Recent Visitor 84
As a follow up to my previous post:
I wanted to demonstrate the full end-to-end deployment of an API Management deployed into an internal virtual network that is published by an Application Gateway. Microsoft actually provides a series of PowerShell cmdlets for the deployment as described here:
Integrate API Management in an internal virtual network with Application Gateway
https://learn.microsoft.com/en-us/azure/api-management/api-management-howto-integrate-internal-vnet-appgateway
https://learn.microsoft.com/en-us/azure/api-management/api-management-howto-integrate-internal-vnet-appgateway
The intent was to then convert the deployment to Terraform code and add it to my repo.
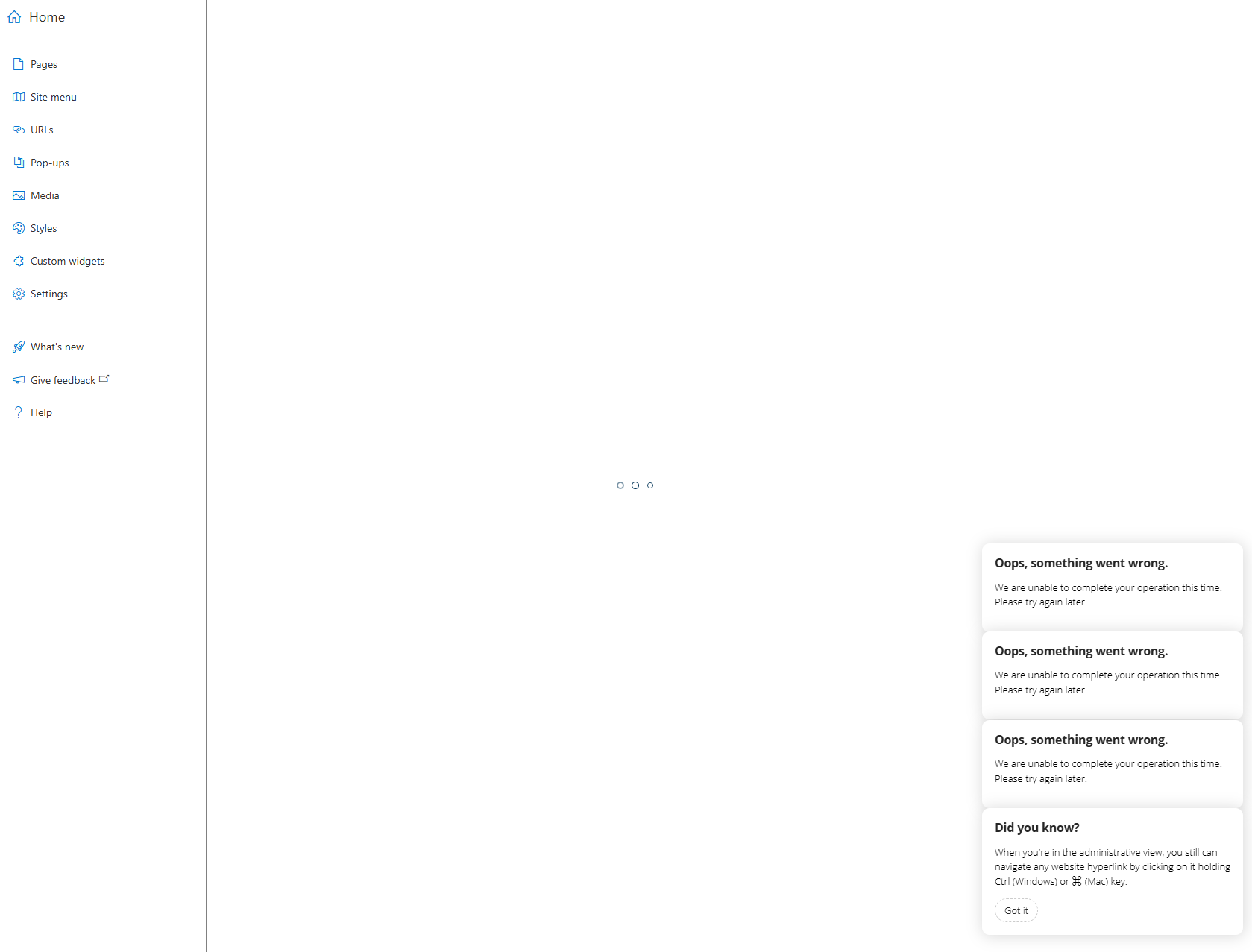
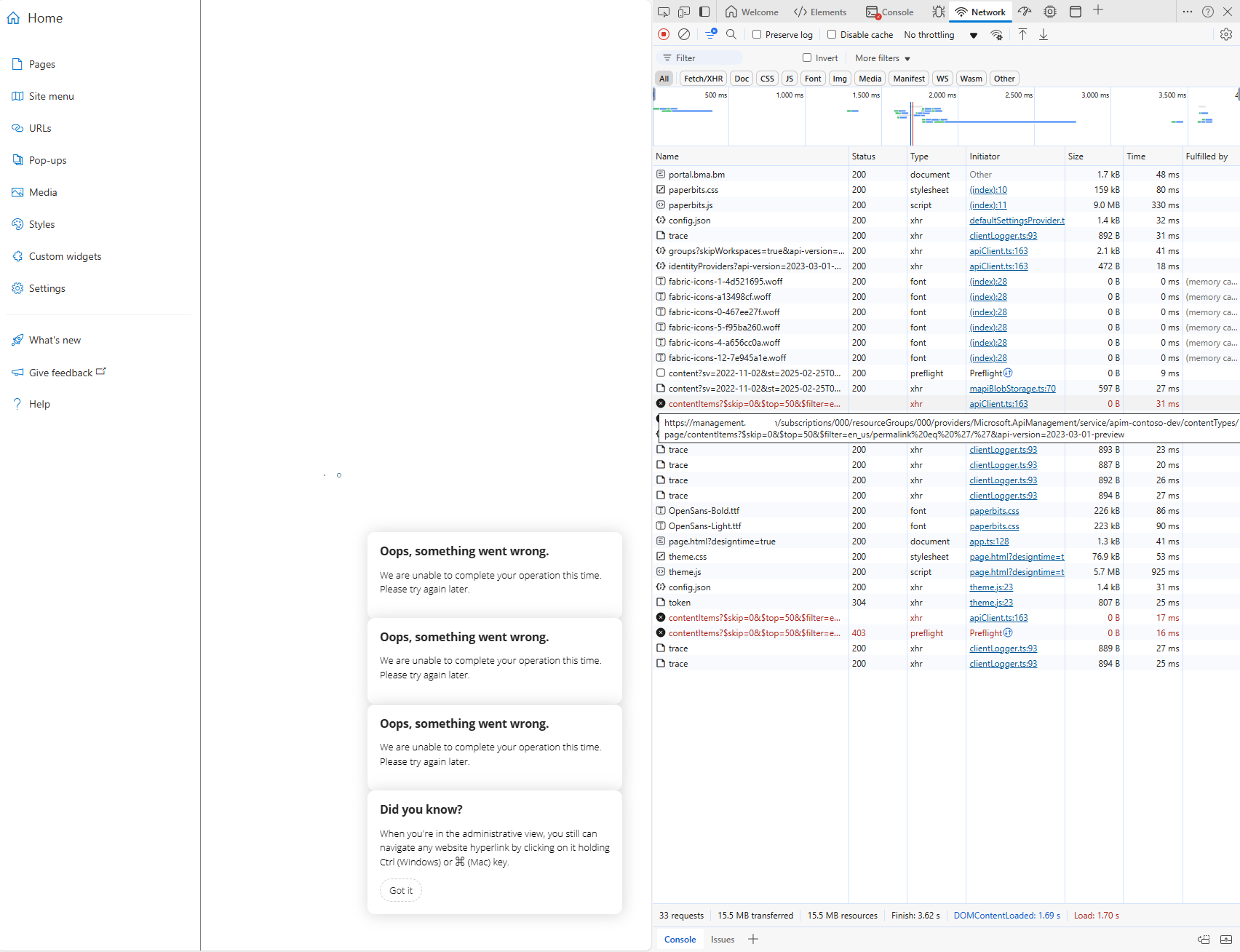
What I noticed was the after successfully deploying the resources, my developer portal exhibited a similar behavior as my previous post where the page would not load:
The only difference is that the error message was more generic with:
Oops, something went wrong.
