I’ve been working with a lot of automation in Azure lately and wanted to capture as many configuration activities I have gone through to share through my blog, and today’s post is to demonstrate how to set up a service principal with a secret that can be used when using Connect-AzAccount (https://docs.microsoft.com/en-us/powershell/module/az.accounts/connect-azaccount?view=azps-7.1.0), which can be used for automation activities.
The full script that I created can be found at my following Github repo: https://github.com/terenceluk/Azure/blob/main/PowerShell/Connect-AzAccount-with-Service-Principal.ps1
Below is the breakdown of the script and its process.
Begin by authenticating into Azure with:
Connect-AzAccount
Proceed to set the variables (name and password) for creating the App Registration and Enterprise Application that will be named “TestApp”
$spName = “TestApp”
$spPassword = “ChM7Q~fbYA934Q.nFxihDrSfBov3vqhh4g5OG”
$passwordLifeInYears = 3
Use the $spPassword variable containing the password we defined to create an object that is used to create a secret with an expiry date in the TestApp App Registration. For the purpose of this example, the secret will be valid for today’s date + 3 years.
$credentials = New-Object Microsoft.Azure.Commands.ActiveDirectory.PSADPasswordCredential `
-Property @{StartDate=Get-Date; EndDate=Get-Date -Year (Get-Date).AddYears($passwordLifeInYears).year; Password=$spPassword};
$spConfig = @{
DisplayName = $spName
PasswordCredential = $credentials
}
