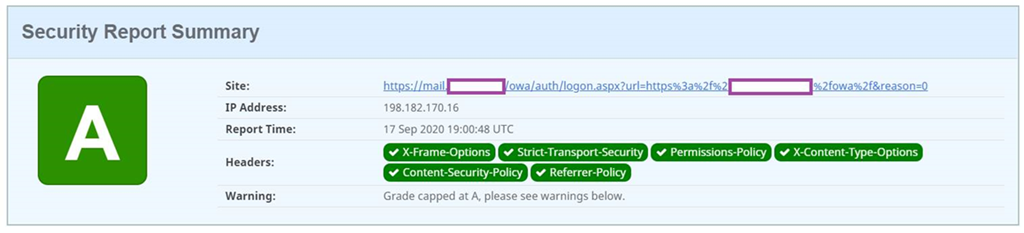
I’ve recently been involved with a few projects involving security vulnerabilities from penetration scans and one of the clients were asked to secure their Exchange OWA portal load balanced behind a Citrix ADC so that 2 of the 6 headers that are identified to be missing from the Security Headers (https://securityheaders.com/) scan are addressed:
- X-Content-Type-Options
- Permissions-Policy
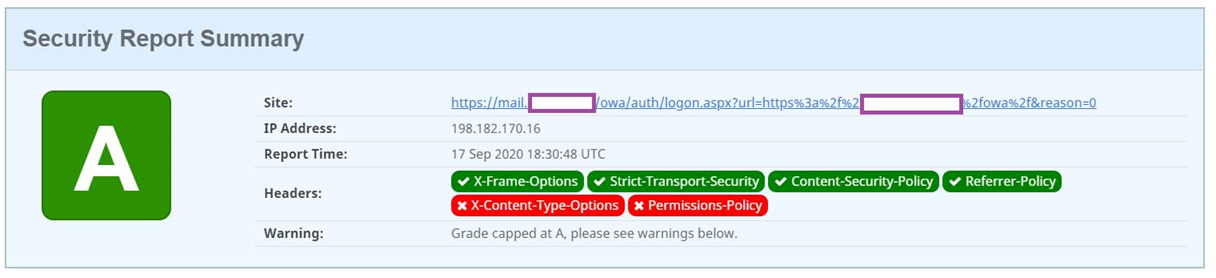
Please refer to my previous blog post for instructions on how to implement the other headers identified to be present in the scan above:
Securing a Citrix ADC (formally known as NetScaler VPX) to score an A rating on Security Headers – March 2020
https://blog.terenceluk.com/securing-citrix-adc-formally-known-as/
X-Content-Type-Options
The X-Content-Type-Options header is fairly easy to implement as it is described in Citrix’s knowledge base article:
How to create rewrite policy for content security headers , XSS protection, HSTS, X-Content-Type-Options & Content-Security-Policy.
https://support.citrix.com/article/CTX233095
