As a follow up for my previous post:
Using Azure Virtual Network Manager to create and manage hub and spoke networks
https://blog.terenceluk.com/using-azure-virtual-network-manager-to-create-and-manage-hub-and-spoke-networks/
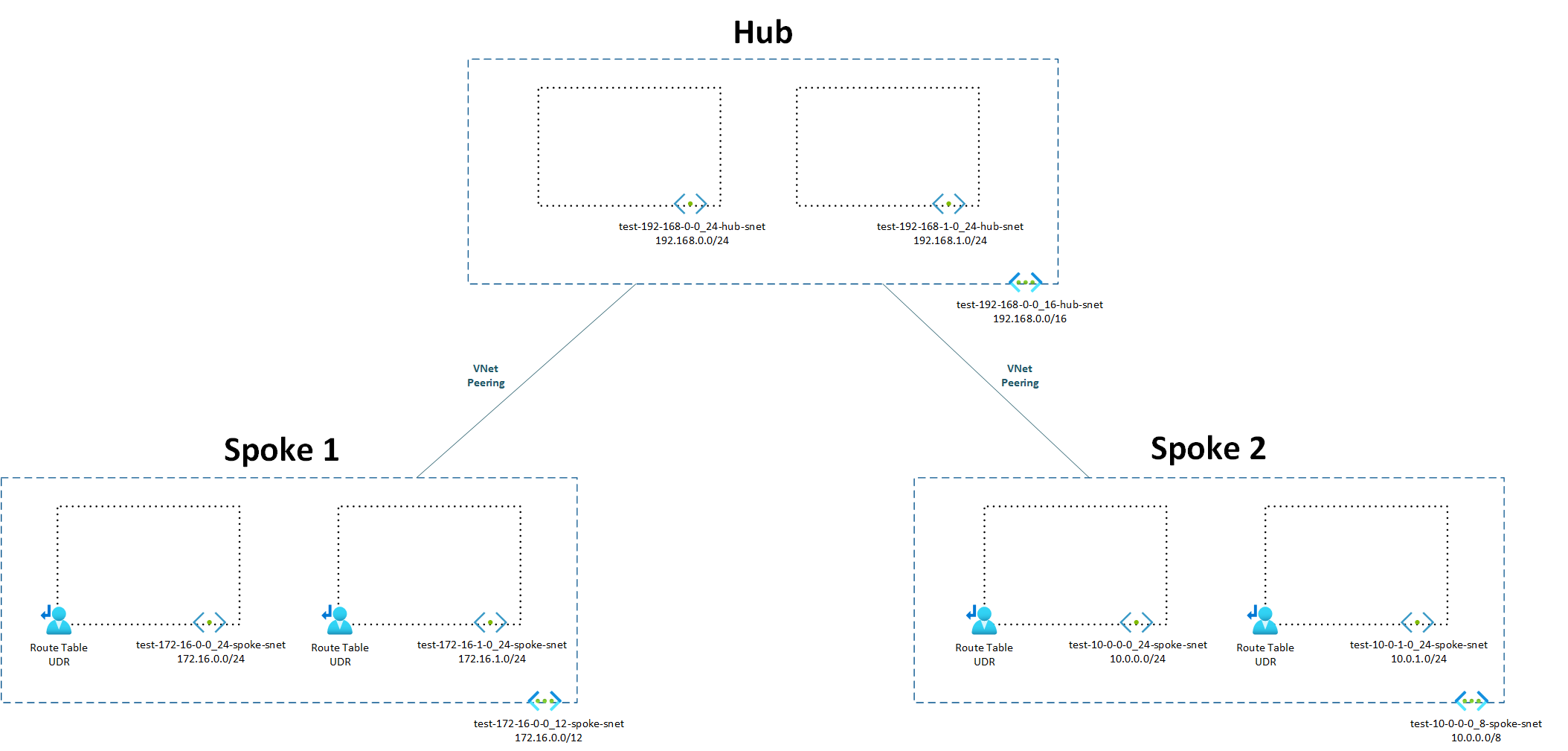
The purpose of this post is to configure Virtual Network Manager‘s new User-Defined-Routes feature that is currently in preview. We’ll be using the same VNet and Subnets that were used to demonstrate configuring VNet peerings for a hub and spoke topology so the corresponding spoke subnets will have Route Tables with UDRs defined as shown in the following diagram:
At the time of this writing, the azurerm_network_manager version 4.7.0 (https://registry.terraform.io/providers/hashicorp/azurerm/latest/docs/resources/network_manager) does not have the ability to configure this so we’ll be using the UI.
