One of the items I had on my to-do list was to create material that I could use to walk my colleagues through how our CSP tenant relates to our customers’ tenants and one of examples I wanted to include in the material was how to grant our CSP foreign principal permissions to a customer’s subscription as describe in my previous post:
Granting a CSP Foreign Principal the Reader or Owner role onto an Azure Subscription with PowerShell
https://blog.terenceluk.com/granting-csp-foreign-principal-reader/
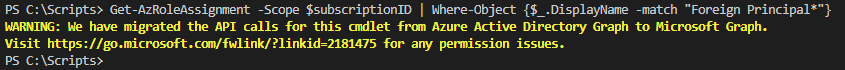
What I quickly noticed while testing the script was that it no longer worked today (May 2022) because the DisplayName for the CSP foreign principal provided by the output was now blank. What this means is that my script, which looks for a entries where the DisplayName matches Foreign Principal*, will now return zero records:
*Note that the warning (https://docs.microsoft.com/en-us/powershell/azure/troubleshooting?view=azps-7.5.0#get-azadgroupmember-doesnt-return-service-principals) is referring to a problem where service principals are not returned by Get-AzAdGroupMember and does not appear to affect the role assignments we’re looking for.
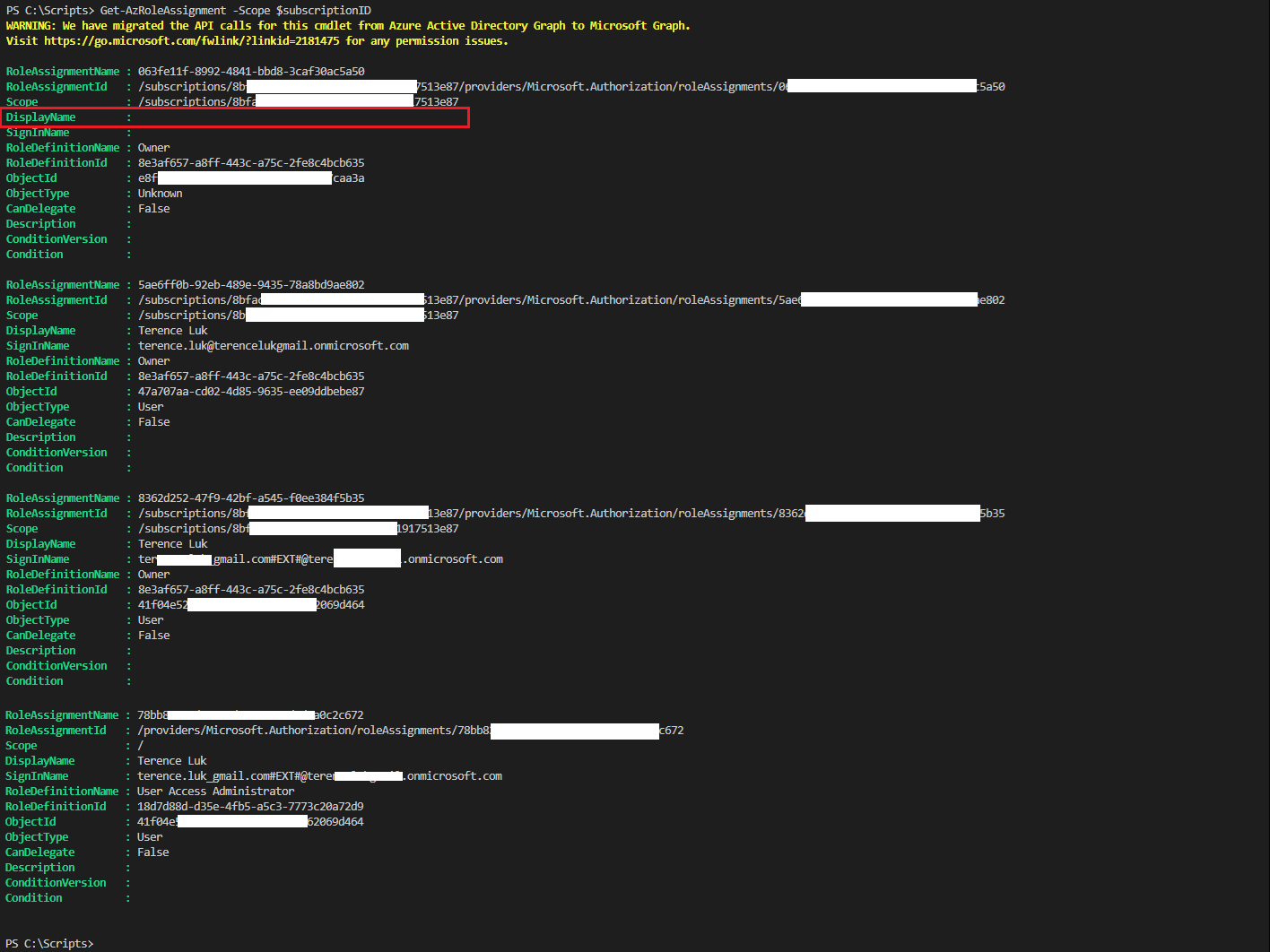
