The recent coronavirus pandemic has led many organizations to rush and provide remote access for their employees and with remote connectivity to corporate resources comes with increased security concerns. One of the common questions that I’ve been asked is whether there was a way to lock down Exchange Online so that only corporate assets could access the service. The short answer is yes, but it is important to note that Office 365 was designed to be accessed in many different ways such as an email client (e.g. Outlook), through the web browser (e.g. webmail), or mobile smartphone (e.g. iPhone and Android devices) and tablets. One of the clients I worked with was mainly concerned about Outlook access as once a user has authenticated with an Outlook client and the credentials are cached, the client would automatically connect to Exchange Online as long as the password hasn’t changed. Having gone through the process of setting up Azure’s Conditional Access Policy to achieve the desired access restriction, this post serves to demonstrate the configuration and the experience of a device that is not Hybrid Azure AD Joined.
Prerequisites
The Conditional Access Policy we’ll be configuring is dependent on the devices in domain as being Hybrid Azure AD Joined. I won’t go into the details of how to configure this but will reference the following two documents:
Tutorial: Configure hybrid Azure Active Directory join for managed domains
https://docs.microsoft.com/en-us/azure/active-directory/devices/hybrid-azuread-join-managed-domains
Tutorial: Configure hybrid Azure Active Directory join for federated domains
https://docs.microsoft.com/en-us/azure/active-directory/devices/hybrid-azuread-join-federated-domains
Creating a Conditional Access Policy
Navigate to Azure Active Directory > Security > Conditional Access and click on New policy to create a new Conditional Access Policy:
Configuring the Users or Groups to apply the policy
Fill in a name for the Conditional Access Policy, select Users and groups to configure who this policy will apply to. It would be best to validate the policy does what you intend it to do so either apply it to a single account or a group to test:
Configuring the cloud apps (Exchange Online) to apply the policy
Select Cloud apps or actions > Cloud Apps > Select apps and locate Office 365 Exchange Online:
Configuring the conditions to apply the policy
Select Conditions > Device platforms > Select device platforms and select Windows and macOS:
Note that we are restricting desktops and laptops from accessing Exchange Online and if you were to select Android, iOS and Windows Phone then your mobile devices would no longer be able to connect as they can be Azure AD registered but not Hybrid Azure AD Joined. See the following
What is a device identity?
https://docs.microsoft.com/en-us/azure/active-directory/devices/overview
Select Conditions > Client apps (Preview) > Select the client apps this policy will apply to and select:
- Mobile apps and desktop clients
- Modern authentication clients
- Exchange ActiveSync clients
- Other clients
Configuring the grant access controls to apply the policy
Select Access controls > Grant > Grant access and select Require Hybrid Azure AD joined device:
The Require all the selected controls and Require one of the selected controls configuration doesn’t matter as we are only configuring one control but if you chose to select more than one then you need to decide whether you want the grant access based on all of the requirements or any one of them.
With the policy configured, you can choose to choose Report-only, On, or Off:
Testing the policy with the “What If” feature
What I’ve noticed was that configure the policy to Report-only could be misleading if you’re trying to use the What If feature because it would not report that the configured policy is applied even if the conditions are met. The only way for the What If feature to report that the policy is applied is if I enable the policy.
Switching the policy to On and using the What If to test the policy will allow you to confirm whether the policy is applied as anticipated:
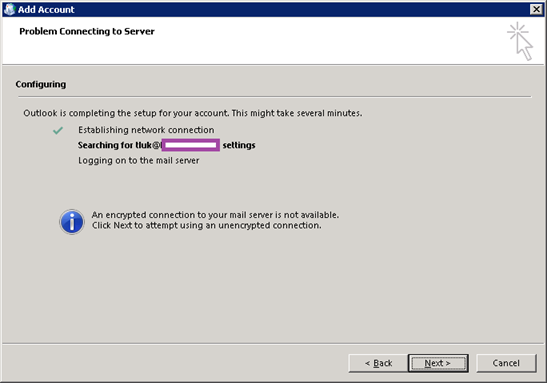
Attempting to access Exchange Online with Outlook 2019 on a PC that is not Hybrid Azure AD Joined
The following is what the experience would look like for a user attempting to use Outlook on a Windows 10 device that is not Hybrid Azure AD Joined.

The user wouldn’t be able to add the mailbox if they attempted to use Outlook 2013 to access Exchange Online:
Important Items to Note
- Configuring such a policy for Exchange Online will also block access to Teams
- This policy does not prevent users from accessing Exchange Online with their mobile or tablet devices and if this is a requirement then I would suggest using Intune