Use the cmdlet below to create the App Registration with a client secret configured and Enterprise Application (Service Principal) named TestApp:
$servicePrincipal = New-AzAdServicePrincipal @spConfig
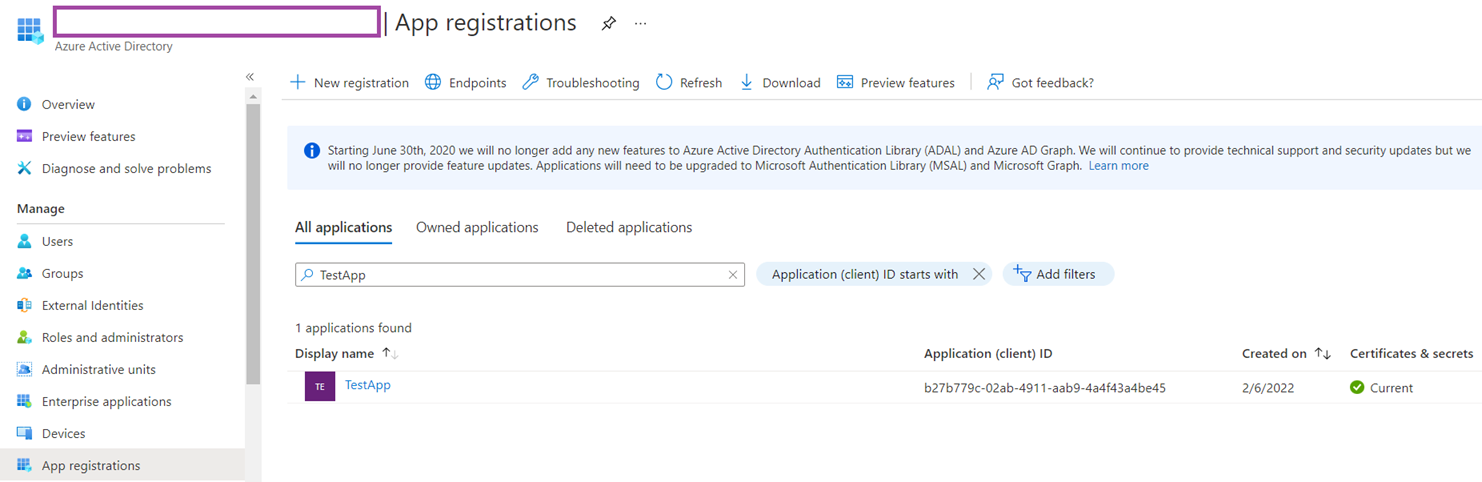
With the cmdlet above executed, you should now be able to see the following TestApp App Registration:
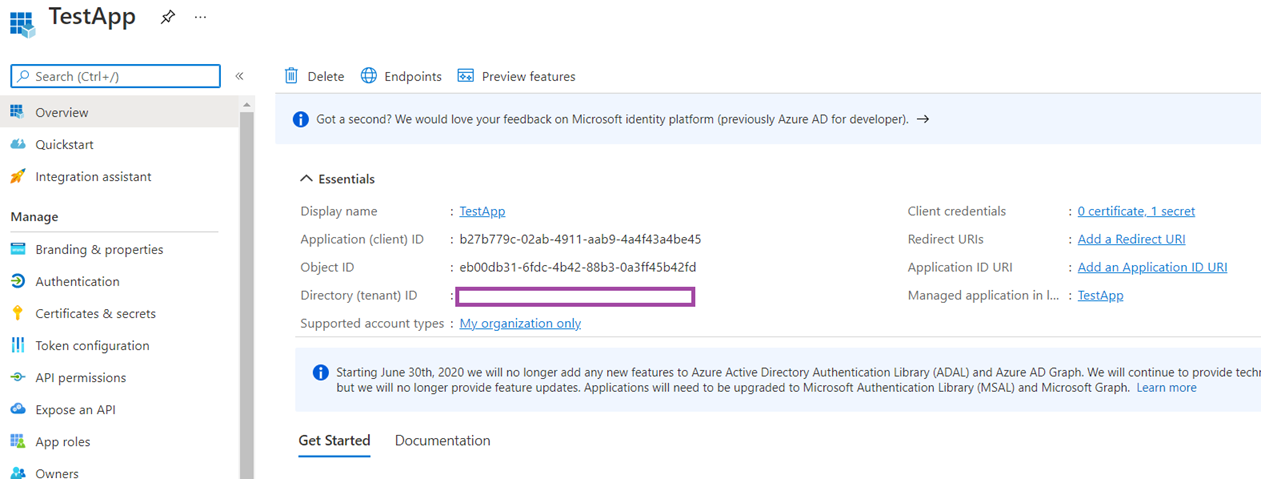
Note the Application ID as you’ll see the Enterprise Application reference it shortly:
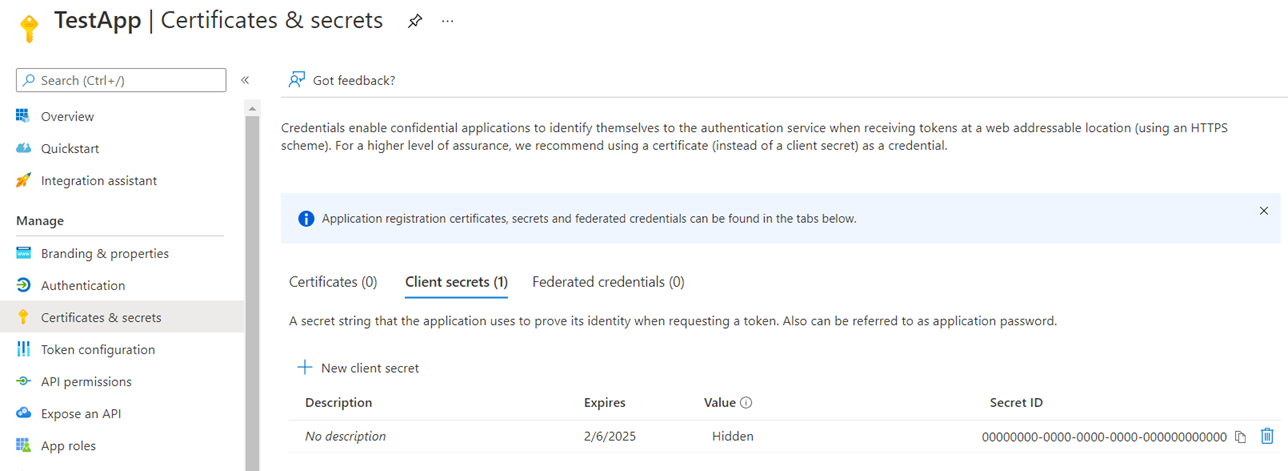
Navigate to the Certificates & secrets area, then select Client secrets, and you’ll see a secret created for it. This secret contains the password we defined earlier but is not retrievable from this portal:
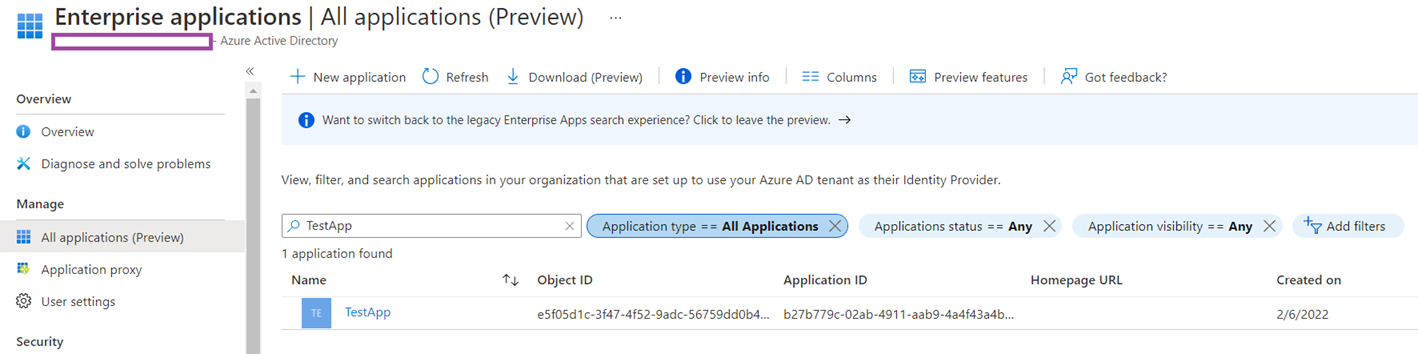
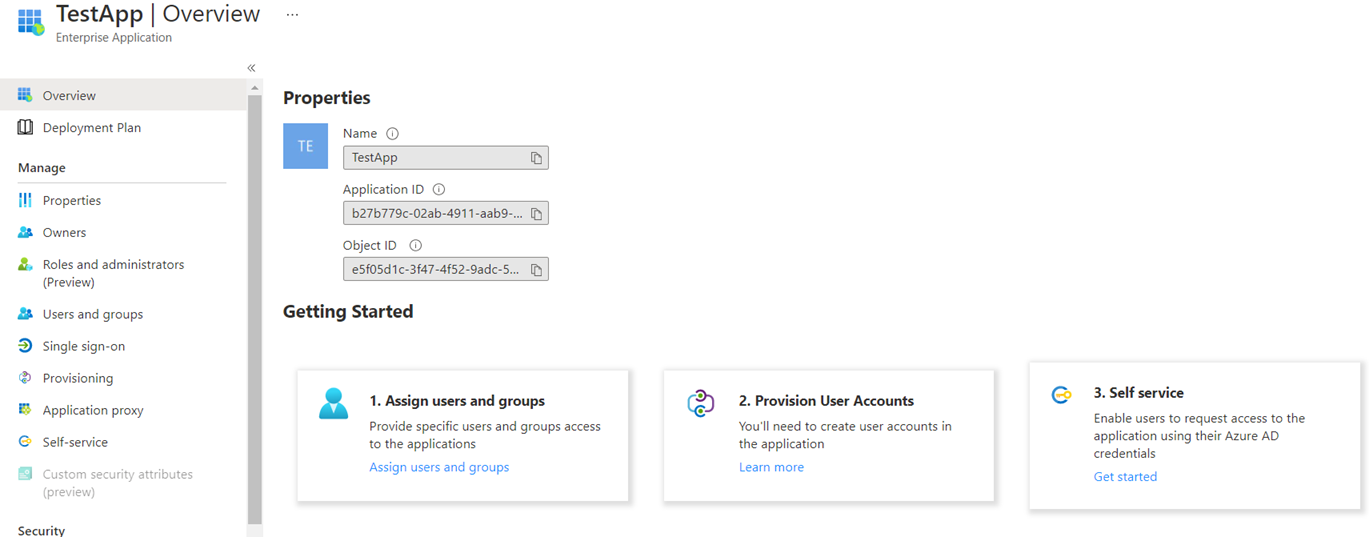
Navigate to the Enterprise Applications and you should see the TestApp created:
Note the same Application ID as the TestApp App Registration in the screenshot above confirming this Enterprise Application (Service Principal) is derived from it:
With the TestApp service principal created, we can now use it to authenticate with Connect-AzAccount but note that we’ll need the following:
- The tenant ID we’re connecting to
- The configured secret for the TestApp App Registration
- The Service Principal Application ID, which can be found from the App Registration or Enterprise Application properties
Begin by defining the variables required to connect:
$tenantId = “84f4470b-3xxx-4xx9-xx95-abxxxxx3024f”
$spPassword = “ChM7Q~fbYA934Q.nFxihDrSfBov3vqhh4g5OG”
$servicePrincipalAppID = “b27b779c-02ab-4911-aab9-4a4f43a4be45” # This is the Application ID of the Enterprise App