If I remove the filter, it will return the CSP foreign principal with a blank DisplayName as shown in the following screenshot:
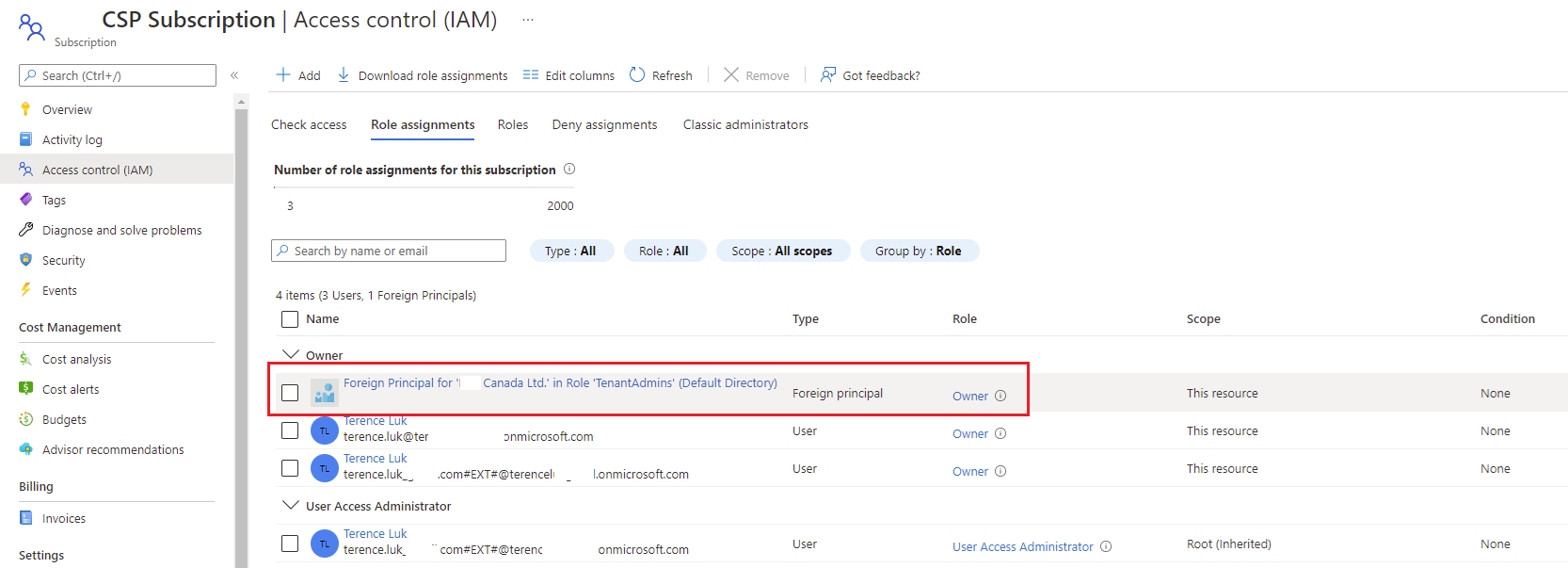
For reference, here is a screenshot of the foreign principal as displayed as a Azure RBAC role in the Access control (IAM) blade:
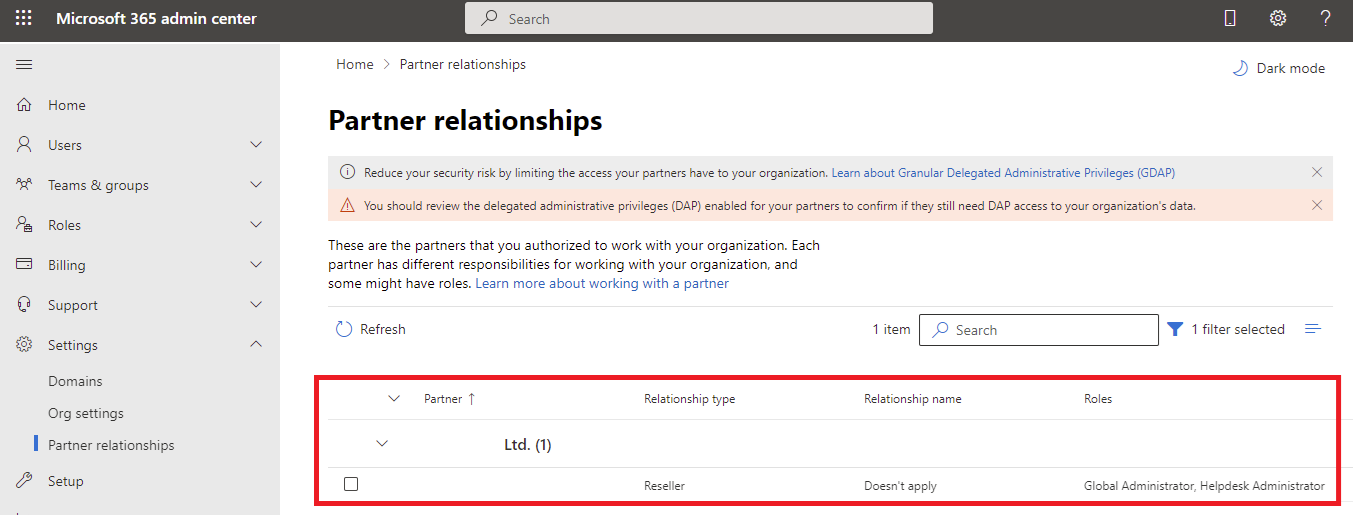
Here is a screenshot in the Microsoft 365 admin center portal of the foreign principal:
I’ve checked three tenants to confirm this is the same across them but since I’m not sure if this is temporary, I will leave the previous post as is with the script unchanged and will provide the updated set of cmdlets in this post that will be focused on discussing the roles from the CSP tenant, how it maps to the tenant’s Azure AD, and how they are used to grant permissions to a customer’s tenant.
Before I begin, the following post provides great information about the CSP identity and rights management even though it is very old: https://docs.microsoft.com/en-us/archive/blogs/hybridcloudbp/identity-and-rights-management-in-csp-model. I highly encourage anyone learning about the CSP program to go through the blog entry.
The Microsoft Partner Center Portal
