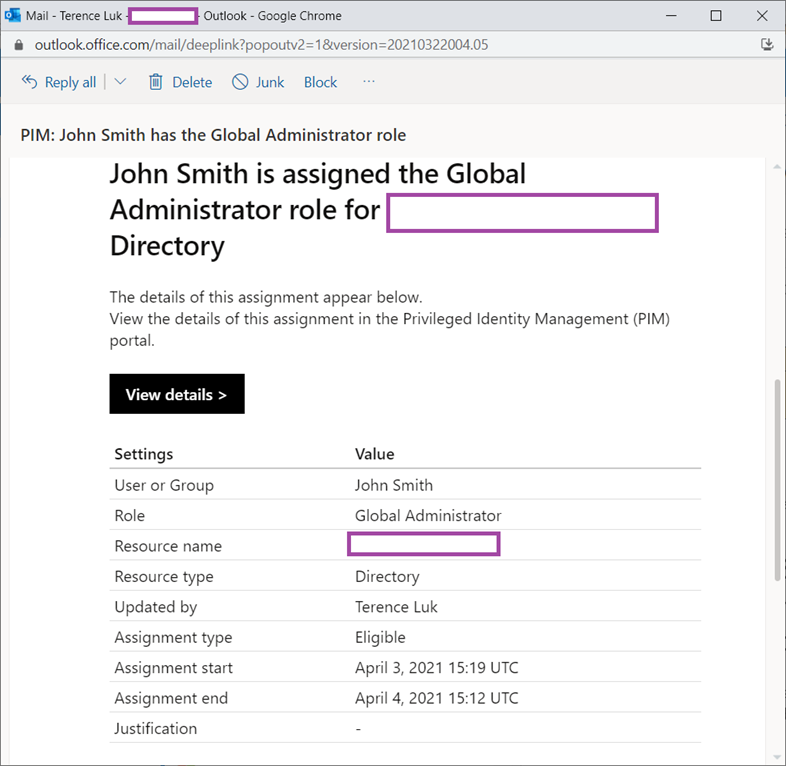
Note that upon completion of assignment John Smith the eligible role, notification emails such as the one below would have been sent to the admins.
Testing a User with Eligible Role
With the eligible role assigned to John Smith, we can log into the Azure portal and confirm that he does not have the ability to create new users or reset passwords as he is eligible but not a Global Admin yet:
We can then navigate to the Privileged Identity Management section, click on Azure AD roles under Activate, then see that we can eligible for the Global Administrator role with the option of activating it:
**Note that there is an end time for this eligible assignment as how it was configured in the previous section.
We’ll notice that attempting to activate the role indicates we are prompted with:
Additional verification required. Click to continue
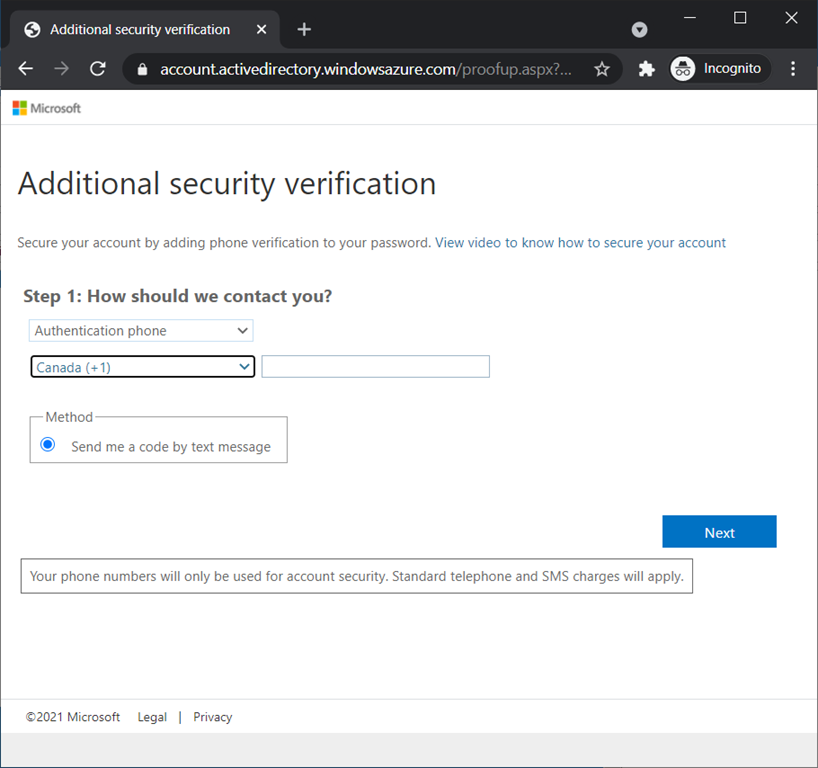
The reason why this prompt is displayed is because this account does not have MFA set up and the default settings for activation is to have MFA setup, which I will show a bit later.