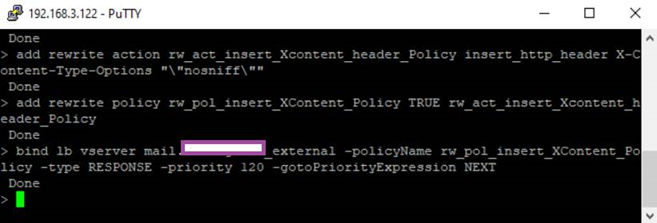
The following are the CLI commands:
add rewrite action rw_act_insert_Xcontent_header_Policy insert_http_header X-Content-Type-Options “”nosniff””
add rewrite policy rw_pol_insert_XContent_Policy TRUE rw_act_insert_Xcontent_header_Policy
bind lb vserver mail.college.bm_external -policyName rw_pol_insert_XContent_Policy -type RESPONSE -priority 120 -gotoPriorityExpression NEXT
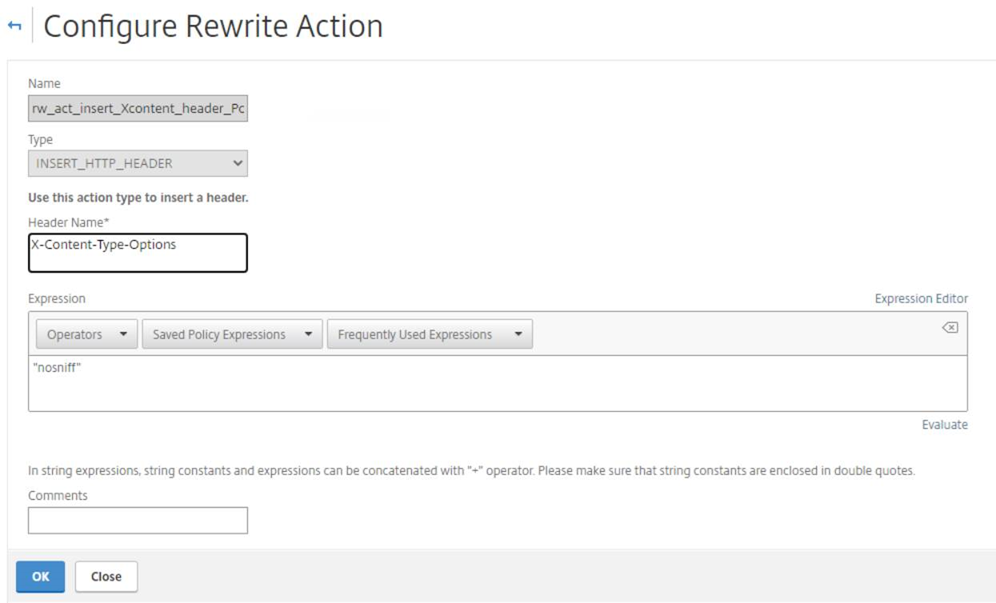
The following is the Rewrite Action in the Citrix ADC / NetScaler GUI:
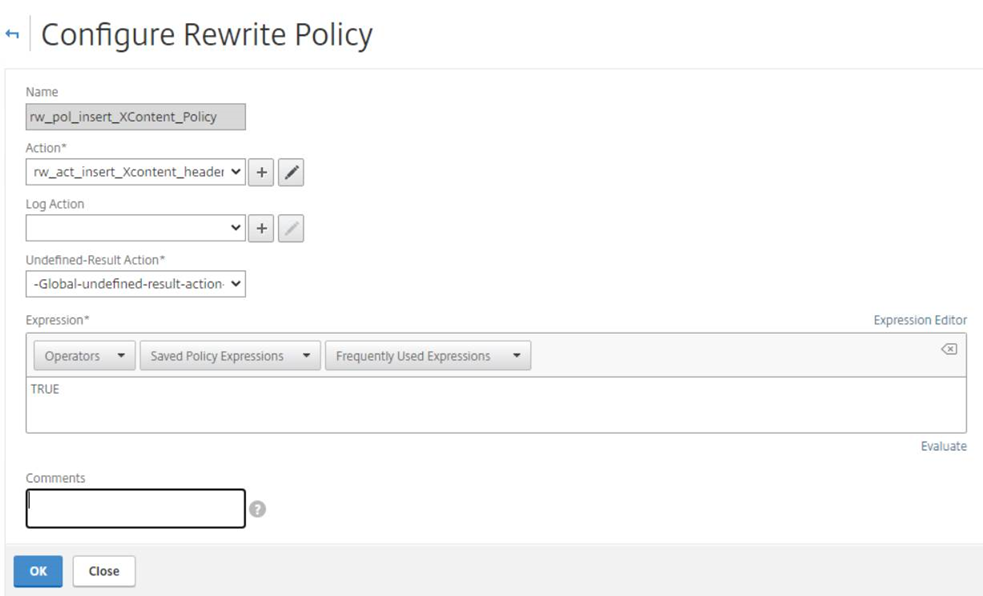
The following is the Rewrite Policy in the Citrix ADC / NetScaler GUI:
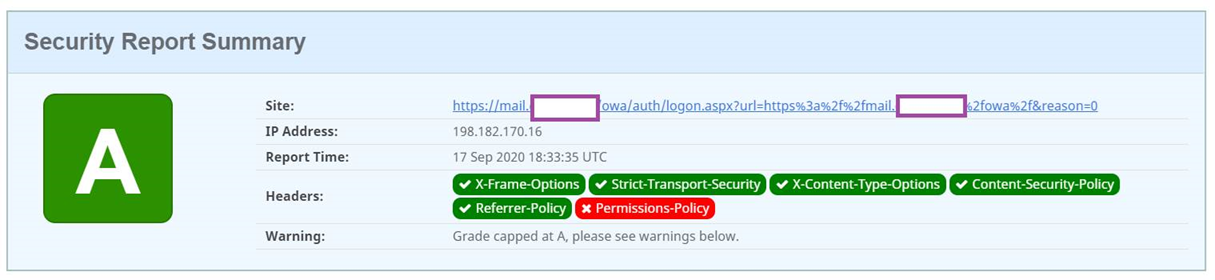
With the Rewrite Action and Policy in place, and having the policy bound to the virtual server, the scan should now return the header as being present:
Permissions-Policy
The Permissions-Policy, which replaces the Feature Policy, isn’t as straight forward as Citrix does not have a KB for the implementation of this header. However, Scott Helme provides a very detailed explanation for this header:
Goodbye Feature Policy and hello Permissions Policy!