We are unable to complete your operation this time.
Please try again later.
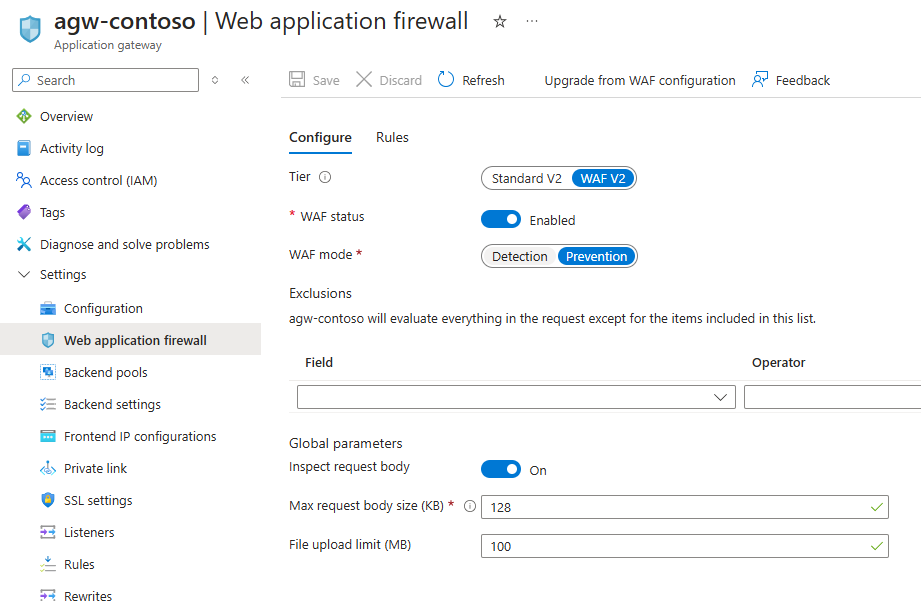
Given the deployment was straight from the Microsoft documentation, I was confused as to why the developer portal wasn’t working even though the API gateway did. As a quick test, I had a look at the WAF settings and decided to change it from Prevention to Detection:
Surprisingly, the developer portal started to work:
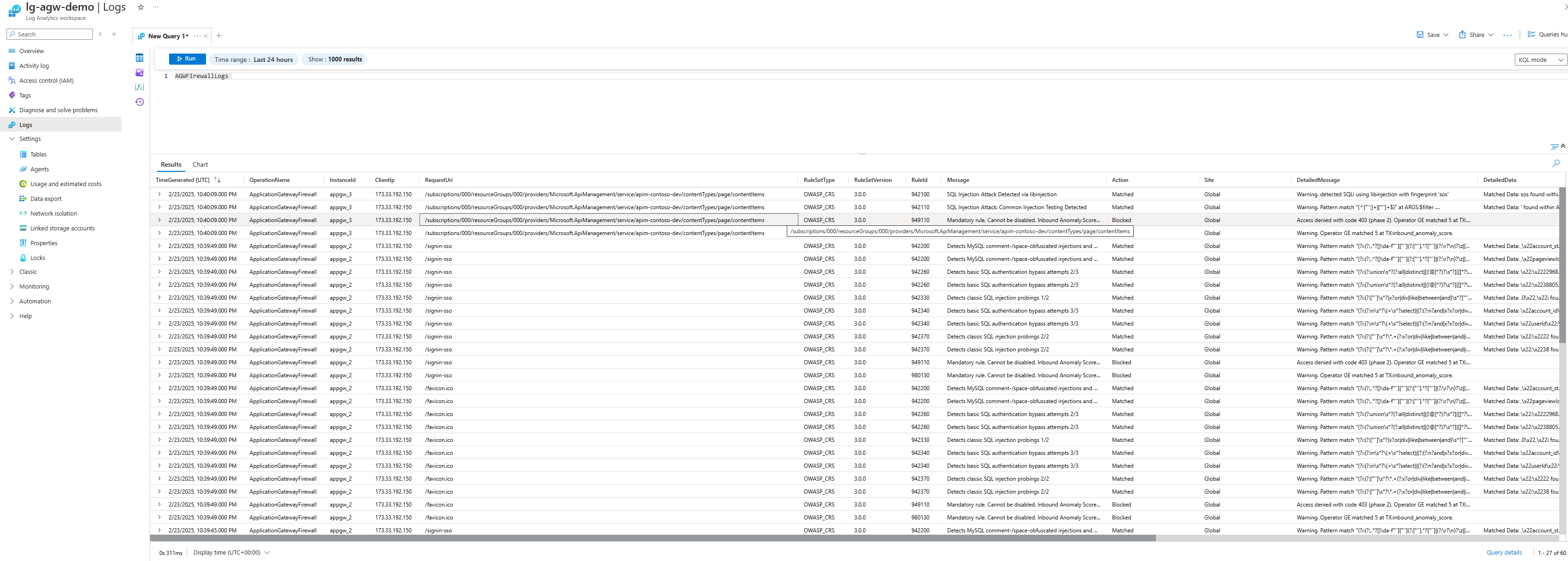
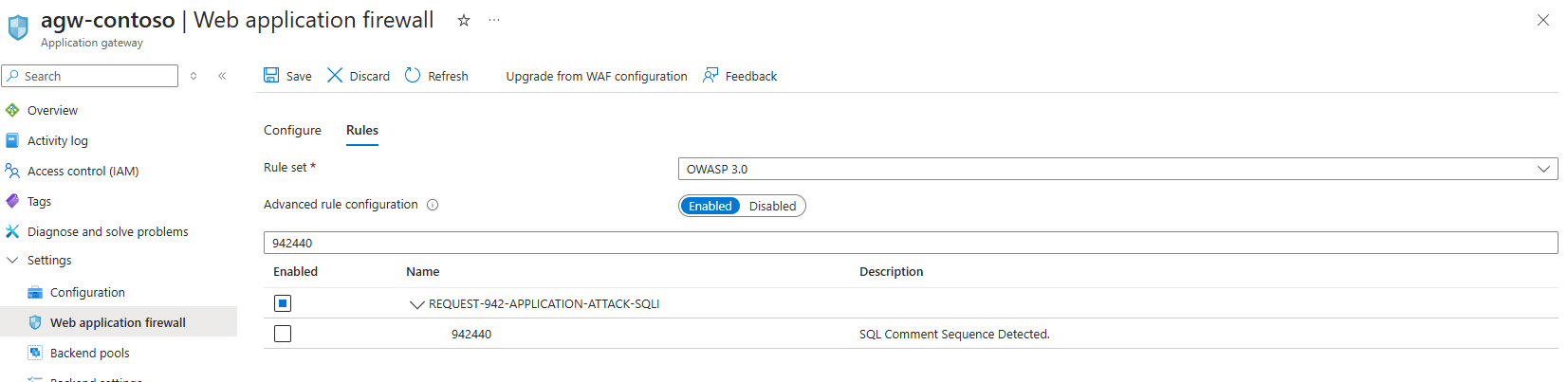
Knowing this is likely a WAF issue, I went ahead and configured Diagnostic Settings for the Application Gateway to review the logs and immediately saw the following entries:
Rule ID: 942100
RequestUri: /subscriptions/000/resourceGroups/000/providers/Microsoft.ApiManagement/service/apim-contoso-dev/contentTypes/page/contentItems
Message: SQL Injection Attack Detected via libinjection
Rule ID: 942110
RequestUri: /subscriptions/000/resourceGroups/000/providers/Microsoft.ApiManagement/service/apim-contoso-dev/contentTypes/page/contentItems
Message: SQL Injection Attack: Common Injection Testing Detected