Convert the Service Principal secret to secure string:
$password = ConvertTo-SecureString $spPassword -AsPlainText -Force
Create a new credentials object containing the application ID and password that will be used to authenticate:
$psCredentials = New-Object System.Management.Automation.PSCredential ($servicePrincipalAppID, $password)
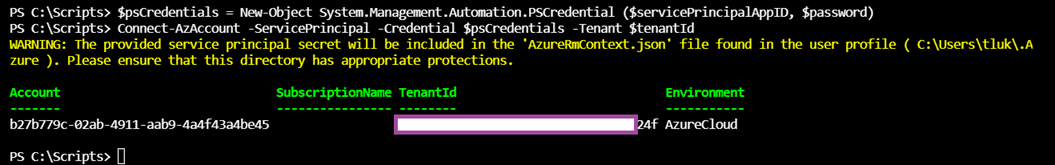
Authenticate with the credentials object:
Connect-AzAccount -ServicePrincipal -Credential $psCredentials -Tenant $tenantId
Hope this helps anyone looking for instructions on how to do this as the instructions I found from Microsoft documentation did not work for me so changes had to be made to a few cmdlets.
Below is the full script pasted into this blog post:
<# Begin by creating the service principal and client secret #>
# Connect-AzAccount – https://docs.microsoft.com/en-us/powershell/module/az.accounts/connect-azaccount?view=azps-7.1.0
# Sign in with a service principal – https://docs.microsoft.com/en-us/powershell/azure/authenticate-azureps?view=azps-7.1.0#sign-in-with-a-service-principal
# Connect to Azure with an authenticated account for use with cmdlets from the Az PowerShell modules
Connect-AzAccount
# Set the variables (name and password) for creating the App Registration and Enterprise Application that will be named “TestApp”
$spName = “TestApp”
$spPassword = “ChM7Q~fbYA934Q.nFxihDrSfBov3vqhh4g5OG”
$passwordLifeInYears = 3