Begin by clicking on the link beside Enabled features where Connectivity, SecurityAdmin are displayed:
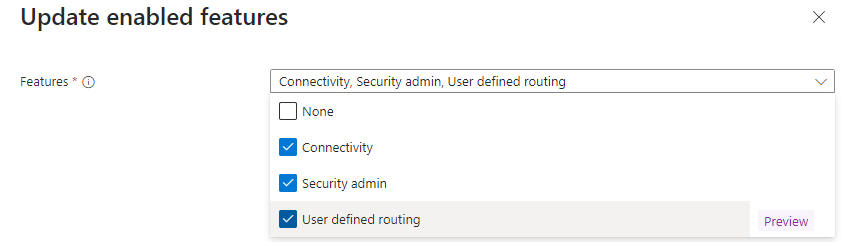
Select the User defined routing in the Features drop down menu:
The label Routing should now be displayed as an enabled feature:
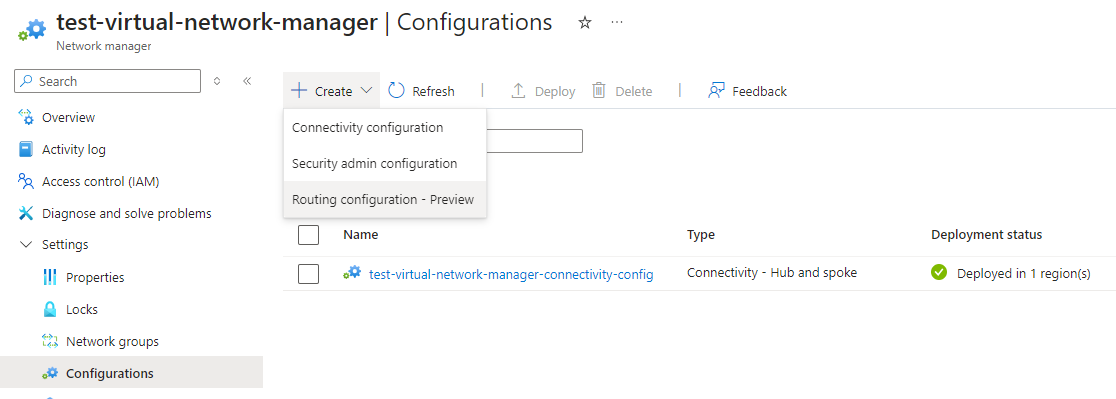
Clicking on the Configurations blade, and then the Create button should now display the option Routing configuration – Preview:
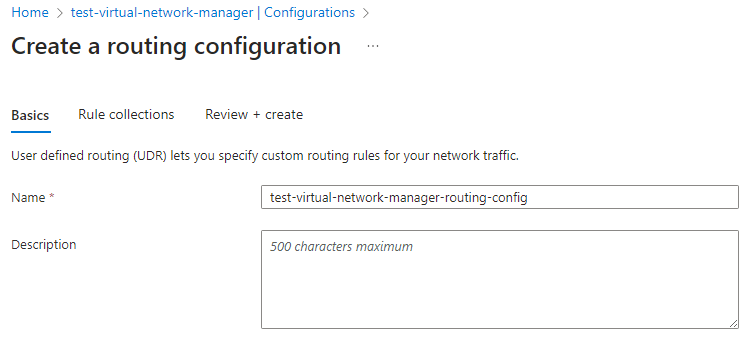
Enter a name for the routing configuration:
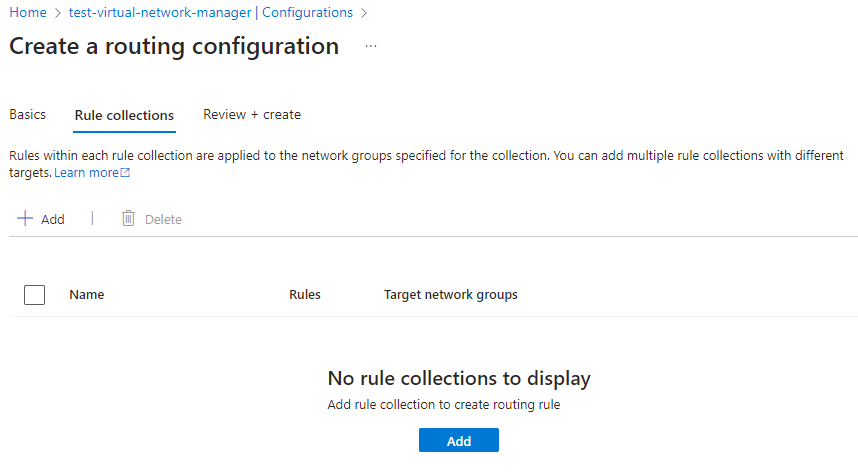
