Many large organizations prefer to manage their own certificates rather than using Azure’s Managed certificates feature, which allows the certificate to be purchased through and managed by Microsoft directly. Importing a certificate PFX file with the certificate’s private key into a Key Vault and granting permissions to an App Service’s managed identity would likely be what most administrators would attempt but many will find that this does not function as expected.
The official Microsoft document for granting access to Key Vault with Azure RBAC can be found here:
Provide access to Key Vault keys, certificates, and secrets with an Azure role-based access control
https://learn.microsoft.com/en-us/azure/key-vault/general/rbac-guide?tabs=azure-cli
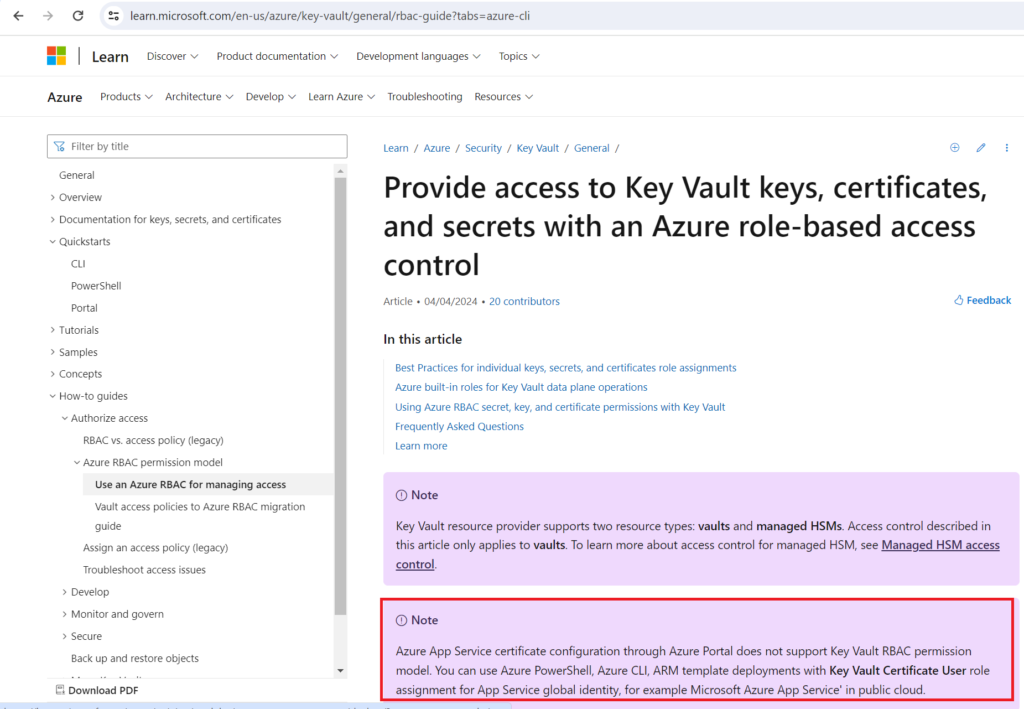
The note included at the beginning of this document indicates the following:
Azure App Service certificate configuration through Azure Portal does not support Key Vault RBAC permission model. You can use Azure PowerShell, Azure CLI, ARM template deployments with Key Vault Certificate User role assignment for App Service global identity, for example Microsoft Azure App Service’ in public cloud.