Proceed to set up MFA:
Once MFA is successfully set up, the following activation options will be displayed. Note how there are various parameters we can configure such as the activation start time, the duration, and a reason, which is required for activation:
For the purpose of this example, I will set the duration to only 2 hours mimicking the scenario that I only need 2 hours of elevated permissions. My reason for the activation will be to: Test Global Admin activation.
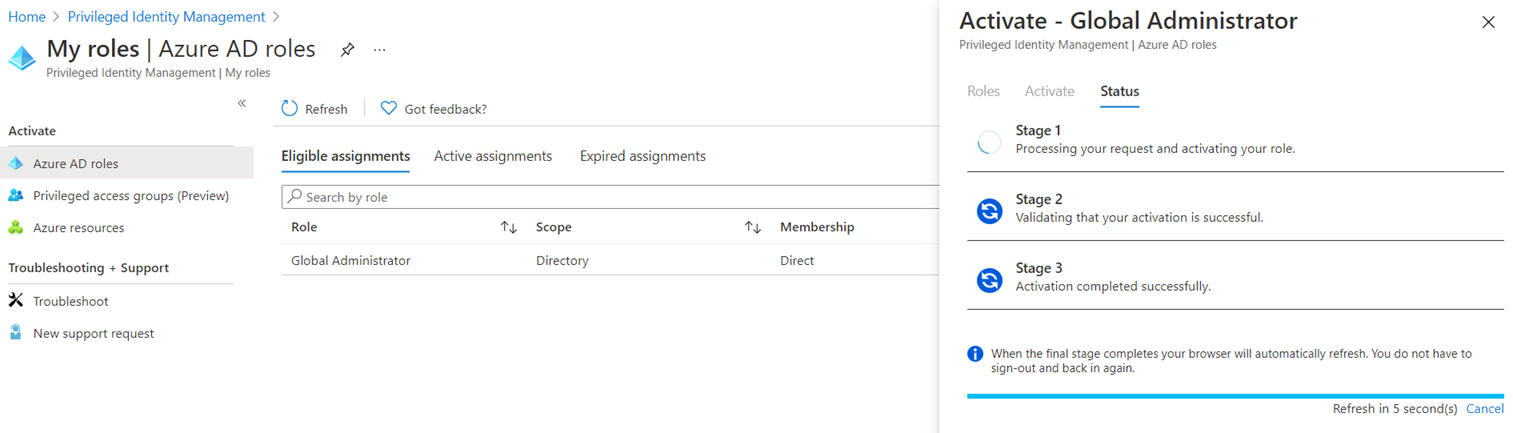
The activation proceeds through 3 stages and will complete fairly quickly (you don’t need to walk away from the computer):
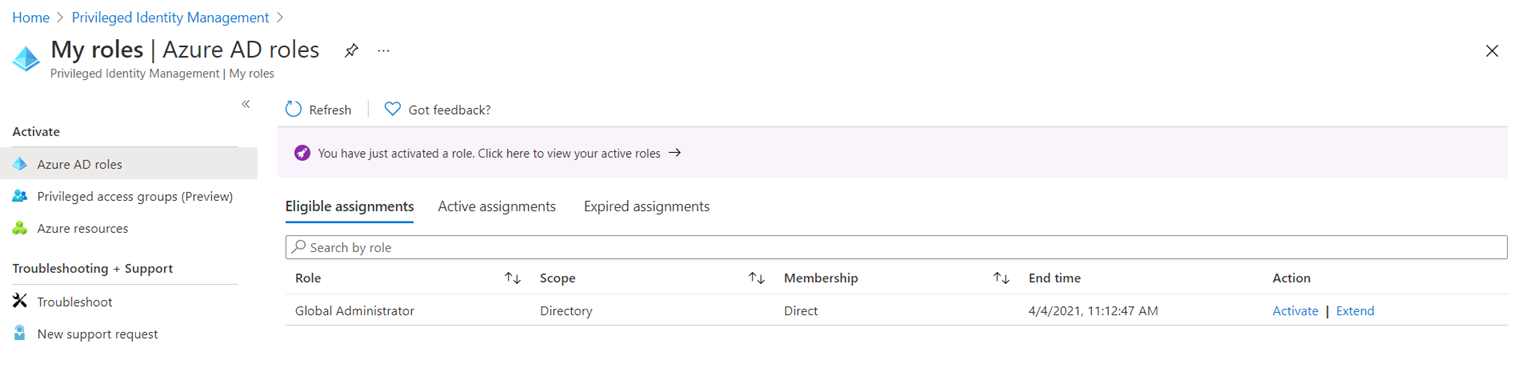
Upon completion of activation, the Eligible assignments tab will refresh and display the following message:
You have just activated a role. Click here to view your active roles
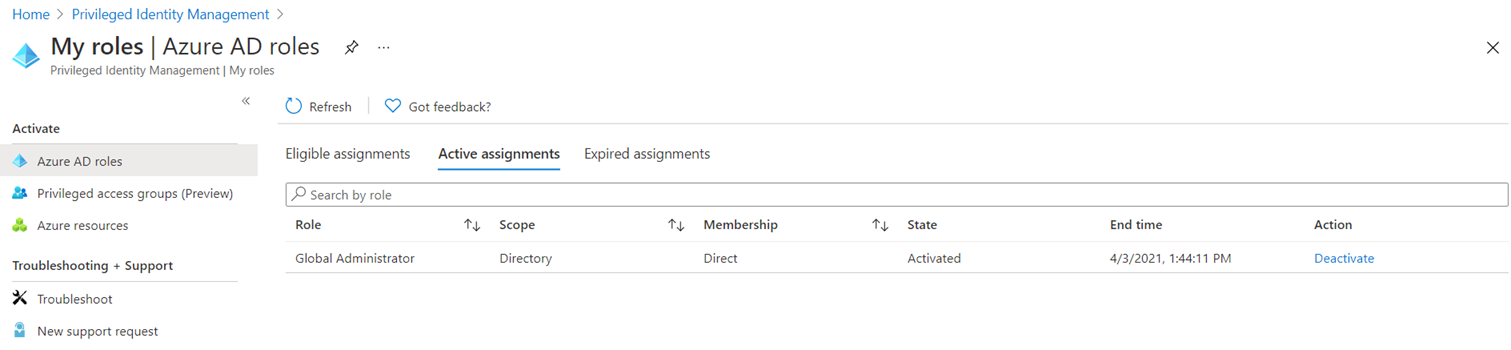
Clicking the Click here to view your active roles will change the table to Active assignments which will display the activated state. Note the End time listed is 2 hours from when I activated it:
The test John Smith user will now be able to create accounts:
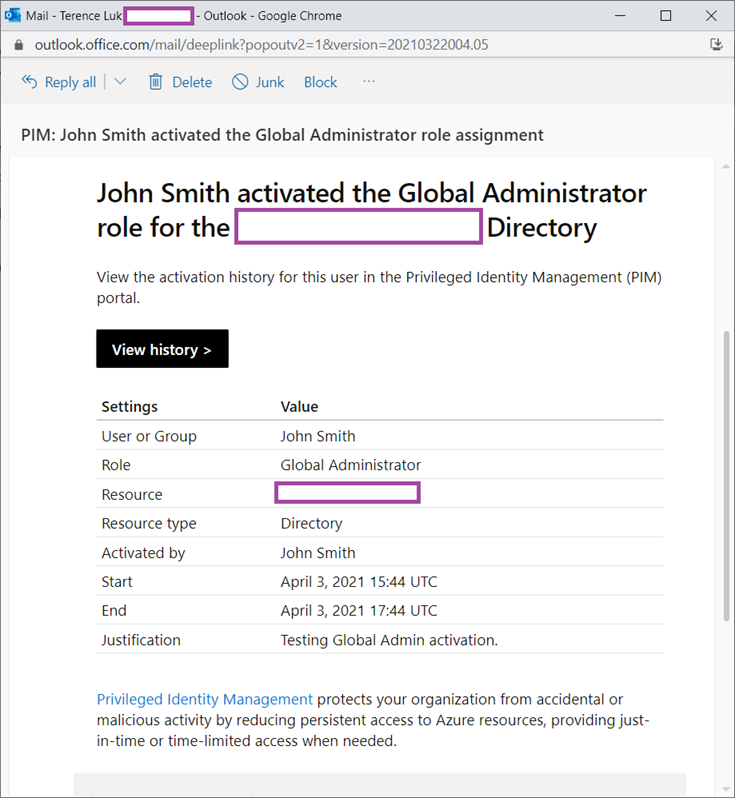
Upon activating the Global Admin assignment, notification emails such as the one below would have been sent to the admins:
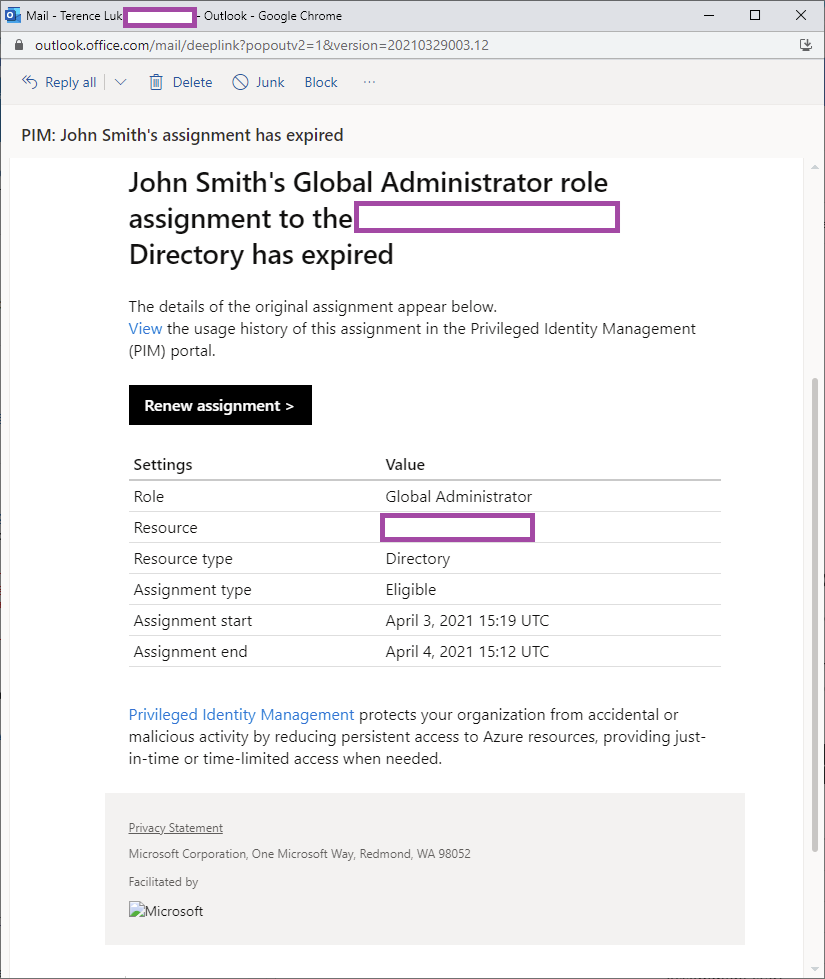
When the duration has expired an email will be sent:
Activation Role Settings Configuration
It is possible to customize the activation role settings as demonstrated in the previous activation by navigating to Azure AD roles under Manage:
Roles and type in Global Admins to list the PIM role, then select it:
Click on Role settings to list the parameters that we can edit:
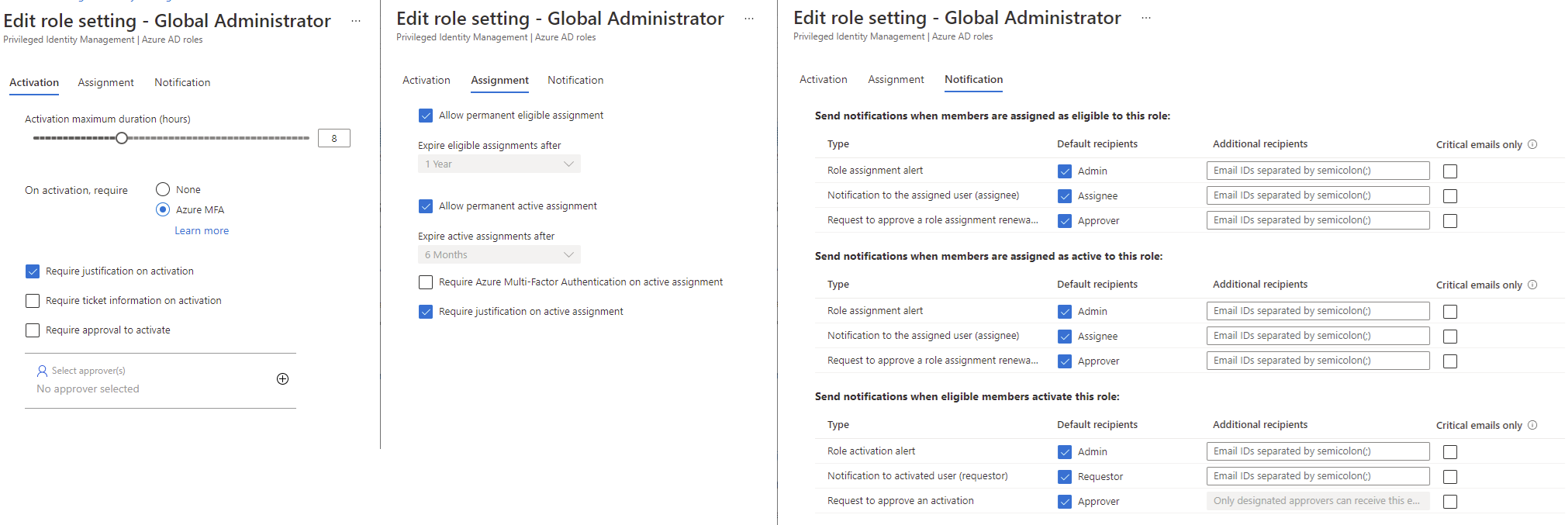
The configuration settings are partitioned into tabs, which I have combined into one screenshot.
The Activation tab allows us to:
- Change the activation maximum duration in hours, which defaults to 8 and is customizable during the activation process
- Requires the account to have MFA setup – why John Smith had to set up MFA
- Require a justification – why we had to enter a reason
- Require ticket information on activation – this will provide two fields – 1. ticket number, 2. ticketing system link
- Require approval to activate – One of the features I enjoy most as this will require another administrator to interactively approve the activation from the Azure portal
The Assignment tab allows us to:
- Allow permanent eligible assignment – this can be changed to limit the amount of time an eligible assignment can be
- Allow permanent active assignments after – this enables or disables permanent active assignment and if it is disabled, the active assignment can be force to expire after a period of time (1 year, 6 months, 3m months, 1 month, 15 days)
- Require Azure MFA on active assignment – this will force MFA for active assignments
- Require justification on active assignment – forces a reason to be entered
The Notification tab allows us to specify various notification settings for when activation or assignments take place.
These configuration settings are set independently for each role.