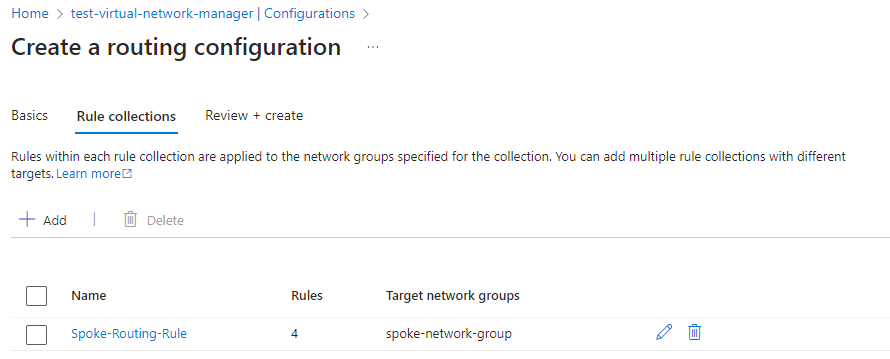
Click on the Rule collections tab then the Add button to being creating collections:
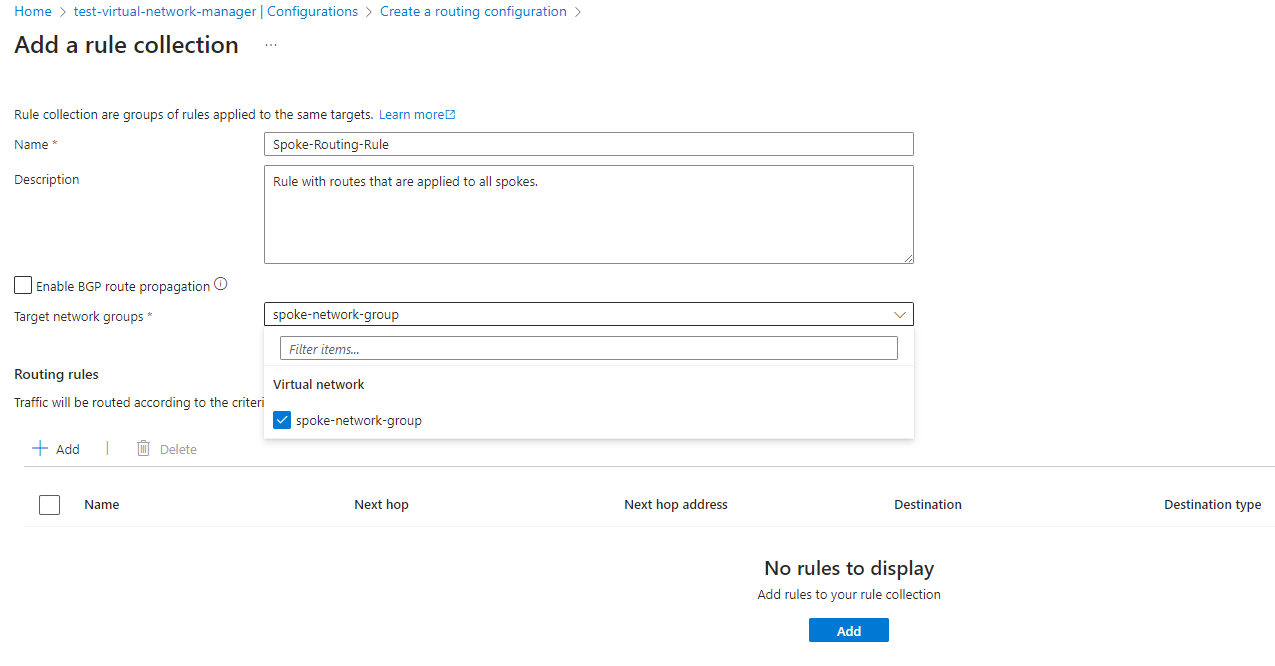
Provide a name for the rule collection, description, and select the target network group to apply rule collection that will have defined routes for traffic flow:
Next, click on the Add button to begin creating the routing rules and you’ll be presented with a form that resembles the one that is presented when you add a new UDR to a Route Table with the following options:
- Name
- Destination type