https://scotthelme.co.uk/goodbye-feature-policy-and-hello-permissions-policy/
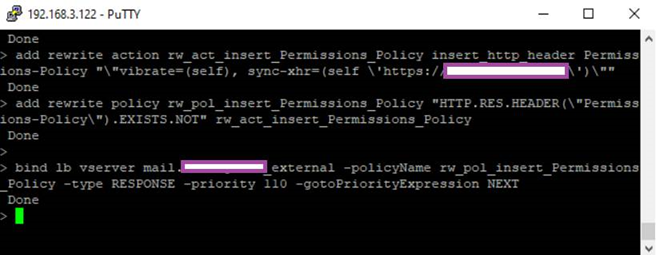
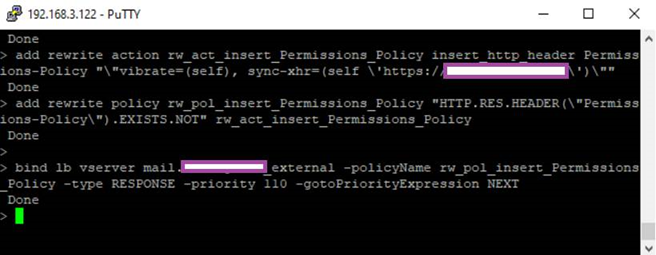
The following are the CLI commands to create the Rewrite Action, Policy and bind it to the virtual server:
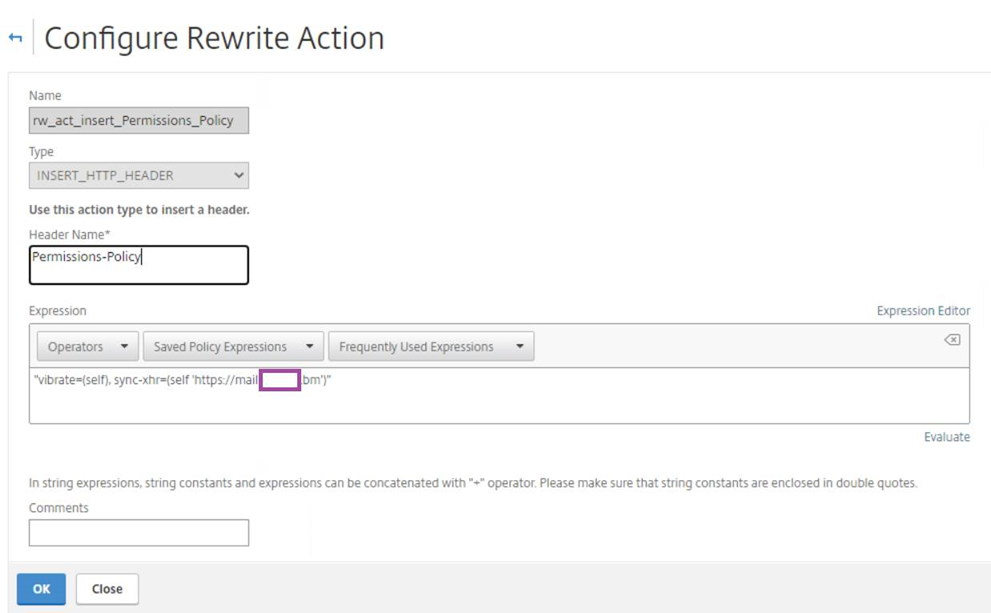
add rewrite action rw_act_insert_Permissions_Policy insert_http_header Permissions-Policy “”vibrate=(self), sync-xhr=(self ‘https://<owa.domain.com>’)””
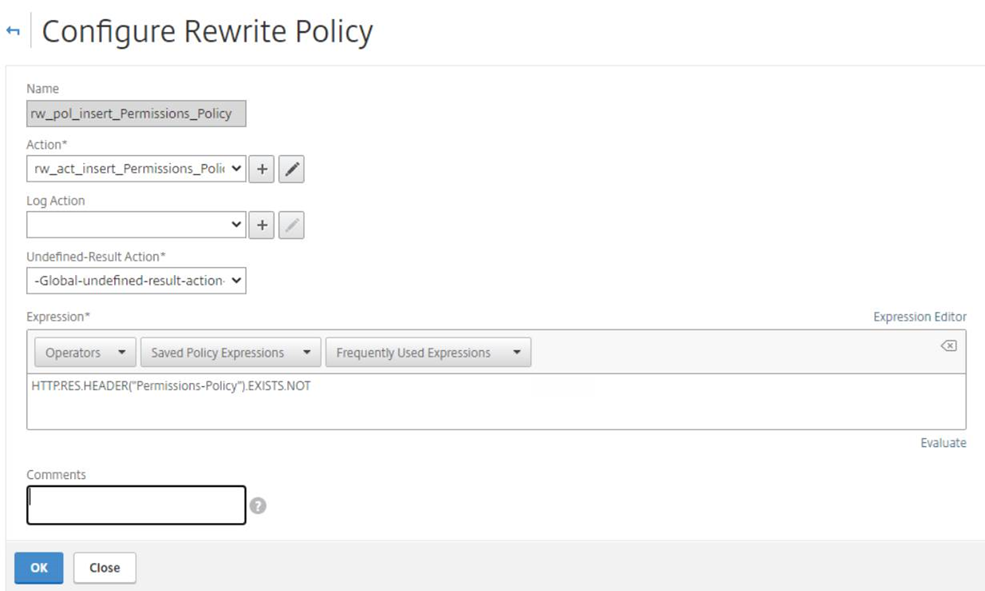
add rewrite policy rw_pol_insert_Permissions_Policy “HTTP.RES.HEADER(“Permissions-Policy”).EXISTS.NOT” rw_act_insert_Permissions_Policy
bind lb vserver mail.contoso.com_external -policyName rw_pol_insert_Permissions_Policy -type RESPONSE 110 -gotoPriorityExpression NEXT
The following is the Rewrite Action in the Citrix ADC / NetScaler GUI:
The following is the Rewrite Policy in the Citrix ADC / NetScaler GUI:
With the Rewrite Action and Policy in place, and having the policy bound to the virtual server, the scan should now return the header as being present:
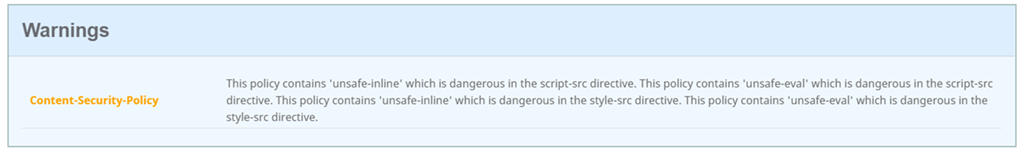
**Note that the reason why the score in the screenshot above is A rather than A+ is because the Content-Security-Policy header configured contains the ‘unsafe-inline’ in the script-src directive. I have yet to successfully omit ‘unsafe-inline’ for sites such as a Citrix Gateway or Exchange OWA without causing the login page to fail to load.