A colleague of mine recently reached out to me to ask why my script from this post:
PowerShell script to assign users in an on-premise AD group to an Azure Enterprise Application’s Users and Groups
https://blog.terenceluk.com/powershell-script-to-assign-users-in-on/
… did not work not work when a service principal was used as the Get-AzureADServiceAppRoleAssignment did not return the Users and Groups of the Enterprise Application that is passed to the cmdlet as the ObjectId. This brought me back to the time when I first worked with this cmdlet and spent hours over the weekend to figure out why this was the case so in hopes of saving others some grief, this post will explain the issue and resolution.
Let me begin by starting with the environment I’ll use for demonstrating this.
Environment
An Application registration named Enterprise-Apps-Permissions-PS is created in this tenant and an Enterprise Application (Service Principal) with the same name has been created from it.
Note that the Object ID of the Enterprise Application is: f984b219-756b-4454-bbf6-4290968836e4
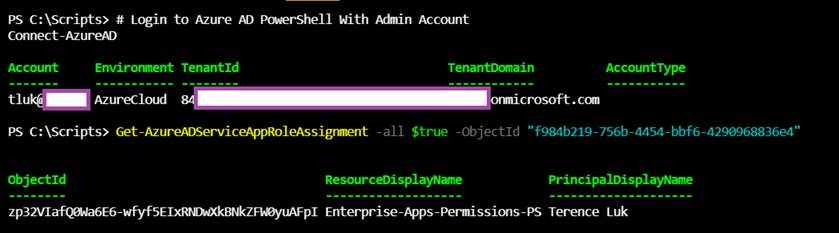
If we wanted to retrieve the Enterprise Application’s Users and Groups via PowerShell, we can simply use the following cmdlets:
# Log into Azure AD PowerShell With Admin Account
Connect-AzureAD
# Retrieve Users and groups assignment
Get-AzureADServiceAppRoleAssignment -all $true -ObjectId “f984b219-756b-4454-bbf6-4290968836e4”
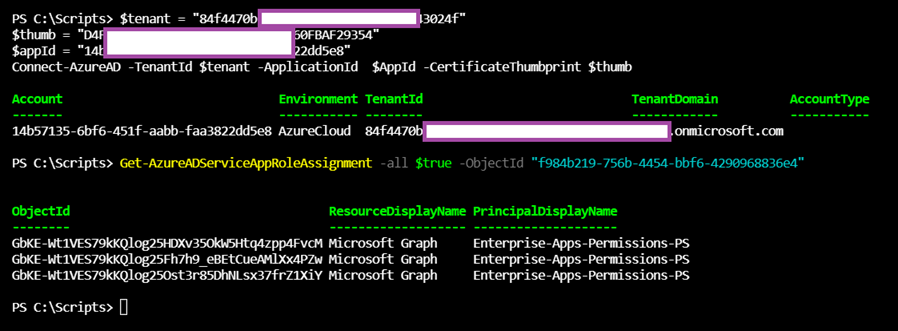
However, if you log in with a service principal using certificate thumbprint to authenticate, executing the same command gives you something different:
# Set variables to connect with service principal
$tenant = “84f4470b-3f1e-4xxxx-9f95-xxxxxxx24f”
$thumb = “D4F02xxxxxx60422BxxxxxxxE60Fxxxxxxxx”
$appId = “14b57135-6bf6-451f-aabb-faa3822dd5e8”
# Connect to Azure AD with service principal
Connect-AzureAD -TenantId $tenant -ApplicationId $AppId -CertificateThumbprint $thumb
# Obtain users and groups
Get-AzureADServiceAppRoleAssignment -all $true -ObjectId “f984b219-756b-4454-bbf6-4290968836e4”
Explanation
The reason why the output is different is because the Get-AzureADServiceAppRoleAssignment looks up and returns different configuration for a user and a service principal.
When logged in as a user and execute Get-AzureADServiceAppRoleAssignment: the Enterprise Application’s Users and Groups will be returned
When logged in as a service principal and execute Get-AzureADServiceAppRoleAssignment: the App registration’s API permissions is returned
Let’s review the output with some side-by-side screenshots.