Those who have worked at a Microsoft partner would be familiar with the partner portal located at: https://partner.microsoft.com where they can sign in by clicking on the Partner Center link:
Microsoft’s CSP program currently supports three main types of transactional relationships:
- Indirect providers
- Indirect resellers
- Direct-bill partners
More information can be found at the following Microsoft documentation: https://docs.microsoft.com/en-us/partner-center/csp-supported-partner-relationships#types-of-partner-relationships-in-the-csp-program
Depending on the type of relationship you’ll be presented with different navigation menus depending on the type of partner and membership (left is the Direct-bill while the right is a Indirect reseller):
For the purpose of this post, we will focus on the Direct-bill partners (Tier 1) who are able to directly provision Azure CSP subscriptions to their customers and are required to use their identity (CSP Provider) to open tickets because customers would no longer be able to from within portal.azure.com.
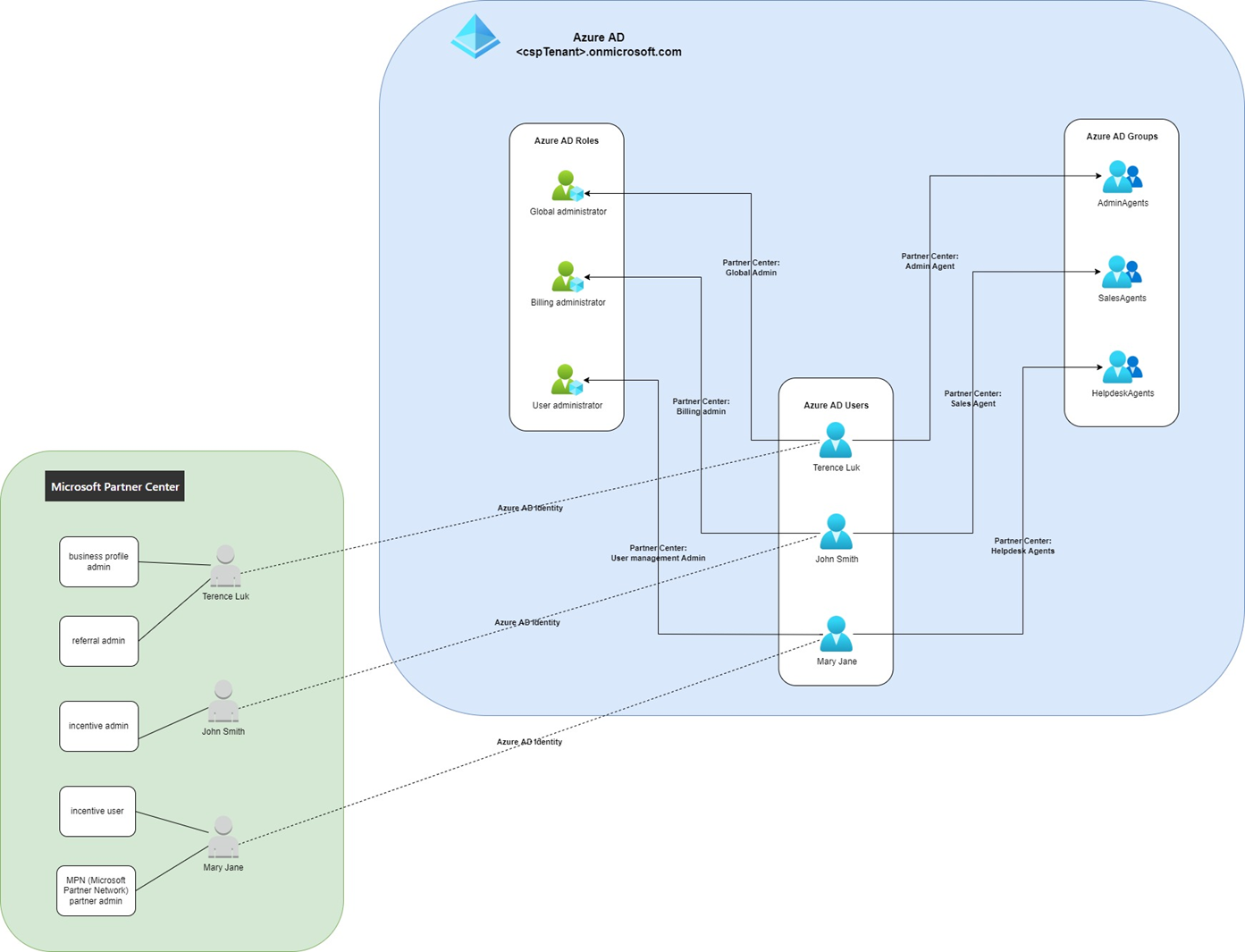
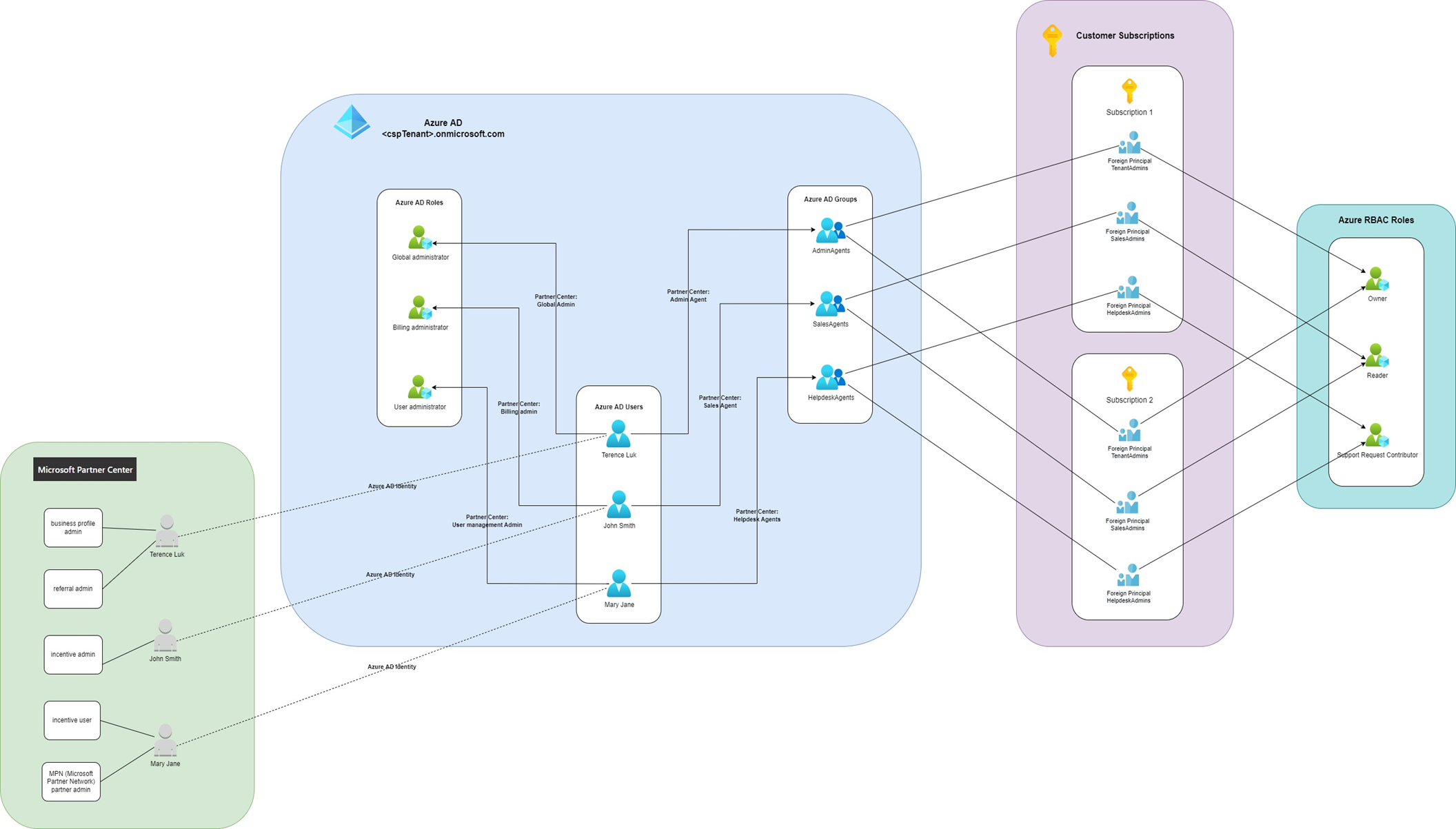
CSP Program User, Roles, Groups and how they relate to Azure AD
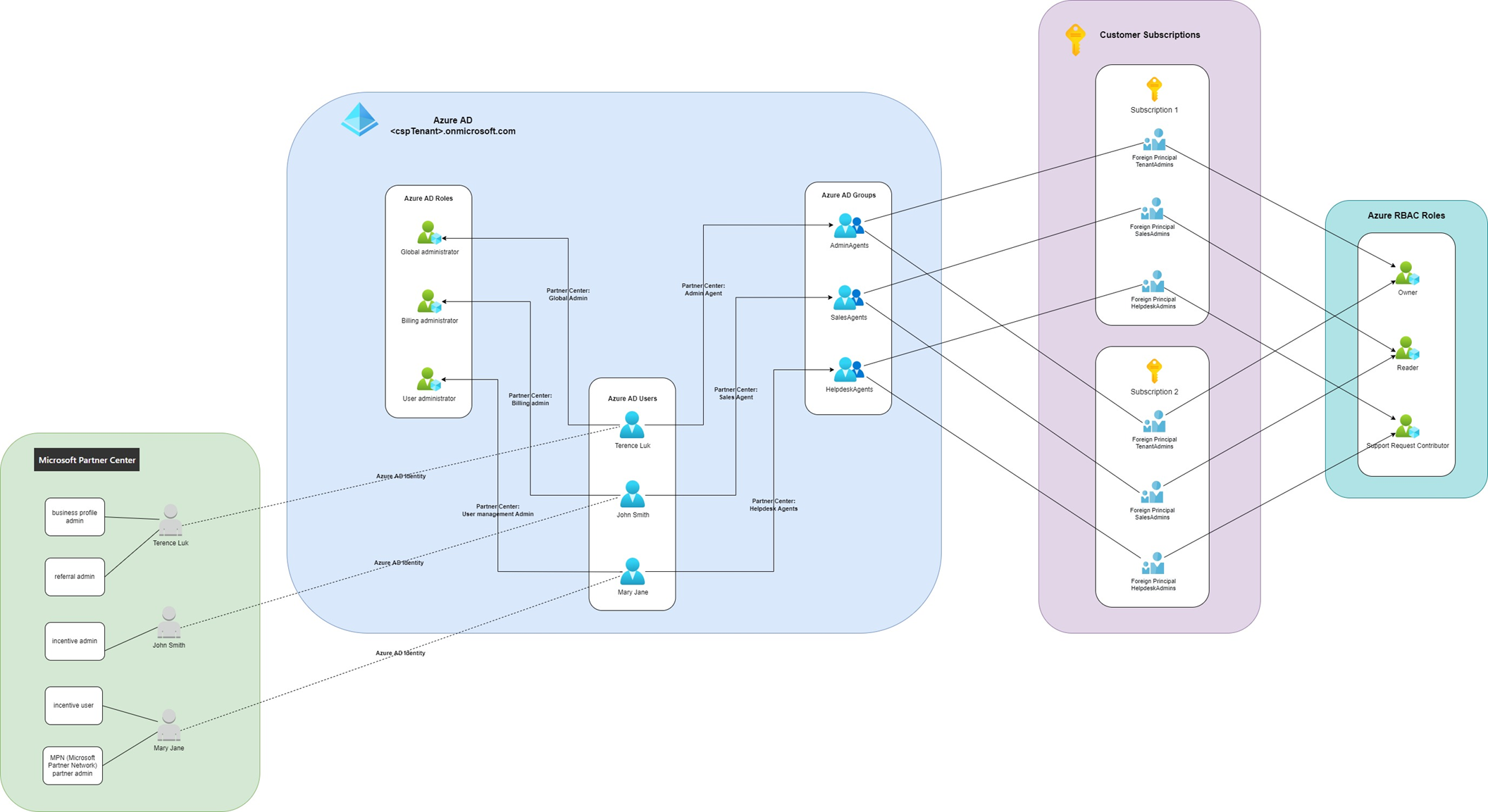
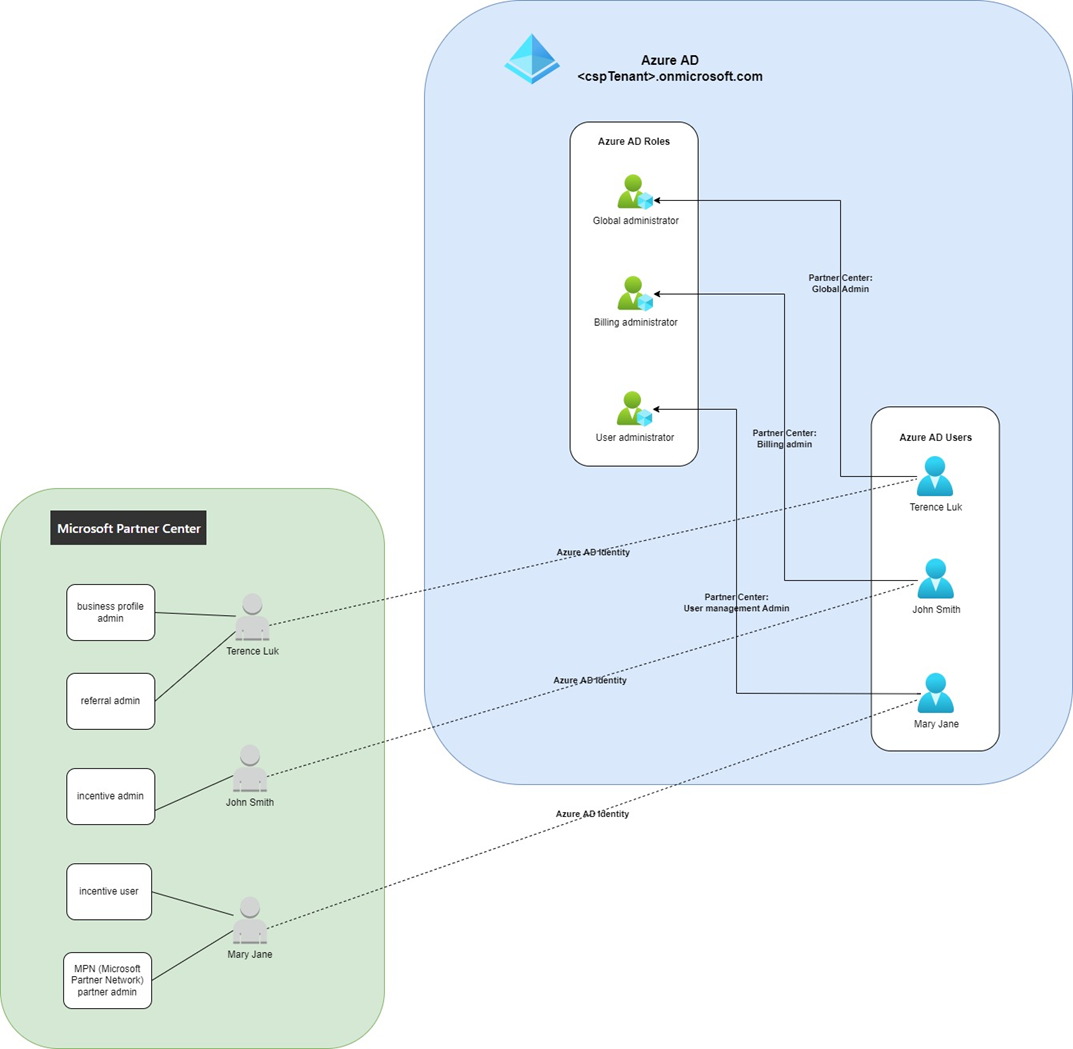