- IP address
- Service tag
- Destination IP addresses/CIDR ranges
- Next hop type
- Virtual network gateway
- Virtual network
- Internet
- Virtual appliance
- None
- Next hop address
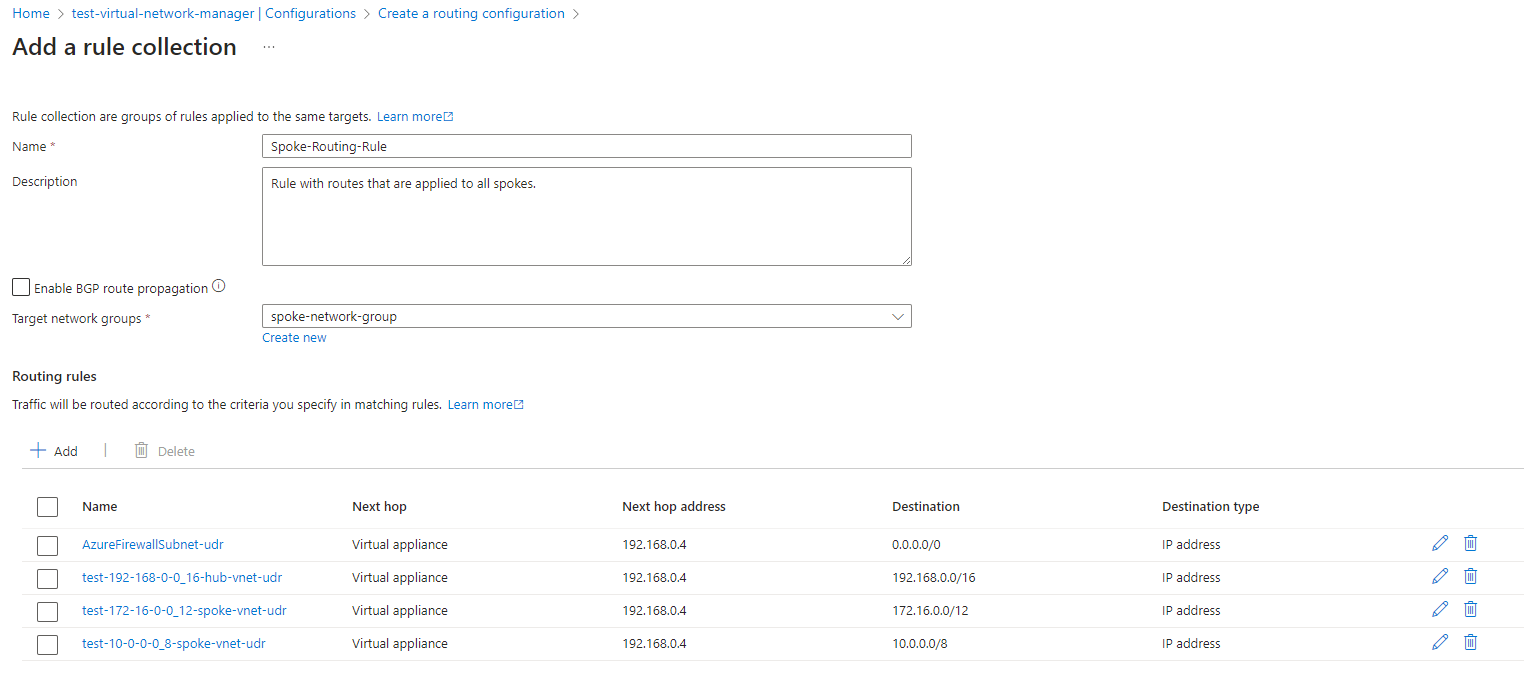
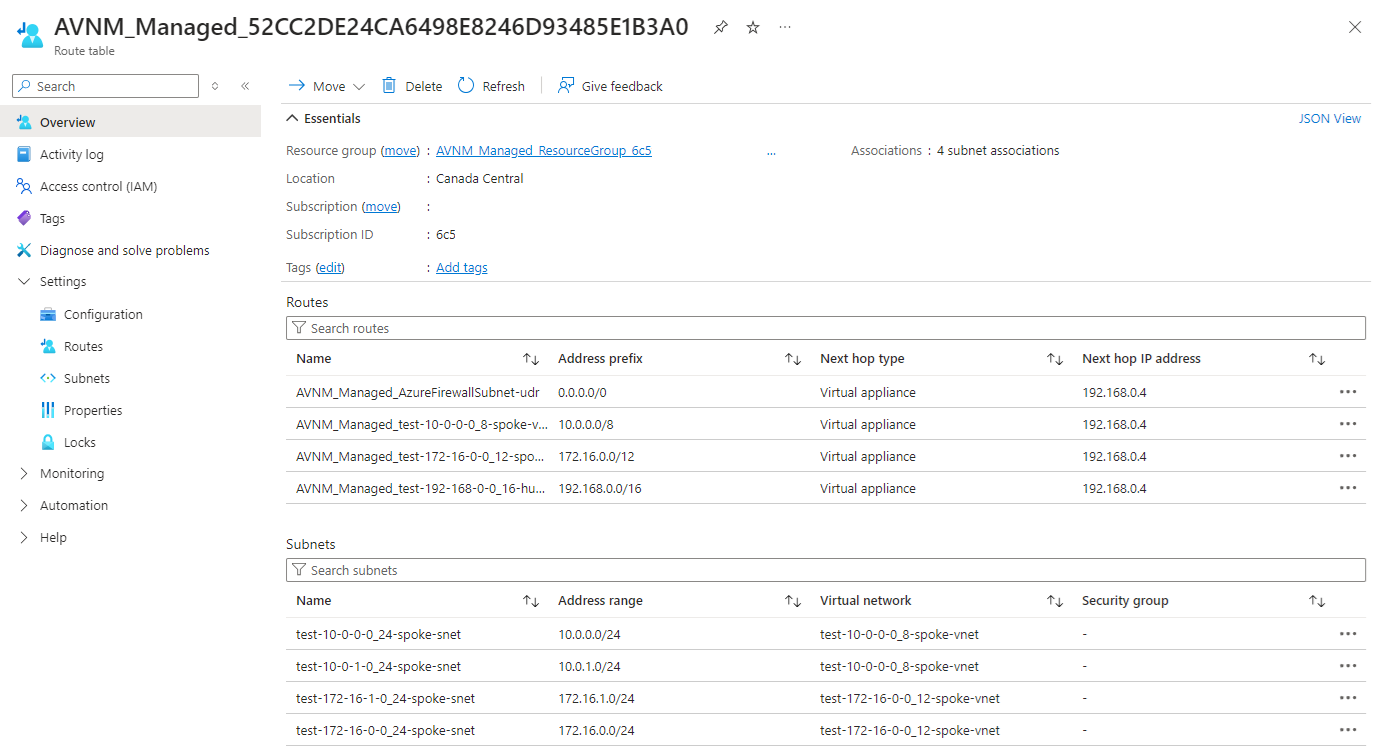
For the purpose of this example, let’s create 4 routes that directs traffic to an Azure Firewall in the Hub Virtual Network:
- Default gateway route
- 192.168.0.0/16
- 172.16.0.0/12
- 10.0.0.0/8
Click on the Add button and you should see the new collection created:
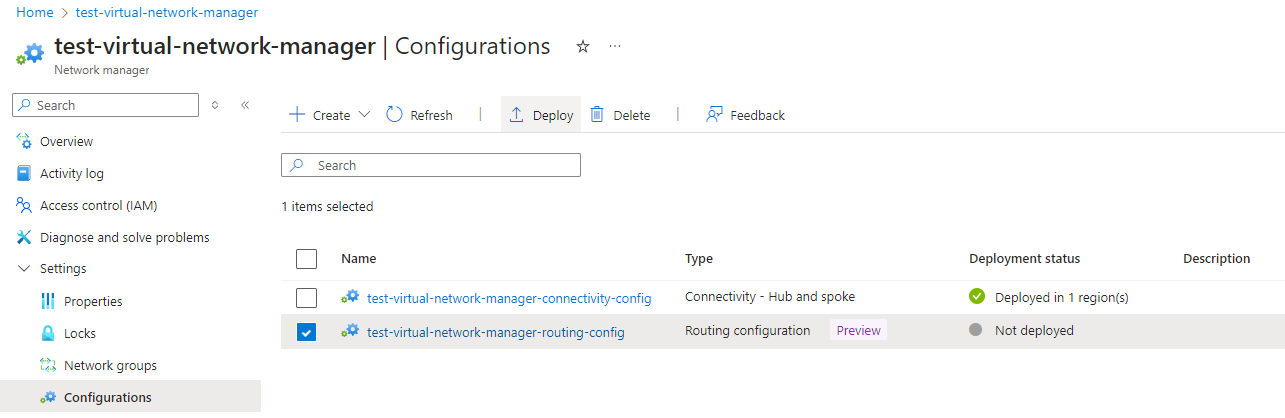