Rule ID: 042200
RequestUri: /signin-sso
Message: Detects MySQL comment-/space-obfuscated injections and backtick termination
I’ve worked with WAF issues in the past and understood that the traffic between the Application Gateway and the APIM was triggering rules such as SQL Injections and eventually scoring an Anomaly score past 5, which results in the traffic being blocked. More detail on how scoring works can be found in the following documentation:
Web Application Firewall – Anomaly scoring
https://learn.microsoft.com/en-us/azure/web-application-firewall/ag/application-gateway-crs-rulegroups-rules?tabs=drs21#anomaly-scoring
https://learn.microsoft.com/en-us/azure/web-application-firewall/ag/application-gateway-crs-rulegroups-rules?tabs=drs21#anomaly-scoring
Attempting to perform a trace from within the a browser will also show that the management endpoint is blocked:
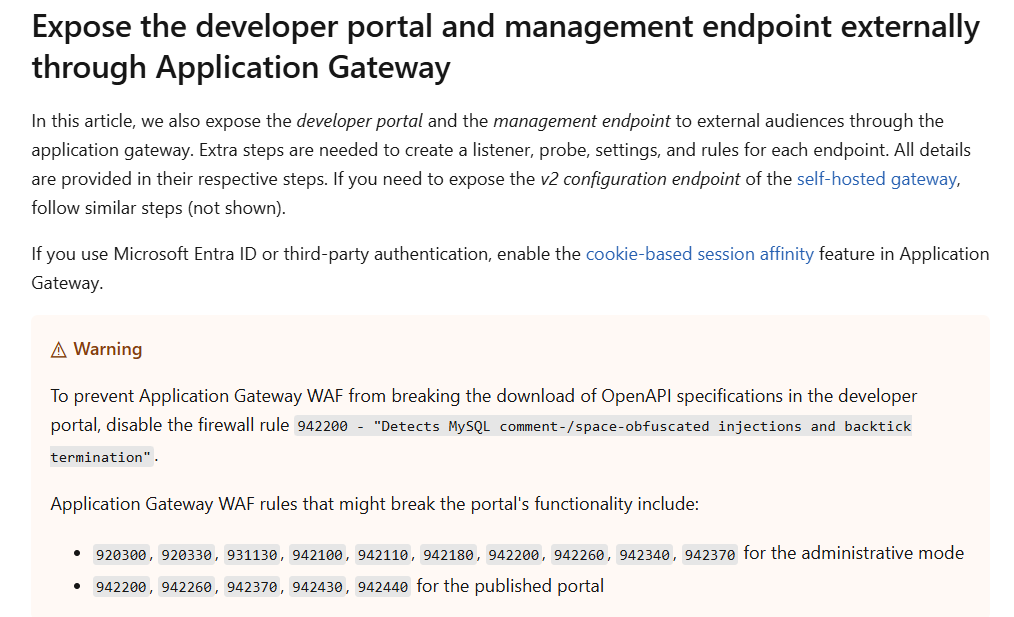
After going through documentation again, I realized that it was mentioned that the Application Gateway WAF can break down APIM’s portal functionality:
Expose the developer portal and management endpoint externally through Application Gateway
https://learn.microsoft.com/en-us/azure/api-management/api-management-howto-integrate-internal-vnet-appgateway#expose-the-developer-portal-and-management-endpoint-externally-through-application-gateway
https://learn.microsoft.com/en-us/azure/api-management/api-management-howto-integrate-internal-vnet-appgateway#expose-the-developer-portal-and-management-endpoint-externally-through-application-gateway
To my surprise, there are a total of 16 rules that can cause access issues to the developer portal. Taking the instructions in the warning literally, it sounds like Microsoft recommends to disable all of these rules.
- 942200
- 920300
- 920330
- 931130
- 942100
- 942110
- 942180
- 942200
- 942260
- 942340
- 942370
- 942200
- 942260
- 942370
- 942430
- 942440
Once I’ve gone ahead and disabled all of the 16 rules, the page began to load:
I gave the alternatives a lot of thought before proceeding to disable the rules and could not think of a better way workaround so I’m open to suggestions in the comments section if there is a better way.