The following is a diagram I mapped out of how the CSP program users and roles relate to the Azure AD:
Let’s break down the diagram by mapping the various components out in the Partner Center.
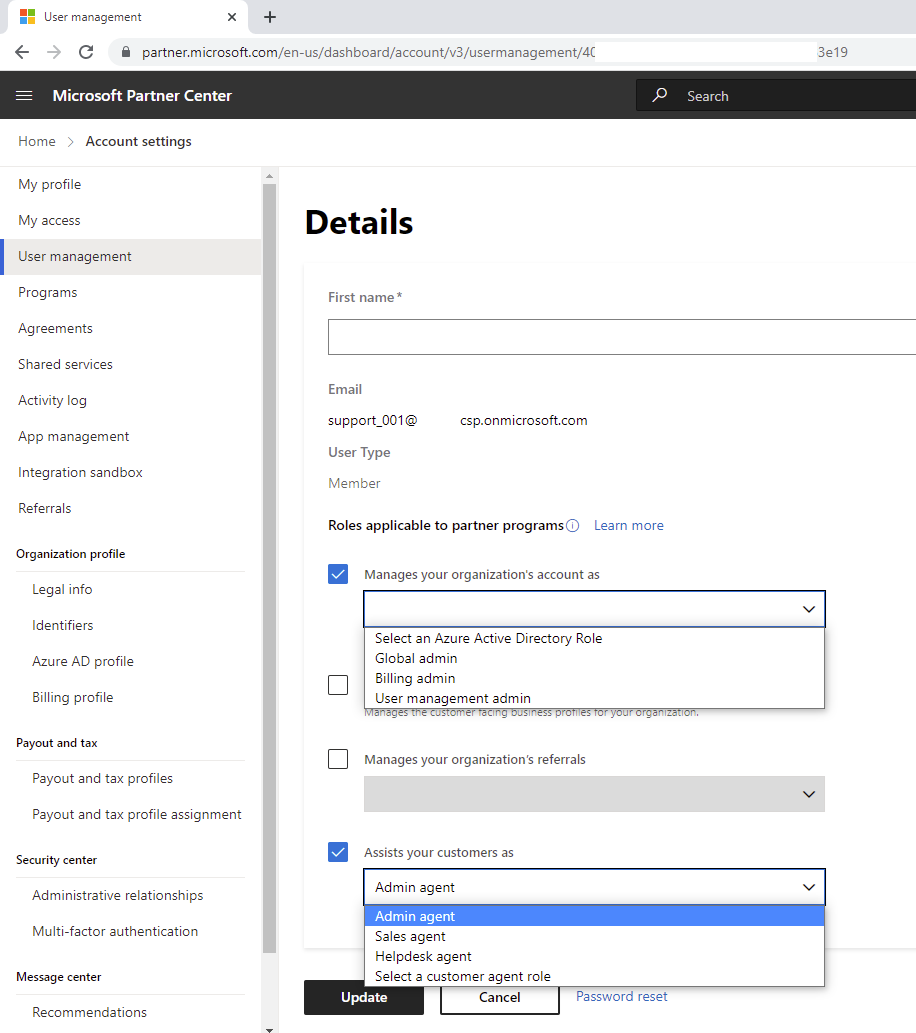
Navigating in the portal https://partner.microsoft.com to User Management, we are able to create accounts and assign predefined roles:
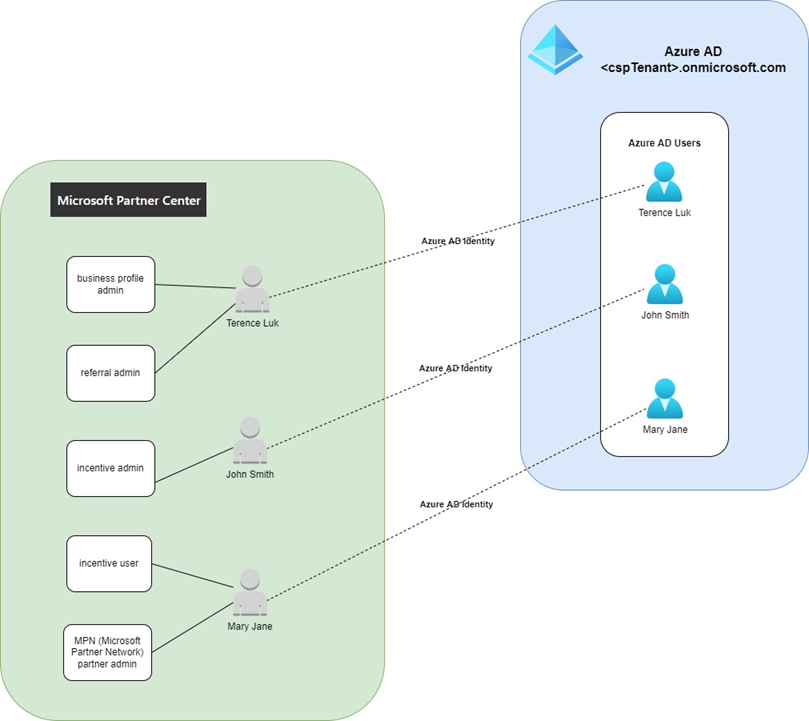
These accounts in the Microsoft Partner Center are user accounts in the CSP Azure AD tenant:
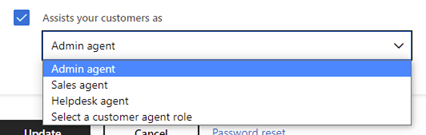
The type of roles and groups we are able to assign accounts are listed under the drop down list Manages your organization’s account as, while the groups we can add the accounts to are listed under Assist your customer as:
The Business Profile admin and Manages your organization’s referrals provide these roles:
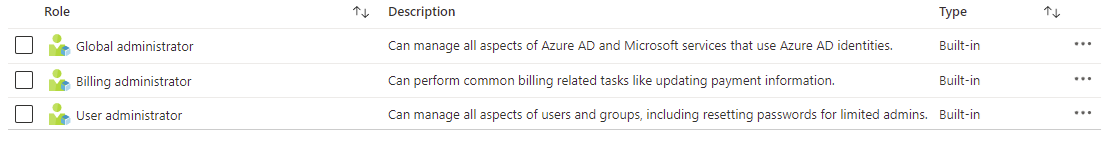
Detailed information about these roles can be found in the following Microsoft documentation:
Azure AD tenant roles and non-Azure AD roles
https://docs.microsoft.com/en-us/partner-center/permissions-overview#azure-ad-tenant-roles-and-non-azure-ad-roles
To summarize, some of these roles and groups are mapped to the Azure AD tenant while the others are not.