PIM Auditing
To perform an audit of on the activities of privileged accounts, navigate to Azure AD roles under Manage:
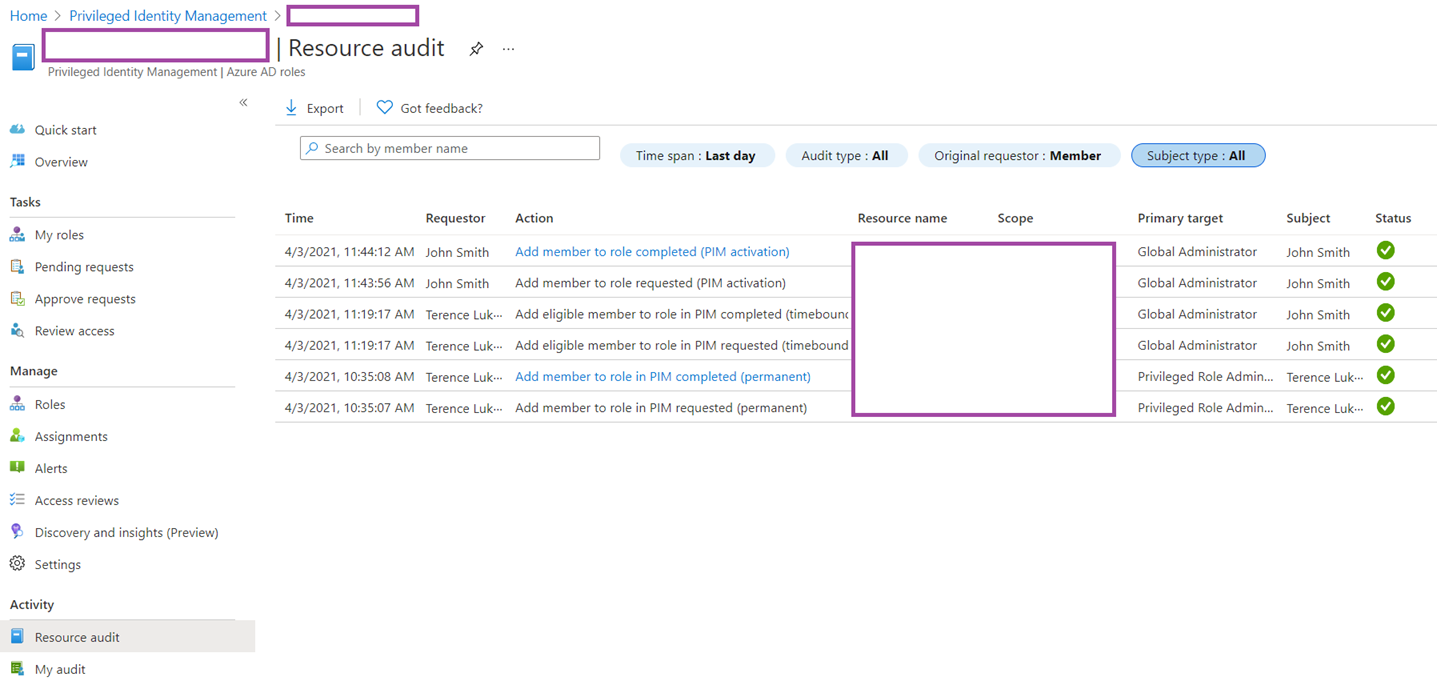
Select Resource Audit under Activity and you will see the actions of PIM administrators as well as users who have activated their eligibility for configured roles:
Clicking on a line item will bring the details of the action:
Navigating to the My audit section will display all the PIM activities the account logged in has made:
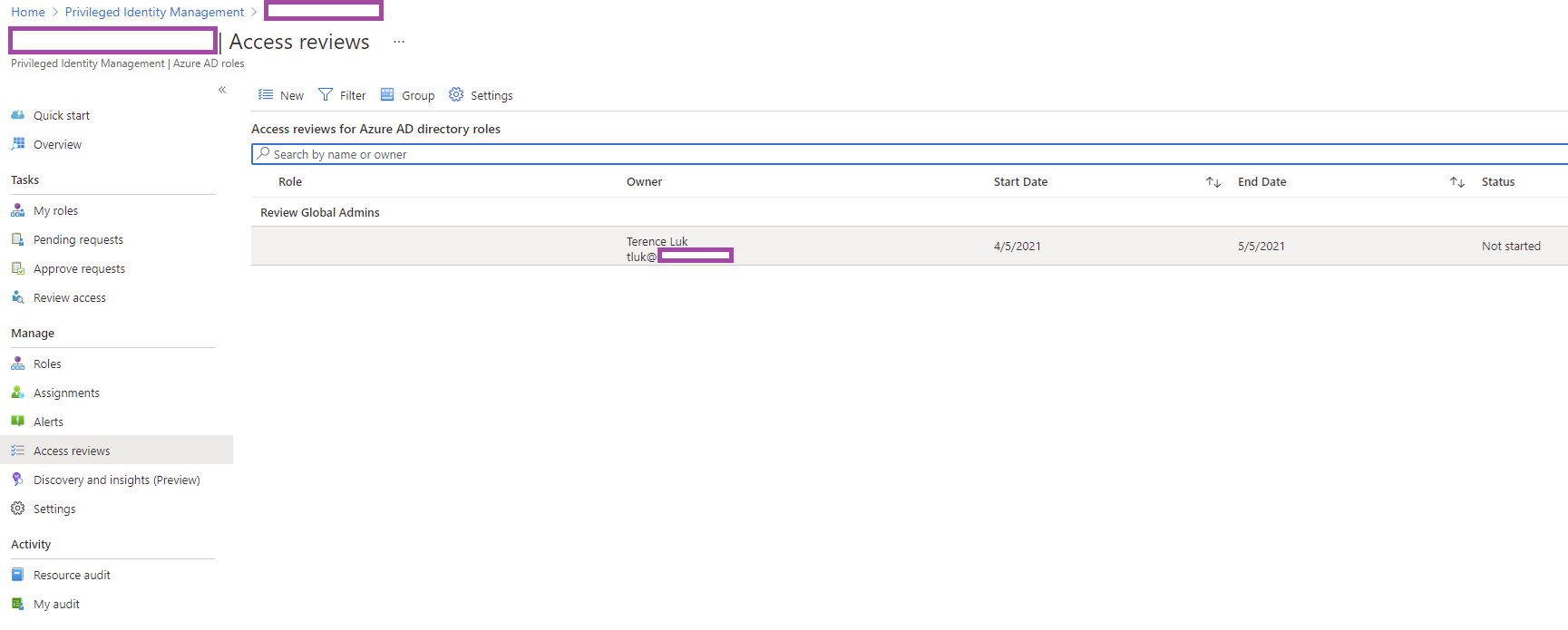
Creating an Access Review
You can create an access review to list the specific PIM activities of a role such Global Admin by navigating to Azure AD roles under Manage:
Then Access reviews and select New:
Then configure the review as required:
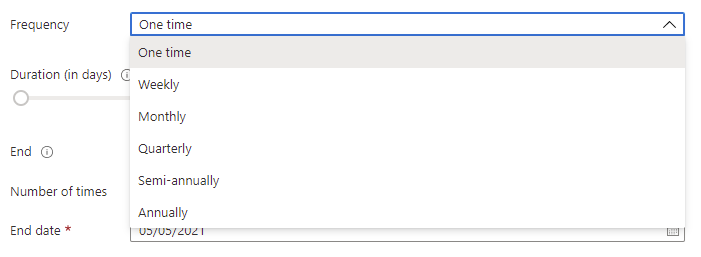
The frequency can be set to the following:
Note the Upon completion settings and Advanced settings that are available:
A review will be created in the Access reviews:
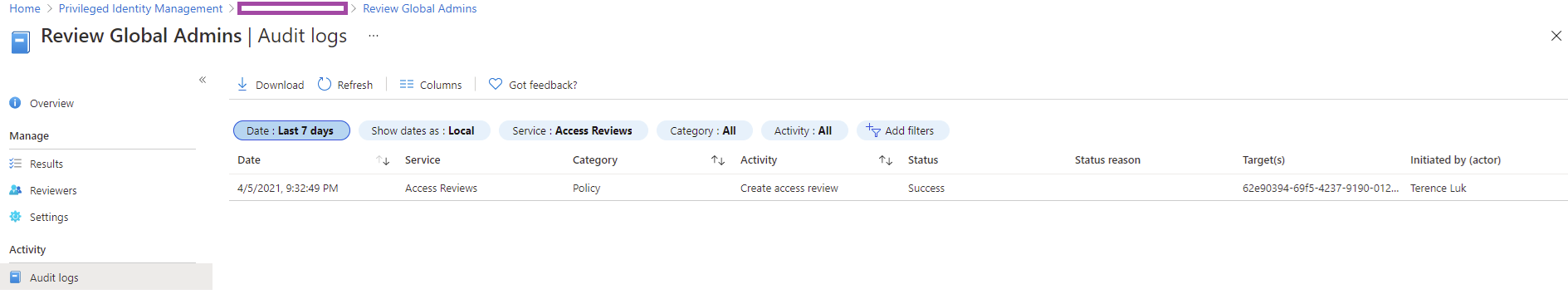
Clicking into the report will provide information about the PIM activity for Global Admins:
Hope this gives anyone looking for information about PIM an overview and demonstration of what it has to offer.

































One Response
Such detail is hard to come by. Crystal clear explanation ,flow and concepts.