I’ve recently had a few clients reach out to me about the configuration for publishing Office 365 SaaS applications via Citrix Workspace because most quickly realize that it isn’t as easy as using the SaaS templates in the Citrix Cloud portal as soon as the service is provisioned. Doing so would present the application icon:
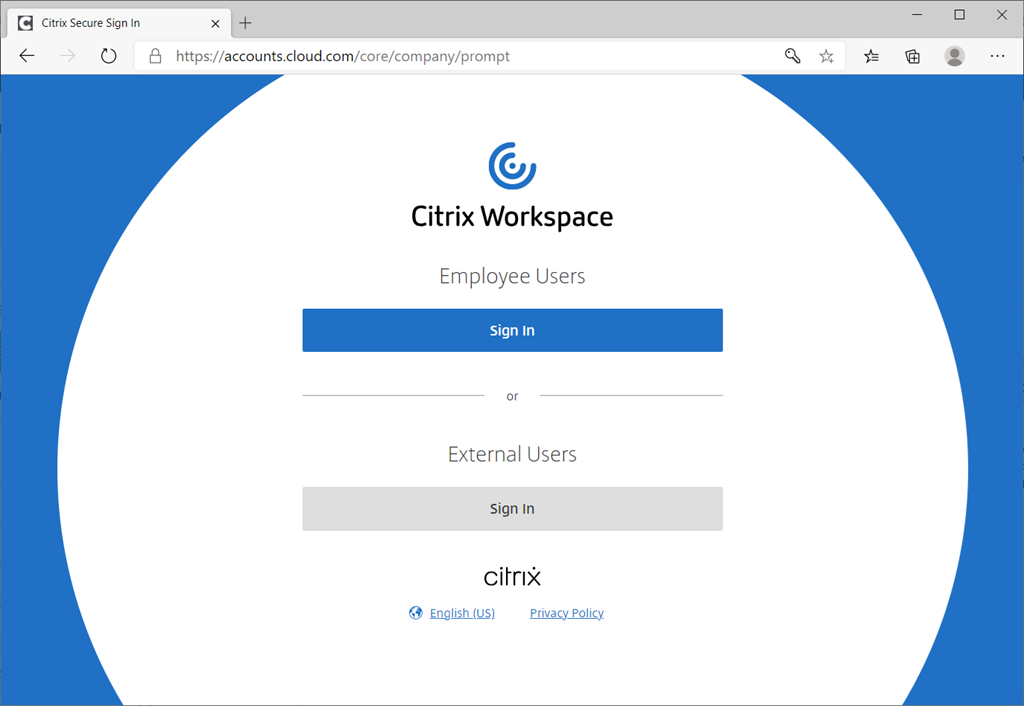
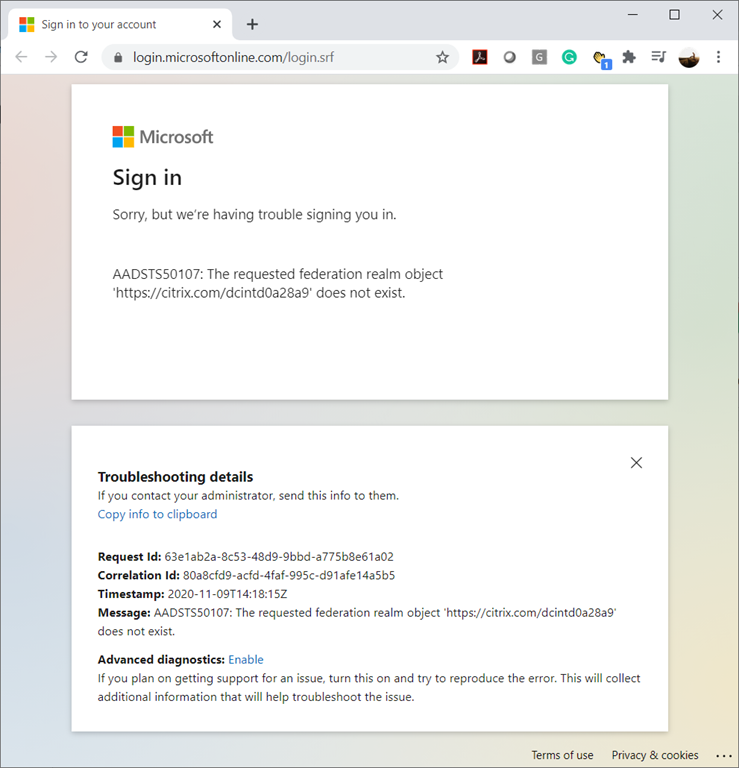
… but clicking on it will display the following error:
Sign in
Sorry, but we’re having trouble signing you in.