Azure AD Tenant Roles
The following is a mapping between the roles listed under: Manages your organization’s account as and the Azure AD tenant roles:
| Microsoft Partner Central Role | Azure AD Role |
| Global admin | Global administrator |
| Billing admin | Billing administrator |
| User management admin | User administrator |
Assigning a user in the Microsoft Partner Center the role of a Global admin will place this identity that lives in Azure AD into the Global administrator role. This is the same for Billing admin > Billing administrator and User management admin > User administrator.
Azure AD Tenant Groups
The roles that are provided under Assist your customer as are mapped as these Azure AD groups:
| Microsoft Partner Central Role | Azure AD Groups |
| Admin Agent | AdminAgents |
| Sales Agent | SalesAgents |
| Helpdesk Agents | HelpdeskAgents |
Assigning a user in the Microsoft Partner Center the role of a Admin Agent will place this identity that lives in Azure AD into the AdminAgents Azure AD group. This is the same for Sales Agents > SalesAgents and Helpdesk Agents > HelpdeskAgents.
Non-Azure AD Tenant Roles
The remaining list of roles are non-Azure AD tenant roles:
- business profile admin
- referral admin
- incentive admin
- incentive user
- MPN (Microsoft Partner Network) partner admin
More information about these non-Azure AD tenant roles: https://docs.microsoft.com/en-us/partner-center/permissions-overview#manage-mpn-membership-and-your-company
CSP Admin Agent, Sales Agent and Helpdesk Agent Azure AD Groups to Customer Subscription Azure RBAC Roles Mappings
One of the most important mappings that should be understood is how the CSP Azure AD groups are mapped to the customers’ subscriptions as Foreign Principal Azure RBAC roles. As described earlier, the following two groups assigned within Partner Center:
- Admin Agent
- Sales Agent
- Helpdesk Agent
… are mapped to the CSP tenant’s Azure AD group:
- AdminAgent
- SalesAgent
- HelpDeskAgent
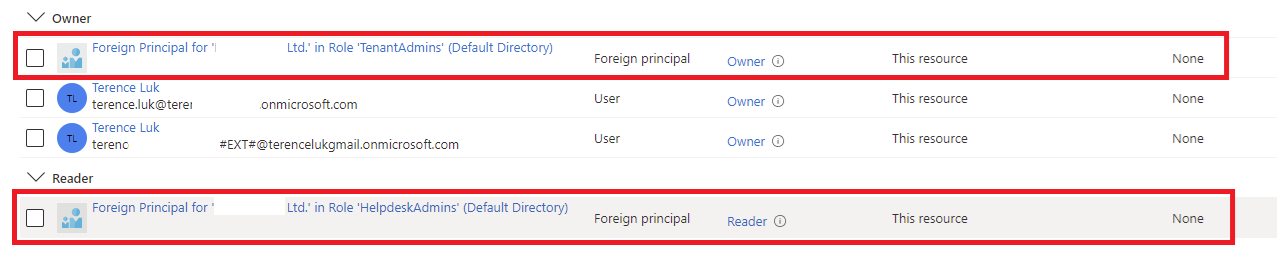
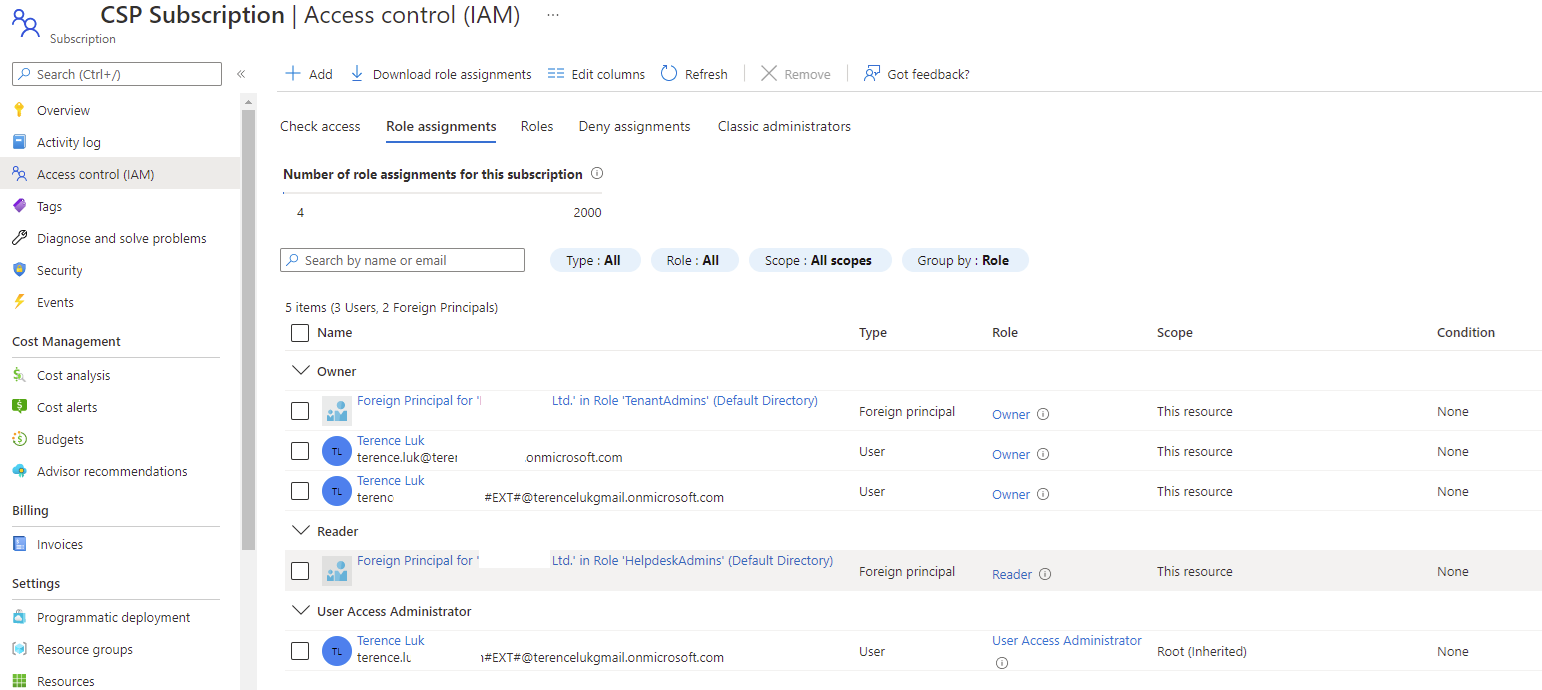
These CSP tenant Azure AD groups can then be granted Azure RBAC roles to the customer’s subscriptions as foreign identities as shown in the screenshot below:
- TenantAdmins
- SalesAdmins
- HelpdeskAdmins
Assigning the CSP tenant’s Azure AD Groups to customers’ subscriptions can only be performed through Azure CLI or PowerShell and cannot be performed through the GUI. To demonstrate this process, I will use the scenario for granting Helpdesk Admin role permissions to open tickets.