# Use the $spPassword variable containing the password to create an object that is used to create a secret in the TestApp App Registration
# The object will also specify when the date of this secret will expire and that is today’s Month and Date in 3 years
$credentials = New-Object Microsoft.Azure.Commands.ActiveDirectory.PSADPasswordCredential `
-Property @{StartDate=Get-Date; EndDate=Get-Date -Year (Get-Date).AddYears($passwordLifeInYears).year; Password=$spPassword};
$spConfig = @{
DisplayName = $spName
PasswordCredential = $credentials
}
# Create the App Registration with a client secret configured and Enterprise Application (Service Principal) named test app
$servicePrincipal = New-AzAdServicePrincipal @spConfig
##############################################################################################################
<# Try connecting with the newly created Service Principal (Enterprise Application) named TestApp with a secret configured #>
# Define the variables required to connect
$tenantId = “84f4470b-3xxx-4xx9-xx95-abxxxxx3024f”
$spPassword = “ChM7Q~fbYA934Q.nFxihDrSfBov3vqhh4g5OG”
$servicePrincipalAppID = “b27b779c-02ab-4911-aab9-4a4f43a4be45” # This is the Application ID of the Enterprise App
# Convert the Service Principal secret to secure string
$password = ConvertTo-SecureString $spPassword -AsPlainText -Force
# Create a new credentials object containing the application ID and password that will be used to authenticate
$psCredentials = New-Object System.Management.Automation.PSCredential ($servicePrincipalAppID, $password)
# Authenticate with the credentials object
Connect-AzAccount -ServicePrincipal -Credential $psCredentials -Tenant $tenantId