AADSTS50107: The requested federation realm object ‘https://citrix.com/dcintd0a28a9’ does not exist.
Troubleshooting details
If you contact your administrator, send this info to them.
Request Id: 63e1ab2a-8c53-48d9-9bbd-a775b8e61a02
Correlation Id: 80a8cfd9-acfd-4faf-995c-d91afe14a5b5
Timestamp: 2020-11-09T14:18:15Z
Message: AADSTS50107: The requested federation realm object ‘https://citrix.com/dcintd0a28a9’ does not exist.
Advanced diagnostics: Enable
If you plan on getting support for an issue, turn this on and try to reproduce the error. This will collect additional information that will help troubleshoot the issue.
One of the important prerequisites that many administrators may not be away of is that Citrix Workspace requires a domain in Azure AD to be federated with it in order to successfully publishing Office 365 as a SaaS application. The choices for federation is to federate the primary domain or another domain that is verified within Azure AD. Most of the clients I work with would not be able to federate their primary domain because that would cause users who attempt to log into Office 365 via https://office.com or https://login.microsoftonline.com/ to be redirected to the Citrix Workspace portal for authentication:
https://accounts.cloud.com/core/company/prompt
With this in mind, what I typically recommend is to review and select a domain that the organization owns and can be verifiable but is not used for any Office 365 authentication to federate with Citrix.
The following Prerequisites section of the document provides a more detailed explanation about this:
The rest of the document provides instructions on how to configure the federation:
Citrix Gateway SaaS and O365 Cloud Citrix Validated Reference Design
https://docs.citrix.com/en-us/advanced-concepts/design-guides/citrix-gateway-o365-saas.html
What I’ve been told by a lot of administrators who may not be completely familiar with Citrix Cloud is that a few of the steps can be confusing so I would like to write this short blog post to demonstrate the configuration.
Prerequisites
Before beginning the federation configuration, ensure that a domain has been selected and verified in the Office 365 portal (Azure AD) as we will need this for the configuration:
Step #1 – Install Azure AD Modules and Connect to Azure Active Directory
Begin by launching PowerShell as an administrator and install the AzureAD modules then connect to Azure Active Directory with the following cmdletse:
Install-Module AzureAD -Force
Import-Module AzureAD -Force
Install-Module MSOnline -Force
Import-module MSOnline -Force
Connect-MsolService
Step #2 – Define the required variables
The following are the variables that will need to be defined and where to obtain the information:
$dom = “contoso.com” < replace contoso.com with the domain that has been selected and verified in Azure AD to federate with Citrix Workspace
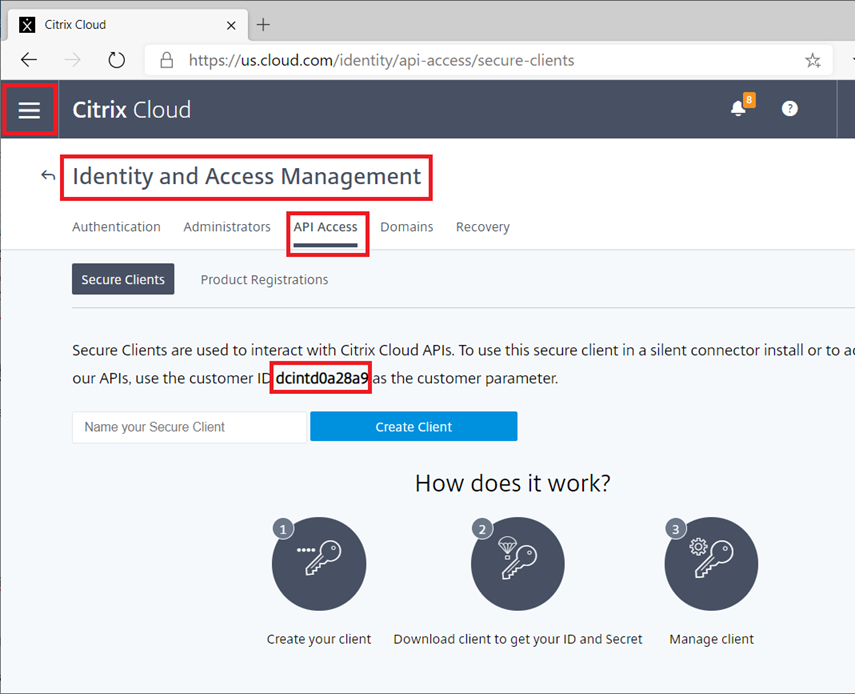
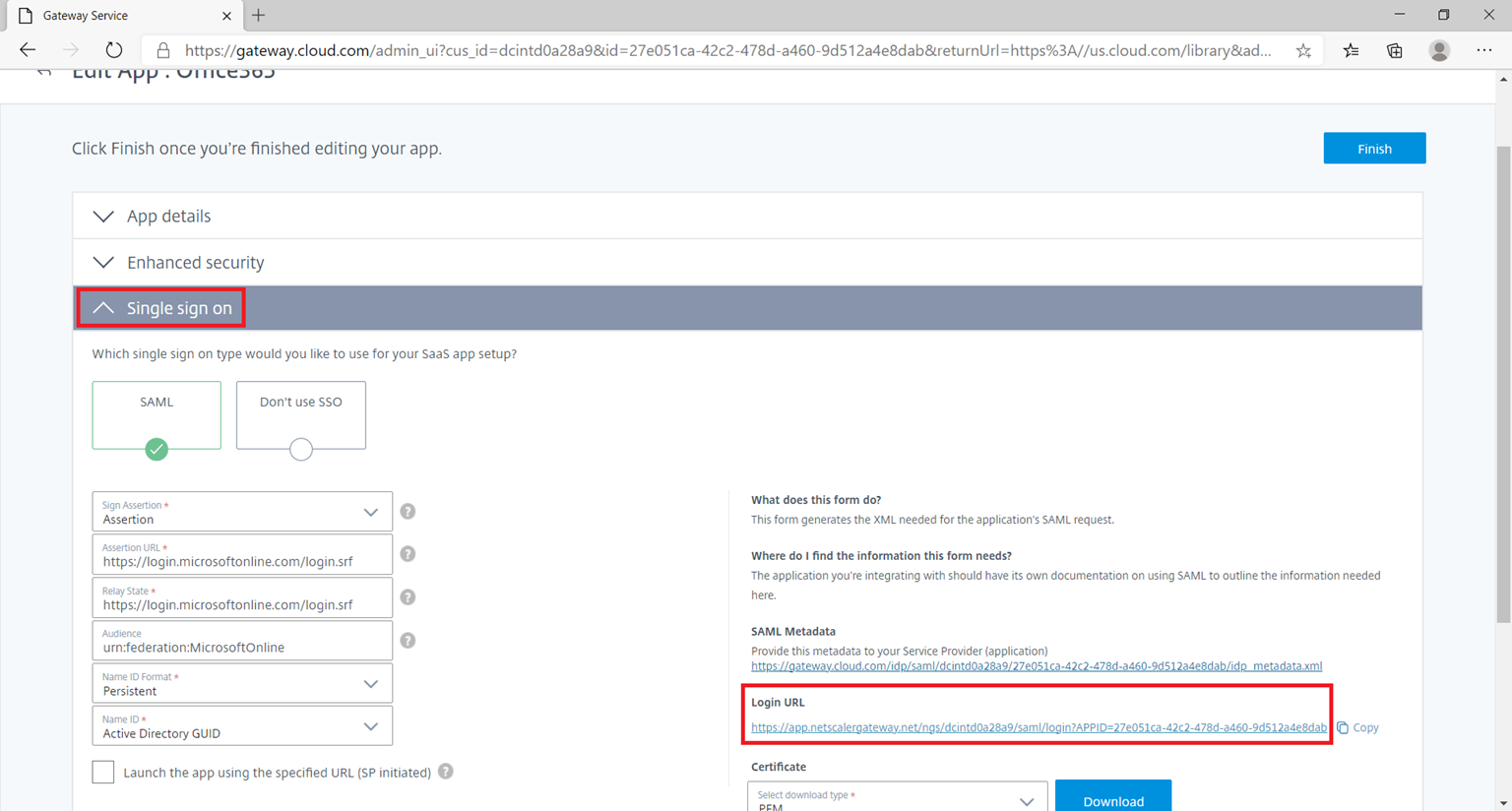
$IssuerUri = “https://citrix.com/dcintd0a28a9” < replace the dcintd0a28a9with the Customer ID, which can be located here in the Citrix Cloud portal:
$fedBrandName = “CitrixWorkspace” < Leave this without any changes
$logoffuri = “https://app.netscalergateway.net/cgi/logout” < Leave this without any changes
$uri = “https://app.netscalergateway.net/ngs/dcintd0a28a9/saml/login?APPID=27e051ca-42c2-478d-a460-9d512a4e8dab” < Replace the full https:// URI with the following:
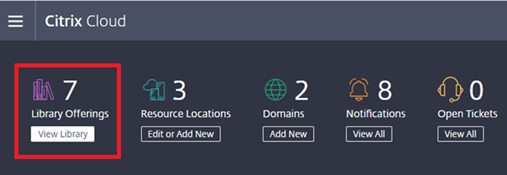
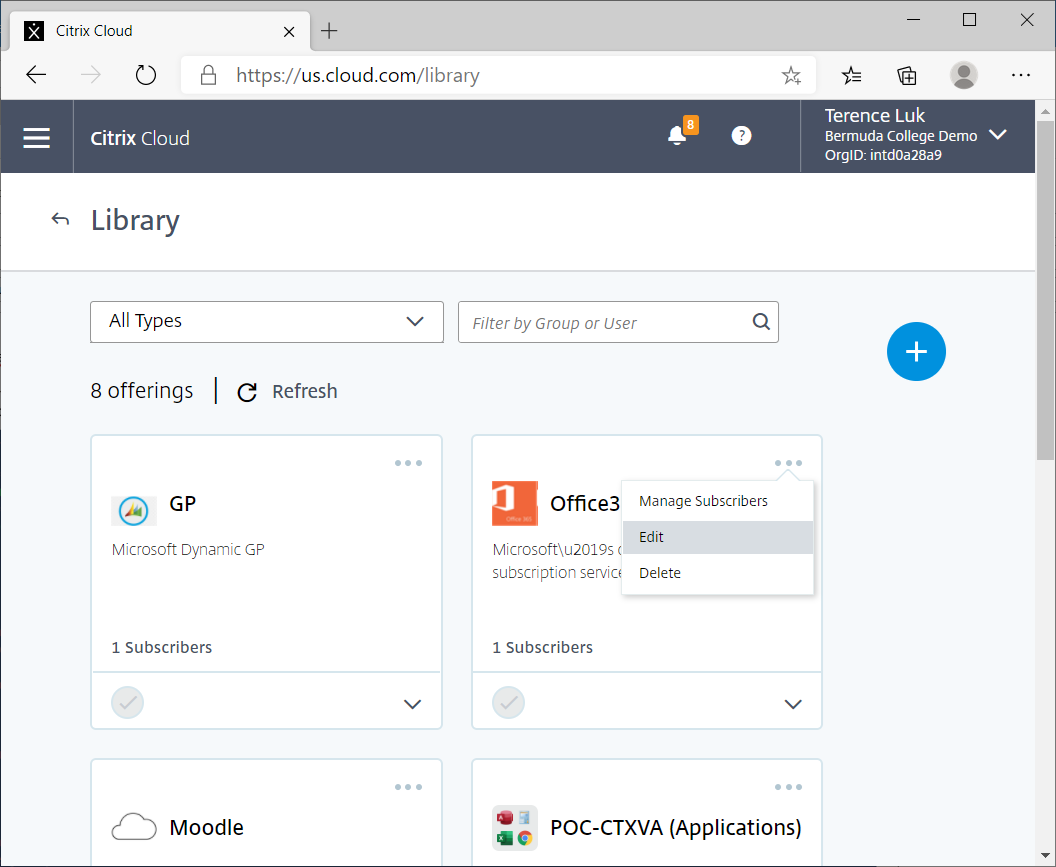
Assuming that the Office 365 SaaS has been published, click into the Library Offerings:
Edit the Office 365 application:
Expand the Single sign on heading and copy the Login URL string:
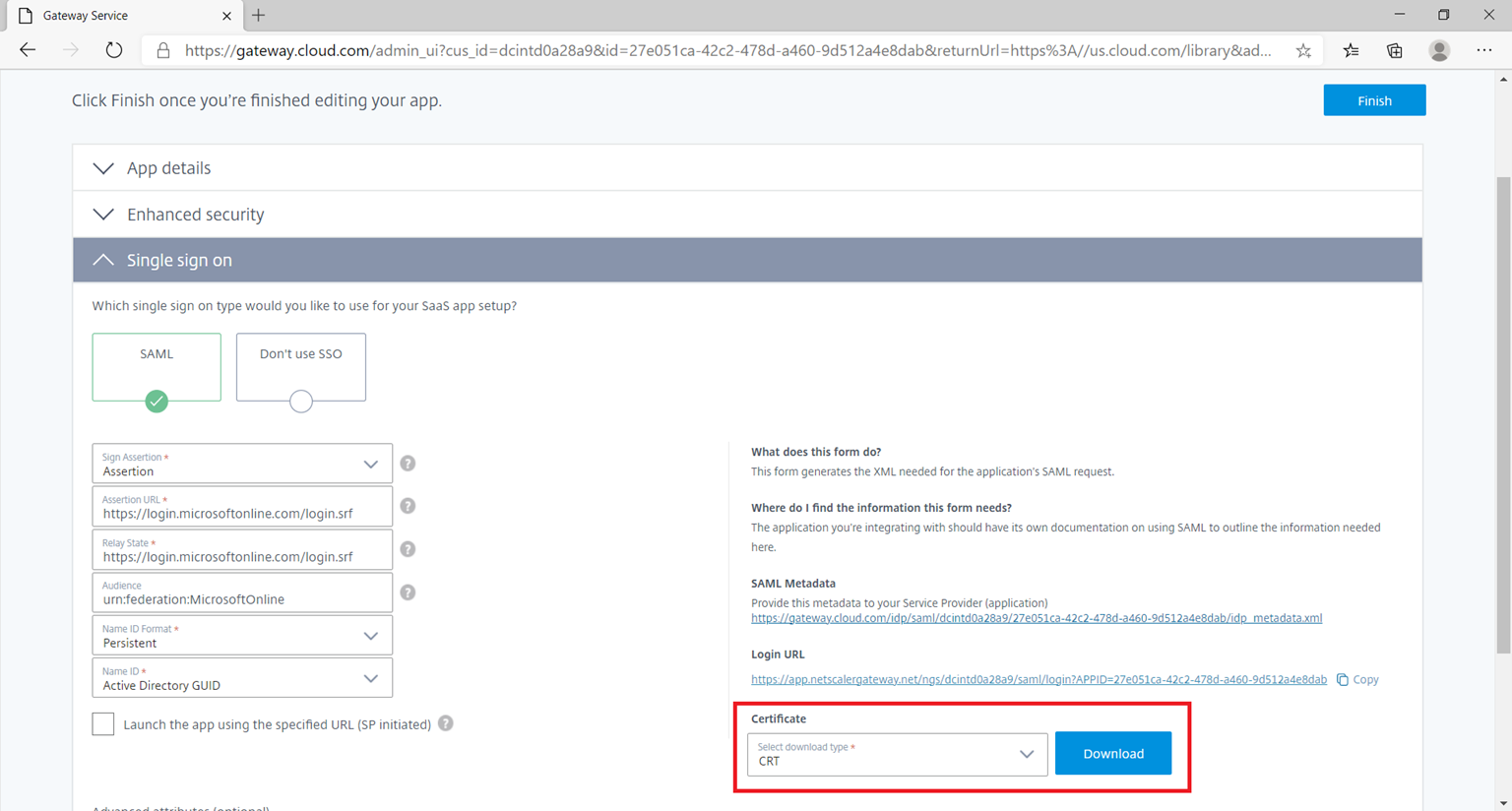
$cert = New-Object System.Security.Cryptography.X509Certificates.X509Certificate2(“c:certdcintd0a28a9_cert.crt”) > The certificate can be confusing for more administrators and the location to download it is in the same place as the Login URL above where you will find the Certificate available to download in multiple formats. Proceed to select CRT and download the file:
$certData = [system.convert]::tobase64string($cert.rawdata) < Leave this without any changes
The following are all the variables with a sample configuration and the items that need to be changed highlighted in red:
$dom = “contoso.com“
$IssuerUri = “https://citrix.com/dcintd0a28a9“
$fedBrandName = “CitrixWorkspace”
$logoffuri = “https://app.netscalergateway.net/cgi/logout”