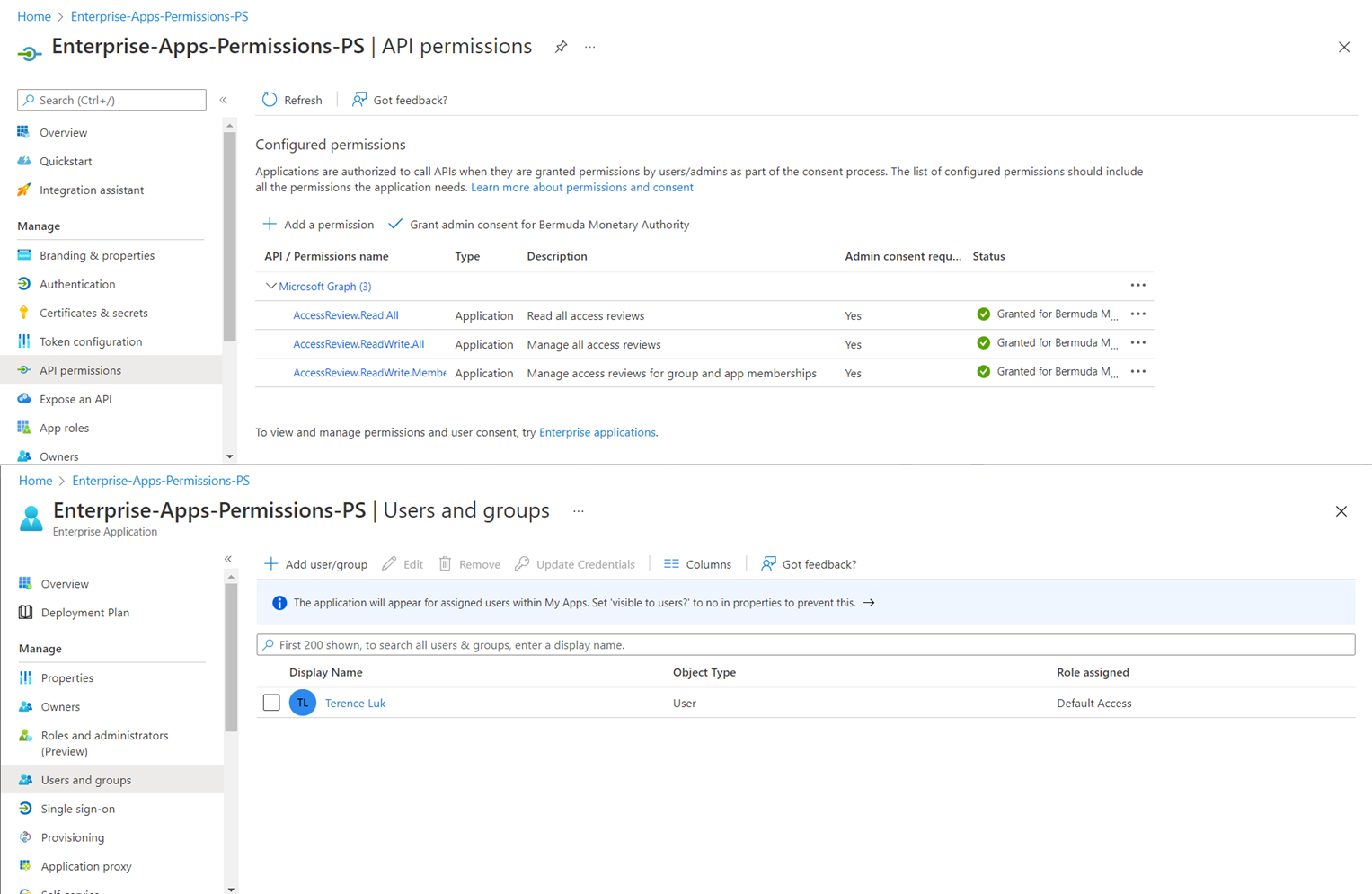
In this environment the App registration named Enterprise-Apps-Permissions-PS has 3 Microsoft Graph permissions assigned to it, which is what Get-AzureADServiceAppRoleAssignment returns when executed under a service principal login. The screenshot has the top window showing the 3 Microsoft Graph permissions assigned to the App registration (Azure Active Directory > App registration > API permissions):
- AccessReview.Read.All
- AccessReview.ReadWrite.All
- AccessReview.ReadWrite.Membership
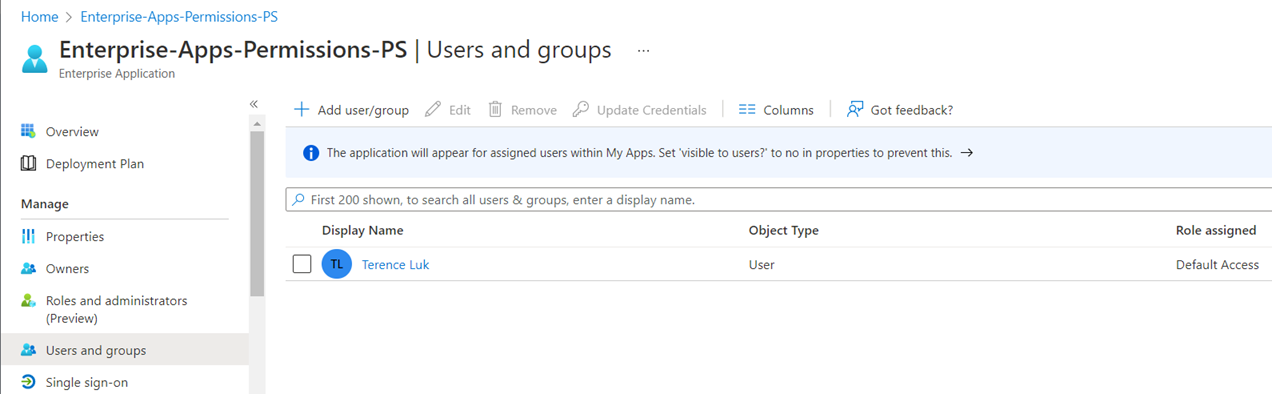
… while the bottom window shows 1 user account assigned to the Enterprise Application linked to the App registration (Azure Active Directory > Enterprise Application > Users and Groups):
- Terence Luk
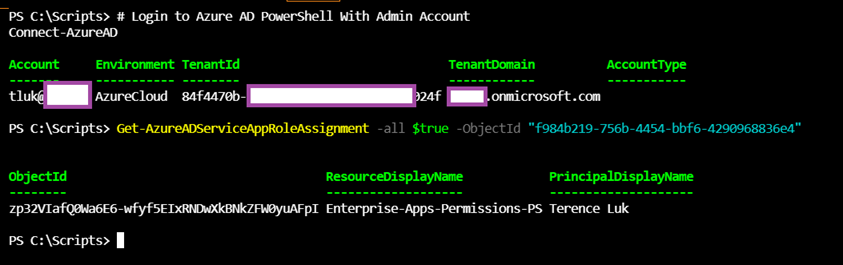
If you use a regular user account to connect to Azure AD via Connect-AzureAD, then proceed use the cmdlet Get-AzureADServiceAppRoleAssignment (https://docs.microsoft.com/en-us/powershell/module/azuread/get-azureadserviceapproleassignment?view=azureadps-2.0) and execute the following:
Get-AzureADServiceAppRoleAssignment -all $true -ObjectId “f984b219-756b-4454-bbf6-4290968836e4”
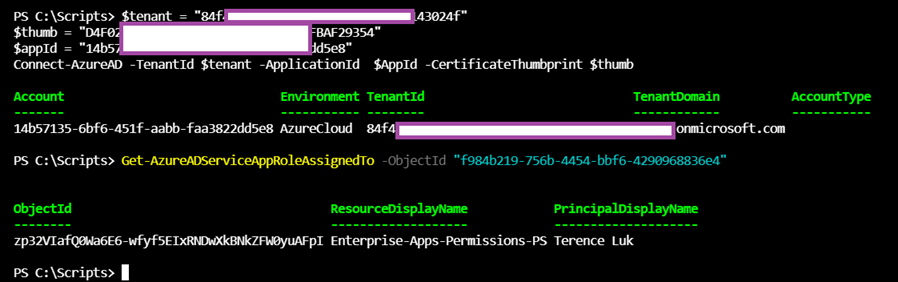
You’ll receive the user and groups assigned to the Enterprise Application as shown in the following PowerShell output and screenshot:
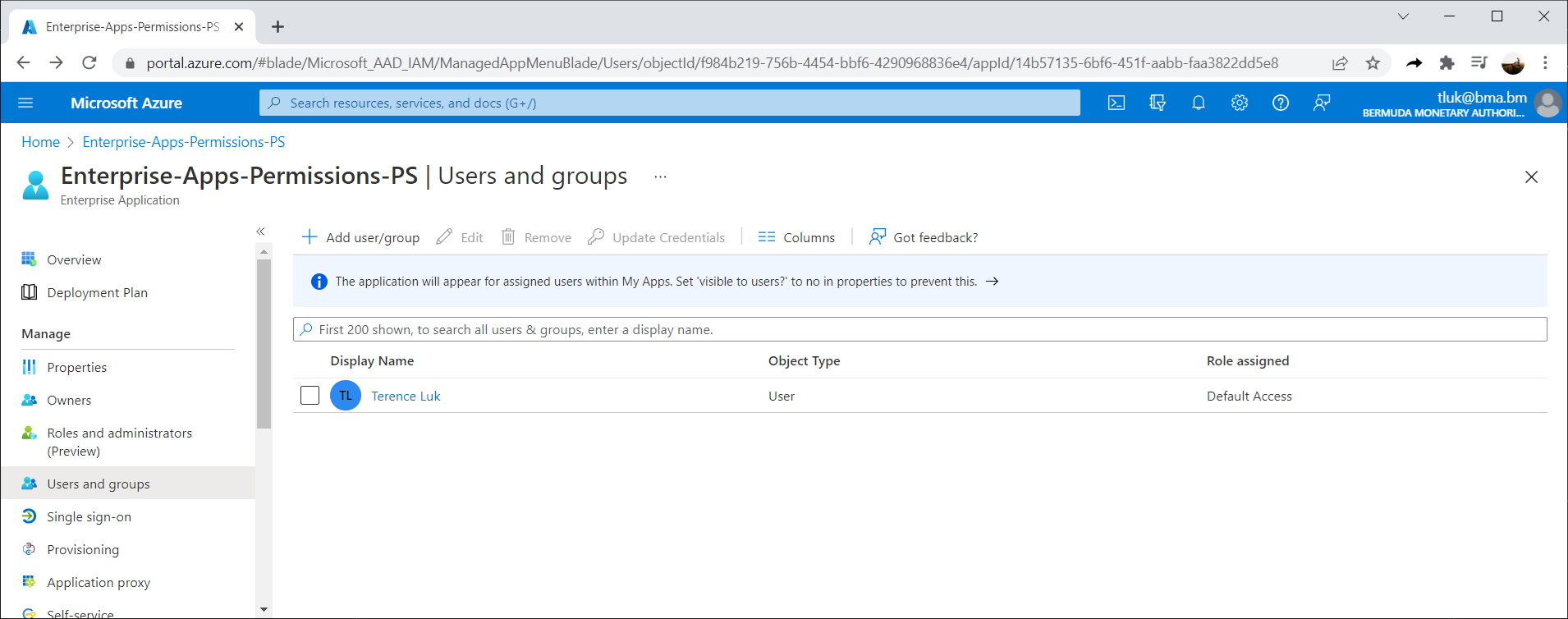
However, if you connect into Azure AD with a Service Principal using certificate authentication as such:
$tenant = “84f4470b-3f1e-4xxxx-9f95-xxxxxxx24f”
$thumb = “D4F02xxxxxx60422BxxxxxxxE60Fxxxxxxxx”
$appId = “14b57135-6bf6-451f-aabb-faa3822dd5e8”
Connect-AzureAD -TenantId $tenant -ApplicationId $AppId -CertificateThumbprint $thumb
Then execute the same cmdlet:
Get-AzureADServiceAppRoleAssignment -all $true -ObjectId “f984b219-756b-4454-bbf6-4290968836e4”
You’ll receive the API Permissions assigned to the App registration as shown in the following PowerShell output and screenshot:
Solution
The Microsoft documentation isn’t very clear (or maybe I’m not reading them properly) but all the examples show Get-AzureADServiceAppRoleAssignment as the cmdlet to use to list the Enterprise Application’s Users and Groups. However, if you’re using a service principal because you’re trying to automate the execution of a script, you actually need to use this cmdlet:
Get-AzureADServiceAppRoleAssignedTo
https://docs.microsoft.com/en-us/powershell/module/azuread/get-azureadserviceapproleassignedto?view=azureadps-2.0
Note the follow output when executing as a service principal:
Hope this helps anyone who might run into this issue as it took quite a big chunk of my weekend when I was troubleshooting this.
Also note that the cmdlet New-AzureADUserAppRoleAssignment to assign a user or group to the Enterprise Application does not change when using a service principal.