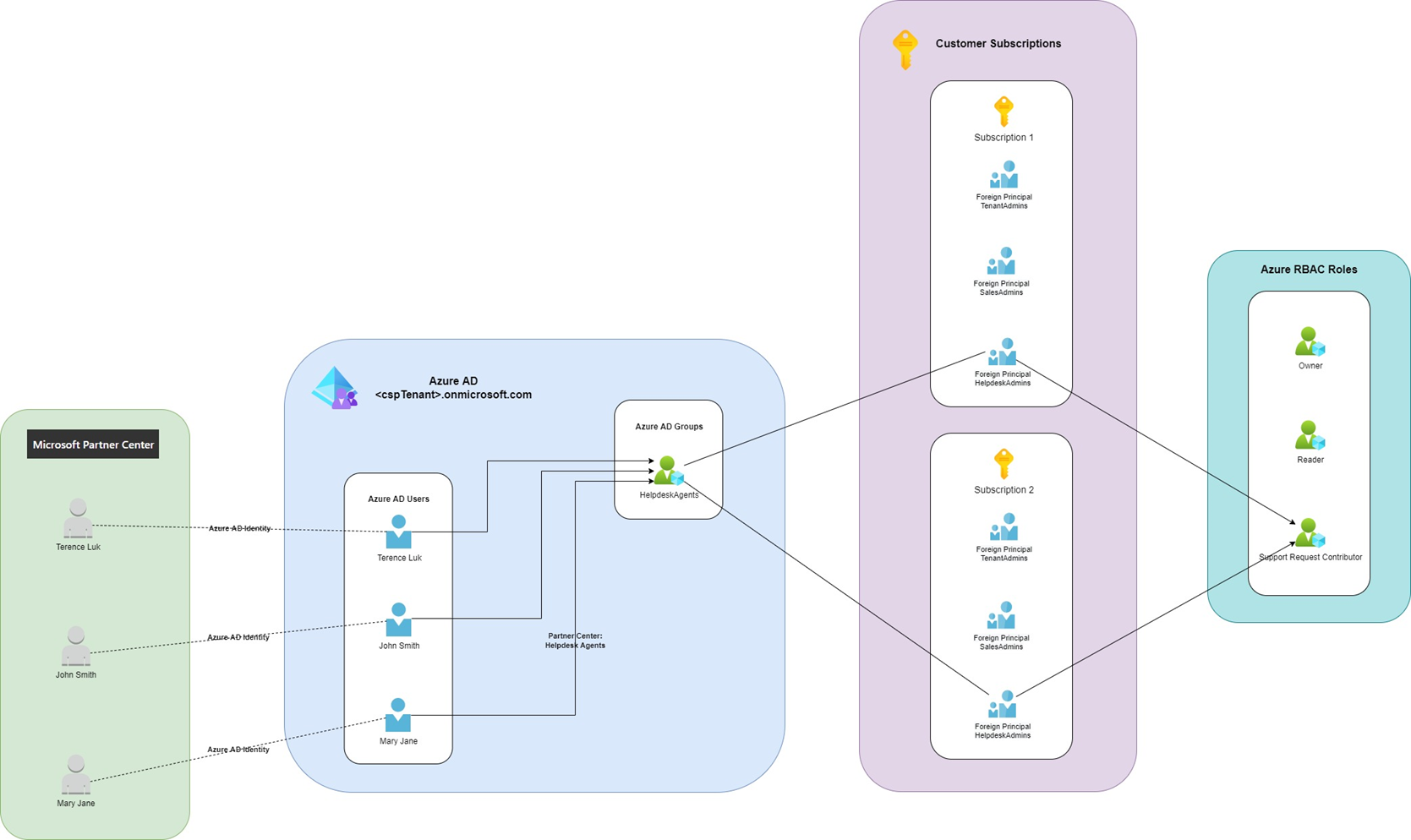
The diagram and the beginning of this walkthrough outlines how the foreign principal mapping are assigned and note that the foreign principals in the diagram can be granted any Azure RBAC rules on the subscription:
Granting CSP Provider Accounts Permissions to Open Tickets
Let’s take the scenario where a Microsoft CSP partner wants to set up an a group of support representatives who simply opens up an Azure support ticket with Microsoft when requested by the customer. These representatives do not need elevated permissions such as Owner, which is automatically granted to the Admin Agents role when a CSP subscription is created, on the subscriptions as they should not have the ability to perform any changes to the subscription and resources. For this scenario, we use the Helpdesk Agent role that is mapped to the HelpdeskAgent Azure AD group, to assign the Support Request Contributor Azure RBAC role onto the customer’s subscription. The following diagram depicts the assignments and how the identities are mapped:
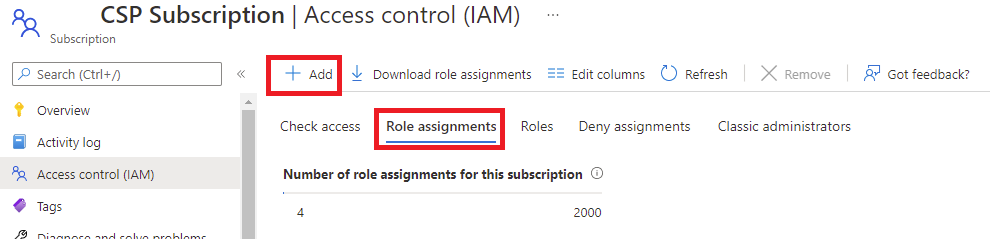
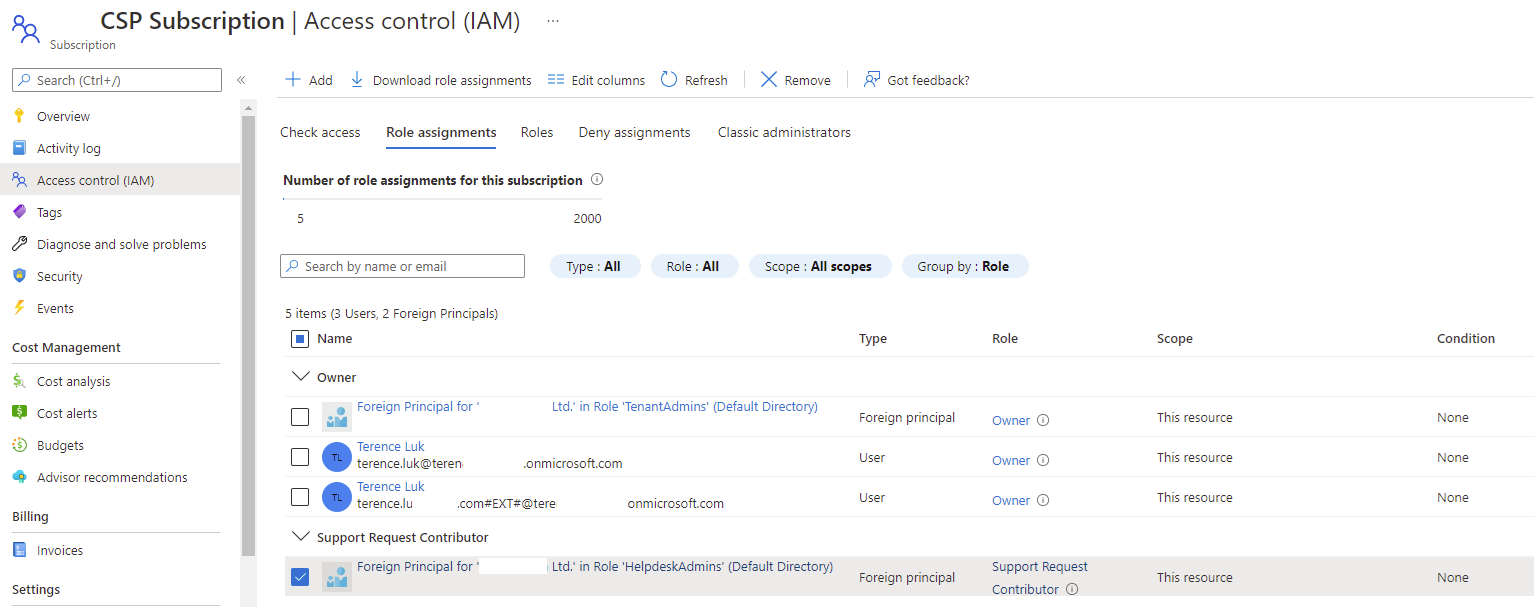
As mentioned earlier, it is not possible to simply sign in as a Owner on the desired customer CSP subscription, navigate to the Access control (IAM) blade, then assign the foreign principal as a Support Request Contributor as shown in the screenshot below because Foreign Principals are not presented from within the portal.azure.com GUI:
The following are instructions on how to assign the HelpdeskAgents Azure AD group in the CSP Azure AD tenant onto a customer’s subscription as a Azure RBAC Support Request Contributor.