$uri = “https://app.netscalergateway.net/ngs/dcintd0a28a9/saml/login?APPID=27e051ca-42c2-478d-a460-9d512a4e8dab“
$cert = New-Object System.Security.Cryptography.X509Certificates.X509Certificate2(“c:certdcintd0a28a9_cert.crt”)
$certData = [system.convert]::tobase64string($cert.rawdata)
Step #3 – Configure the Federation between Azure AD and Citrix
Configure the federation with the following PowerShell cmdlet without any changes:
Set-MsolDomainAuthentication -DomainName $dom -federationBrandName $fedBrandName -Authentication Federated -PassiveLogOnUri $uri -LogOffUri $logoffuri -SigningCertificate $certData -IssuerUri $IssuerUri -PreferredAuthenticationProtocol SAMLP
Step #4 – Confirm the Federation between Azure AD and Citrix
Confirm that the federation has been configured by executing the following PowerShell cmdlet:
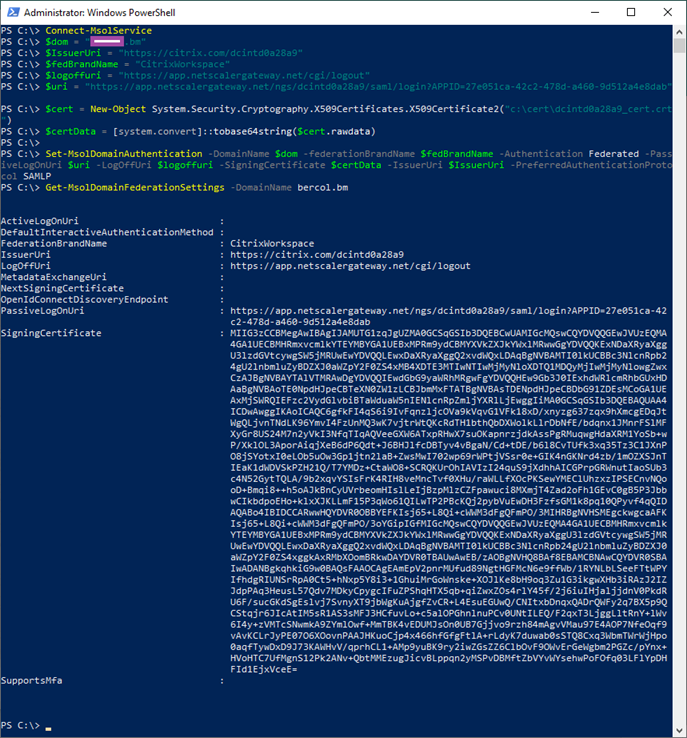
Get-MsolDomainFederationSettings -DomainName contoso.bm
————————————————————————————————————————
The following is a sample output in the PowerShell window after a successful configuration:
With the federation in place, clicking on the Office 365 application will redirect the user to Office 365 to authenticate.