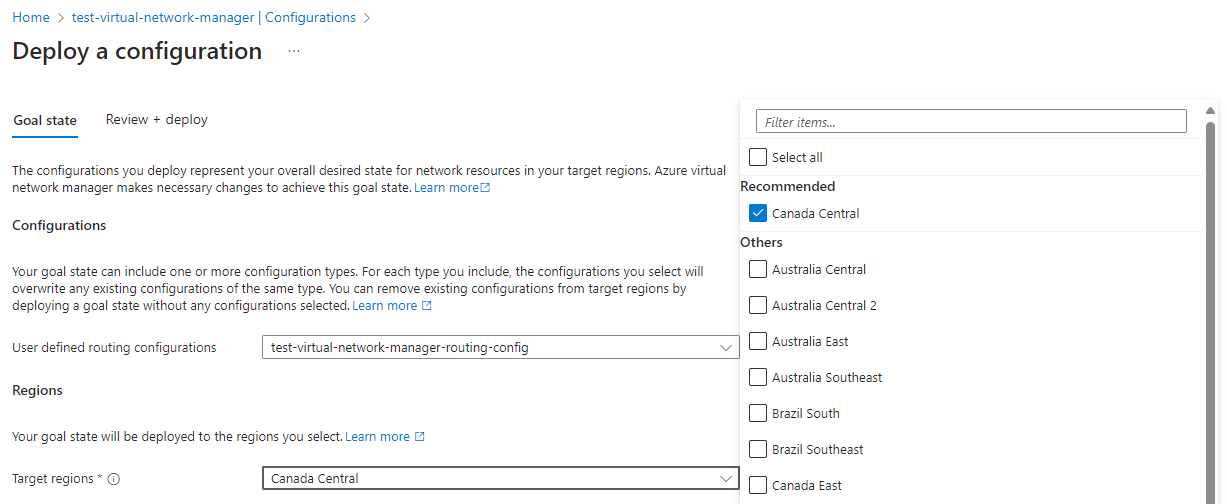
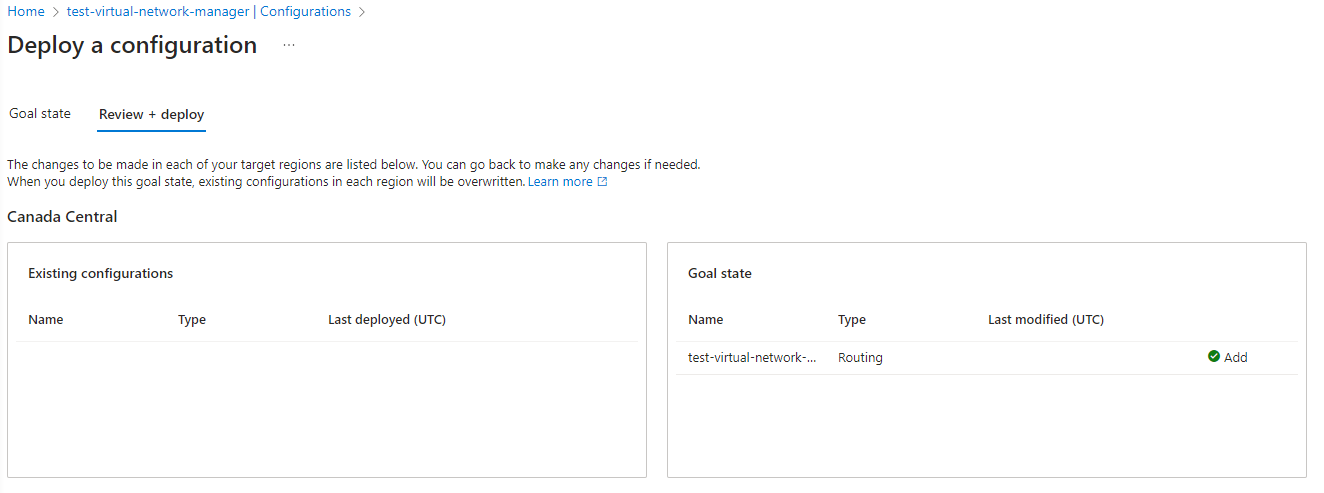
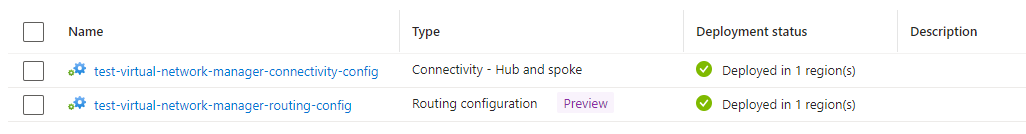
Proceed to create the configuration and you’ll see it displayed in the Configurations as Not deployed. Select the configuration and click on the Deploy button to deploy the new configuration:
Once the configuration has been deployed:
You should now see a Virtual Network Manager Route Table with UDRs created and applied to the subnets in the target network group virtual networks:
A few items to note about this example configuration:
- Routing all private networks to the firewall will mean that even communication within the same subnet will be sent to the firewall and back down. An example of this is if a VM with the IP address 172.16.0.5/24 tries to reach 172.16.0.6/24, the traffic will be directed to the firewall and back down. There isn’t an easy way change this without breaking out the subnets into their own VNets and changing the routes. While it is possible to add a specific route for a subnet’s own subnet to route via “Virtual Network”, it defeats the purpose using Virtual Network Manager to automate the deploy and management of the routes.
- I’ve tried adding a custom route directly into a AVNM managed route table and even if you redeploy the configuration, the custom route is maintained.
Hope this helps anyone who may be looking for a demo of this preview feature. I look forward to the day where we can dynamically put a rule into these AVNM rule collections that allow to either add a route to handle routing a subnet’s own subnet to stay within the virtual network or provide a feature in the Route Table to achieve the same result.