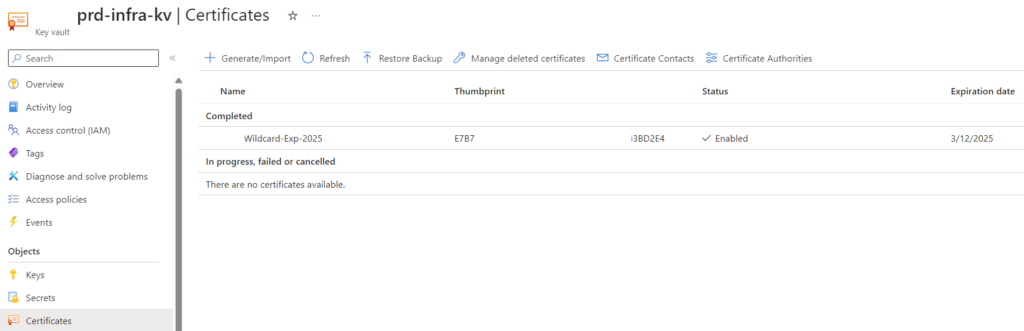
What this basically means is that if you simply import the certificate into Key Vault:
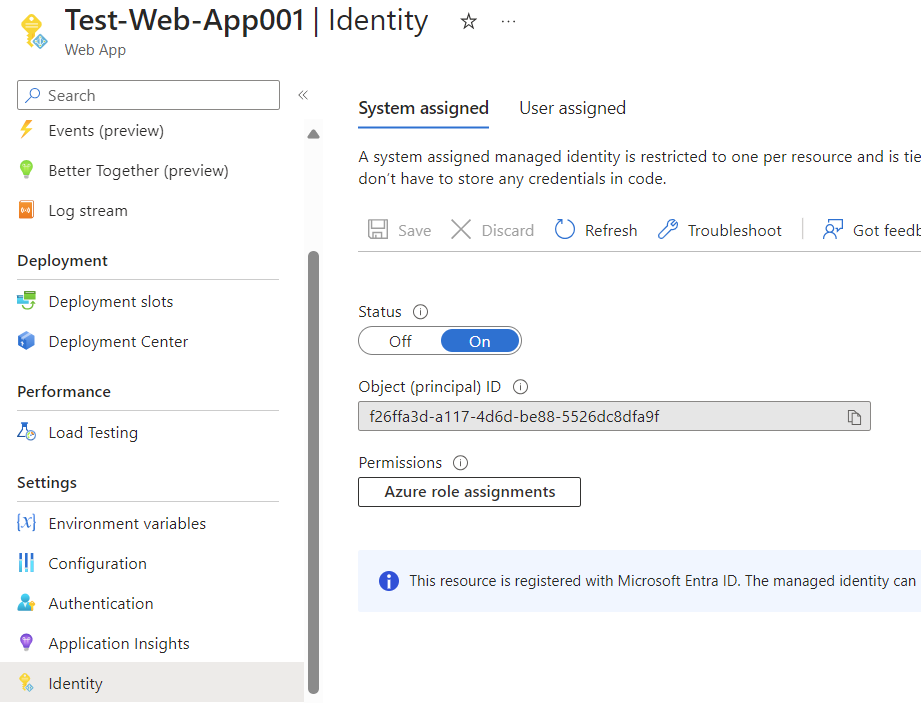
Turn on the managed identity for the App Service:
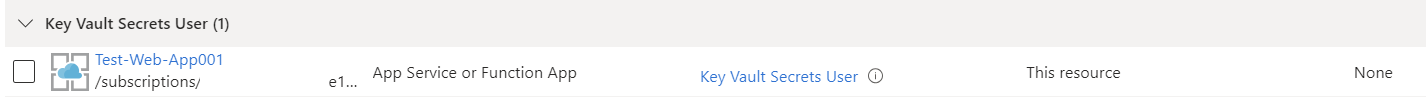
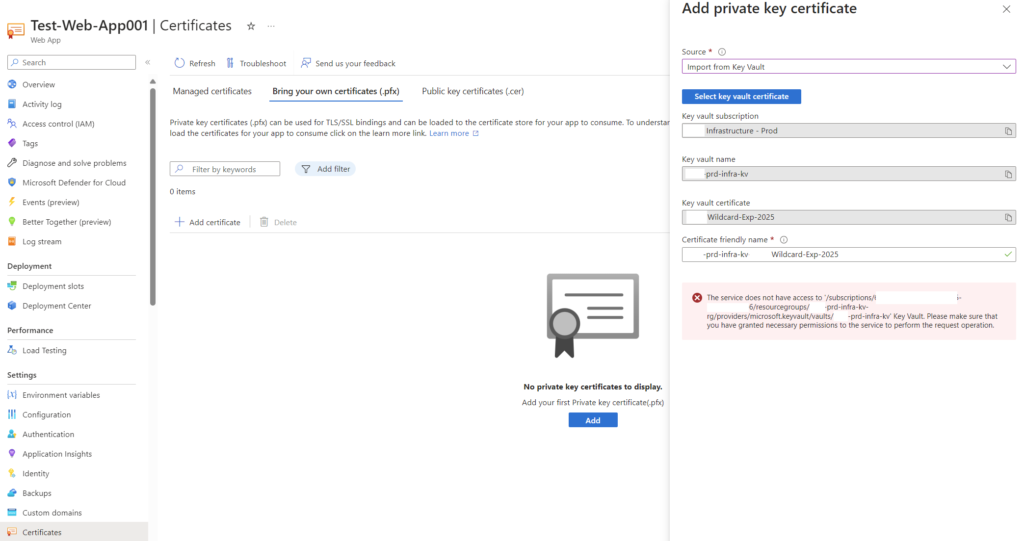
Attempting to assign the identity permission to the Key Vault, you will not be able to access the certificate:
The following is the error you will receive:
The service does not have access to ‘/subscriptions/xxxxxxxxxxxx-xxxx-xxxx-xxxxxxxxxxxxx/resourcegroups/prd-infra-kv-rg/providers/microsoft.keyvault/vaults/prd-infra-kv’ Key Vault. Please make sure that you have granted necessary permissions to the service to perform the request operation.
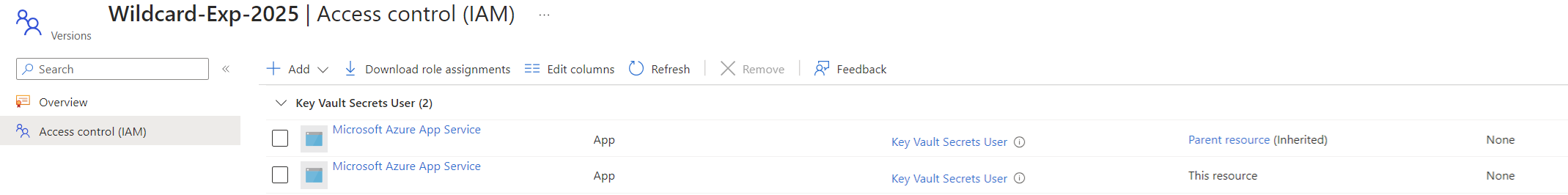
From the research I’ve done and as per the Microsoft document, it appears there isn’t a way to directly assign the App Service managed identity to the Key Vault. The only way to grant permissions to the App Service is to grant the tenant’s App Service global identity. This may create security concerns because if we grant the global identity representing App Services, then any App Service can reach into the Key Vault to retrieve keys, secrets, or certificates depending on the RBAC role granted. The only other option to reduce the amount of permissions the global identity is granted is rather than scoping the permissions to the whole Key Vault, we can scope it to the single secret, key or certificate. If these two options are not allowed in the organization then a manual import of the PFX directly into the App Service would be required. With that, let’s look at how we can configure this with PowerShell as you cannot configure this through the Azure Portal.