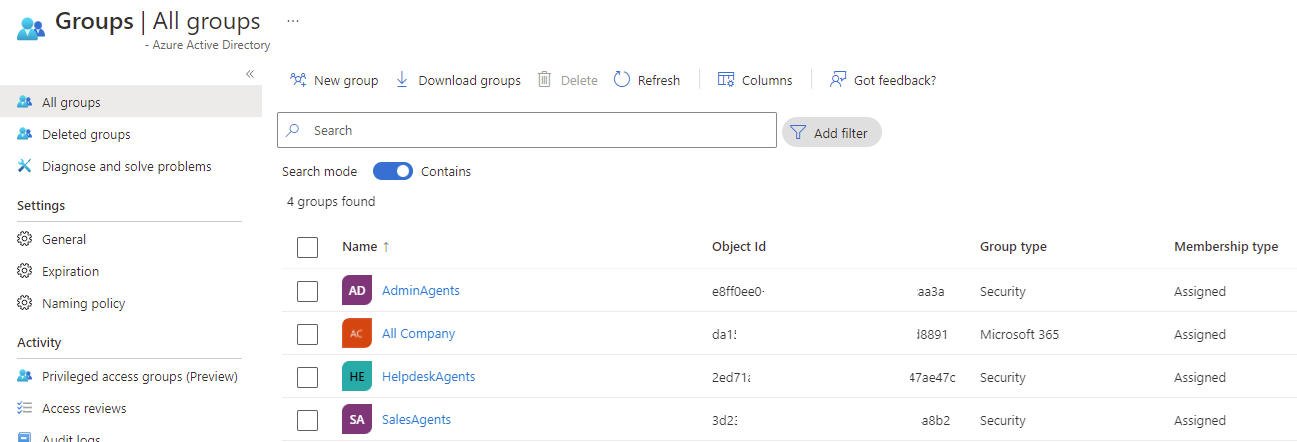
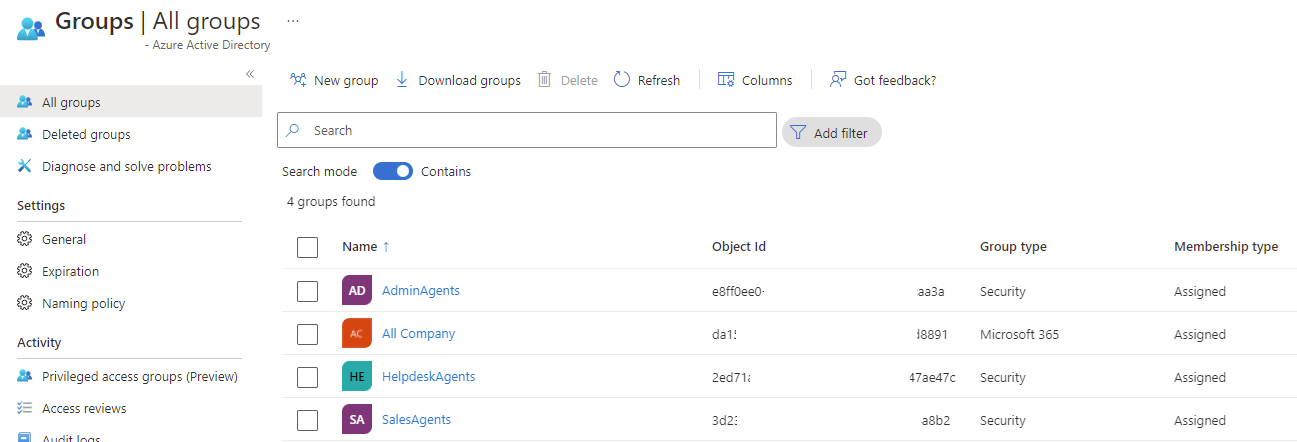
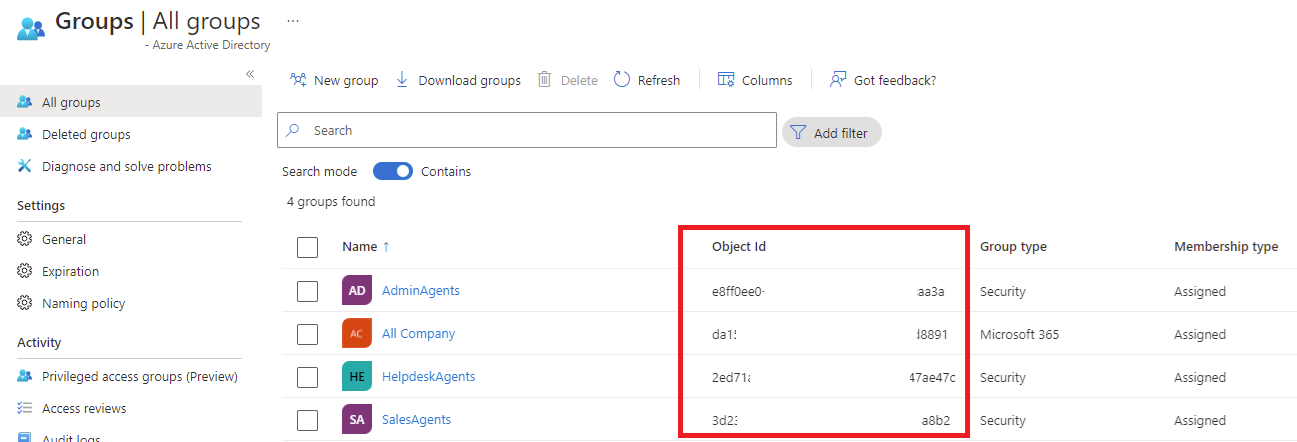
Begin by obtaining the object ID of the HelpdeskAgents Azure AD group in the CSP Azure AD tenant by either navigating to the groups blade:
Or alternatively, use the PowerShell cmdlet Get-AzADGroup to list the Object ID:
Connect-AzAccount ### Log in with CSP partner credentials
Get-AzADGroup | Select-Object DisplayName,Id
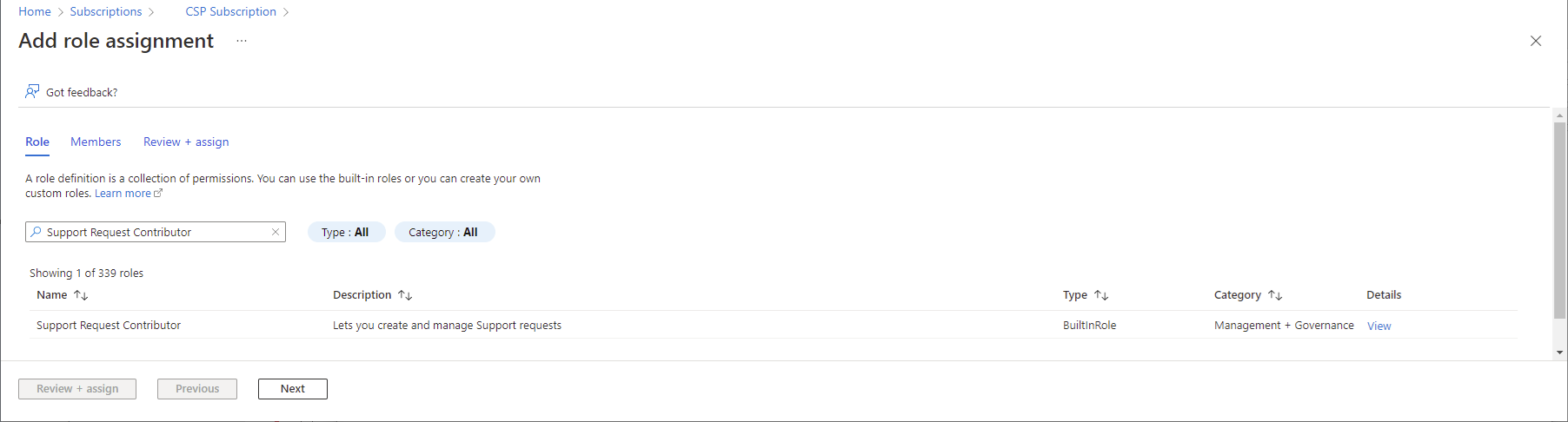
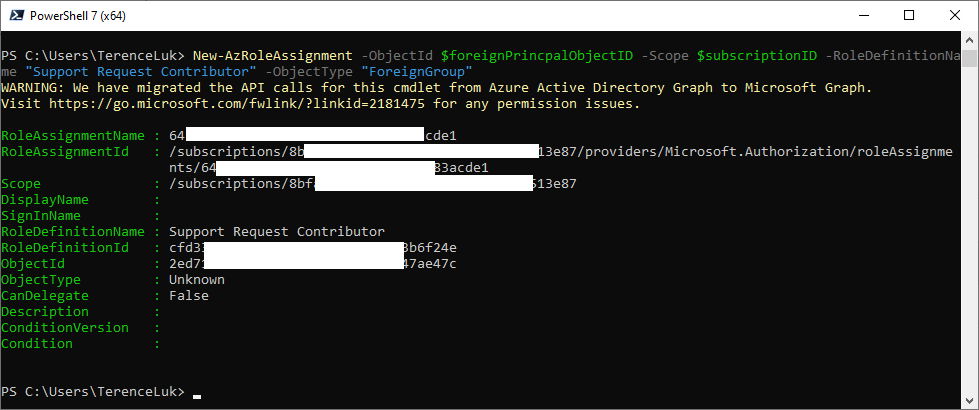
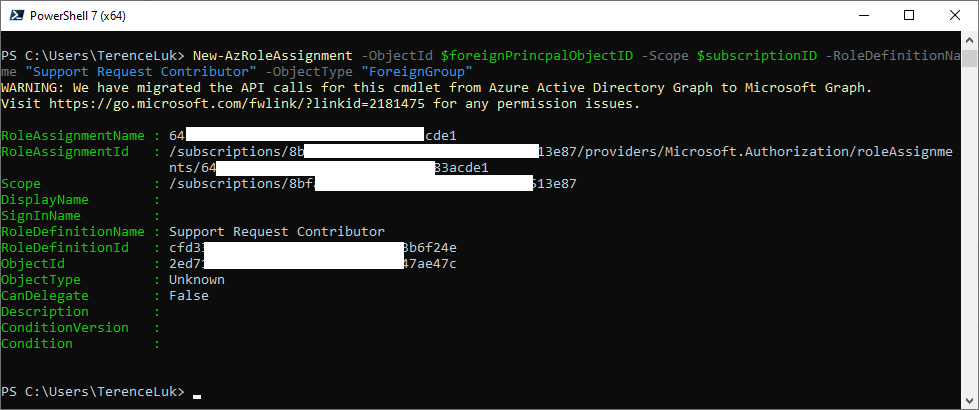
With the HelpdeskAgents Azure AD group ObjectId, proceed to use the following PowerShell New-AzRoleAssignment cmdlet to assign the Azure RBAC role to the desired subscription:
Connect-AzAccount ### Log in with customer global admin credentials
$foreignPrincipalObjectID = “<Azure AD Group Object ID>”
$subscriptionID = “/subscriptions/<Subscription ID>”
New-AzRoleAssignment -ObjectId $foreignPrincipalObjectID -Scope $subscriptionID -RoleDefinitionName “Support Request Contributor” -ObjectType “ForeignGroup”
With the above cmdlet executed, the HelpdeskAdmin foreign principal identity will be displayed as a Support Request Contributor on the subscription and users in this group able to open support tickets:
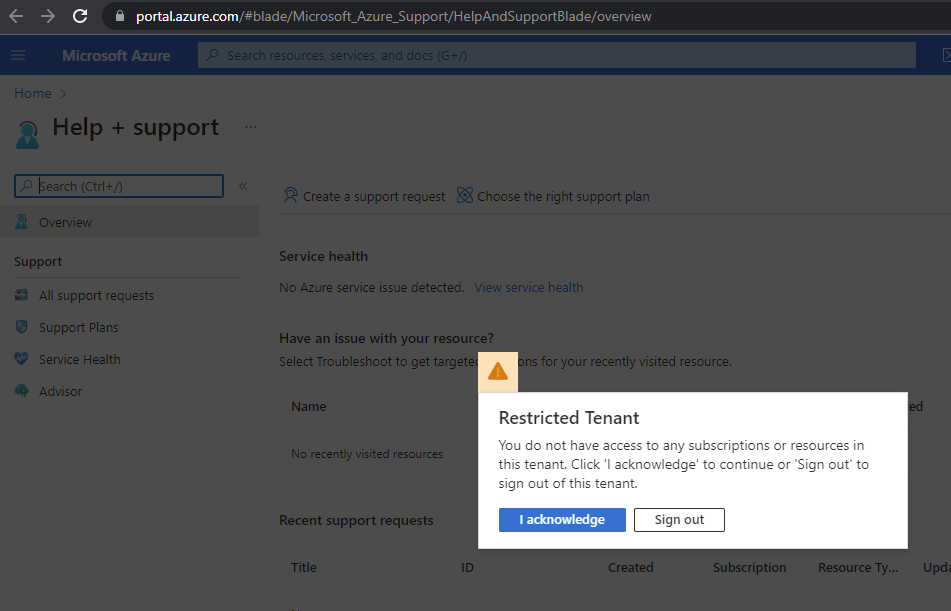
Note that you do not need to grant additional permissions such as reader to the foreign principal if the users only need to open tickets. It is a common misconception that the users need Reader access to the subscription because prior to graning the Support Request Contributor role, trying to open a new service request will display the following:
Restricted Tenant
You do not have access to any subscriptions or resources in this tenant. Click ‘I acknowledge’ to continue or ‘Sign out’ to sign out of this tenant.
It is not necessary to grant Reader and Support Request Contributor to the subscription.
Granting CSP Provider Accounts Permissions to Read Subscription
Another potential scenario is if the CSP partner would like to provide support where representatives will only view and provide guidance for troubleshooting without making any changes. Assuming we want to use the HelpdeskAgents Azure AD Group, we can use the same cmdlet as shown above to assign the Reader Azure RBAC role to the subscription. Providing this permission will allow the users in this group to view all the resources in the subscription (there are some restrictions such as various configuration parameters in app services) but unable to make any changes such as provisioning, editing, or deleting.
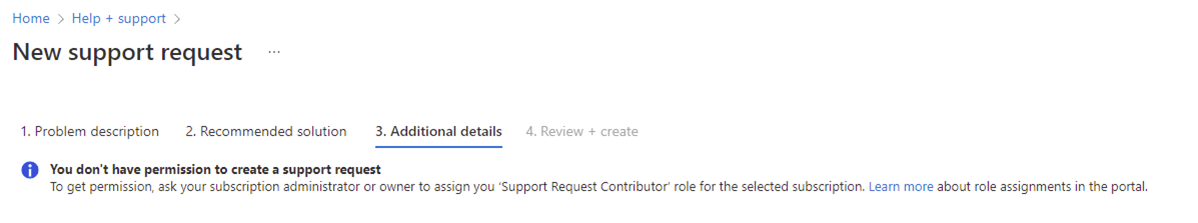
It is also worth noting that having Reader access to a subscription does not permit the user to open support tickets as an attempt to do so will display the following message during the ticket creation process:
You don’t have permission to create a support request
To get permission, ask your subscription administrator or owner to assign you ‘Support Request Contributor’ role for the selected subscription.
—————————————————————————————————————————-
I hope this post helps anyone who may be trying to learn more about how being a CSP can manage their customer’s tenant. The design isn’t overly complex but requires a bit of time to dissect the components and understand how they all interact with each other.