The first component we’ll need is the application ID that represents all App Services. This unique ID is the following: abfa0a7c-a6b6-4736-8310-5855508787cd
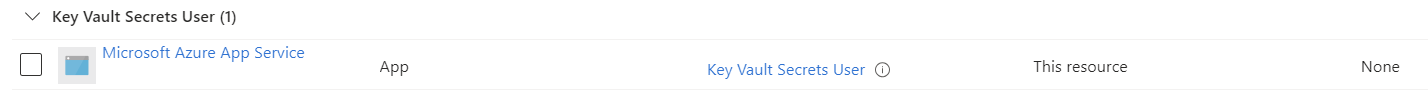
You can confirm this by searching for the application ID and find the service principal in the Enterprise Applications:
Scoping for the entire Key Vault
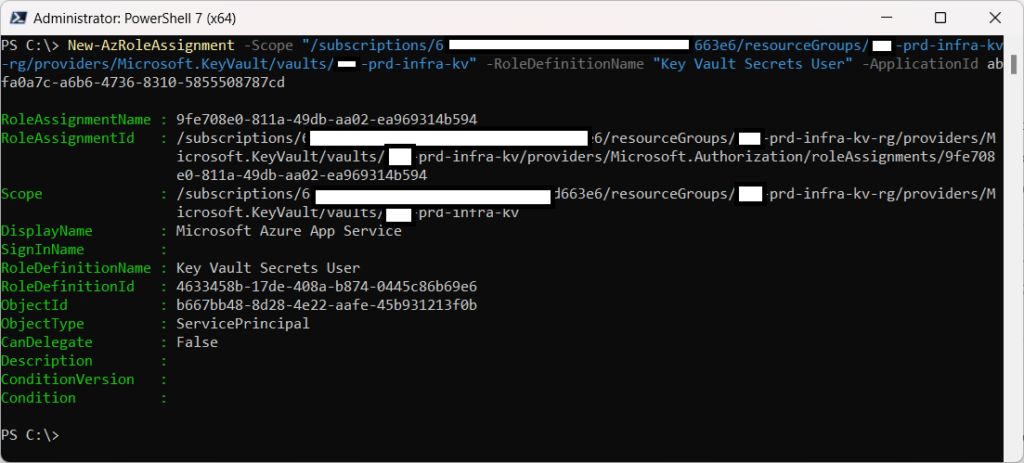
The following is the PowerShell cmdlet to use if you want to grant permissions to the App Service over the entire Key Vault:
Connect-AzAccount
Set-AzContext -Subscription xxxxxxxxxxxx-xxxx-xxxx-xxxxxxxxxxxxx
New-AzRoleAssignment -Scope “/subscriptions/xxxxxxxxxxxx-xxxx-xxxx-xxxxxxxxxxxxx/resourceGroups/prd-infra-kv-rg/providers/Microsoft.KeyVault/vaults/prd-infra-kv” -RoleDefinitionName “Key Vault Secrets User” -ApplicationId abfa0a7c-a6b6-4736-8310-5855508787cd
Scoping for the precise item in Key Vault
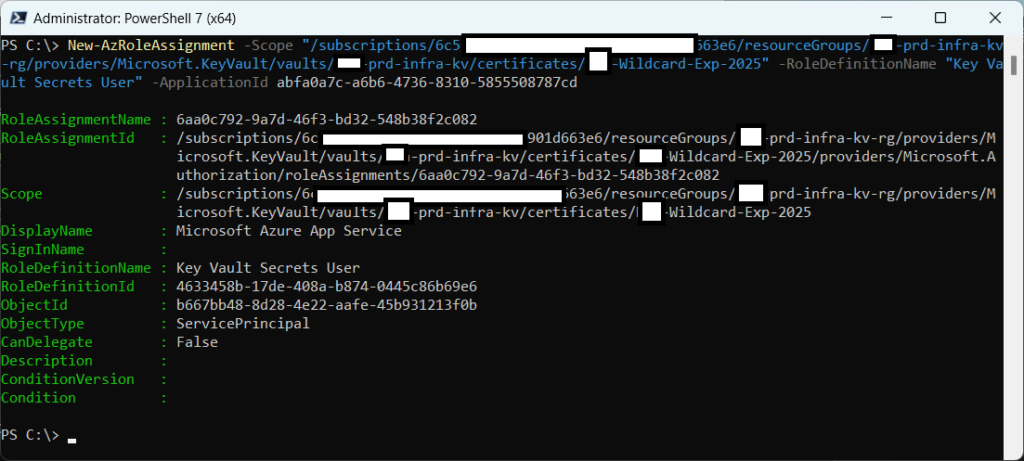
Use the following cmdlet to scope specifically to, say, a certificate:
New-AzRoleAssignment -Scope “/subscriptions/xxxxxxxxxxxx-xxxx-xxxx-xxxxxxxxxxxxx/resourceGroups/prd-infra-kv-rg/providers/Microsoft.KeyVault/vaults/prd-infra-kv/certificates/<certificate name>” -RoleDefinitionName “Key Vault Secrets User” -ApplicationId abfa0a7c-a6b6-4736-8310-5855508787cd
Note the direct assignment to the certificate:
Hope this helps anyone who may be looking for a walk through of this process.