One of the common behaviors with using a WAF, whether it’s an F5, NetScaler, or, in this case, an Application Gateway, is that the IP address that the web service see’s from inbound traffic will always be the IP address of the Application Gateway. This is expected because the Application Gateway receives the traffic on behalf of the web service it is protecting and will establish (also known as proxy) a new connect to the web service. To quickly demonstrate this, I’ve set up an Application Gateway that publishes IIS on a Windows Server 2022. The following diagram demonstrates the traffic flow:
As shown above, the inbound IP address of my home network is 173.33.192.150 but when the traffic arrives to the IIS service on the Windows Server, it appears as the App Gateway’s internal IP address of 10.12.2.4 and 10.12.2.5.
The following are the IIS log entries located in the C:\inetpub\logs\LogFiles\W3SVC1 folder:
Note that the fields we’re interested in are:
- s-ip <– Server IP Address
- c-ip <– Client IP Address
The fields natively logged by IIS aren’t very useful when traffic is proxied over from the App Gateway as there is no easy way to determine what was the true originating client IP. While it is possible to try and reconcile these logs with the App Gateway logs through timestamps, it’s not practical.
Prior to working with the App Gateway, I configured many Citrix NetScalers as load balancers and WAFs, and wrote a blog post back in 2021 about this issue:
How to configure Citrix ADC / NetScaler to forward client Source IP to Exchange Server 2019 / 2016 or any IIS application
https://terenceluk.blogspot.com/2021/06/how-to-configure-citrix-adc-netscaler.html
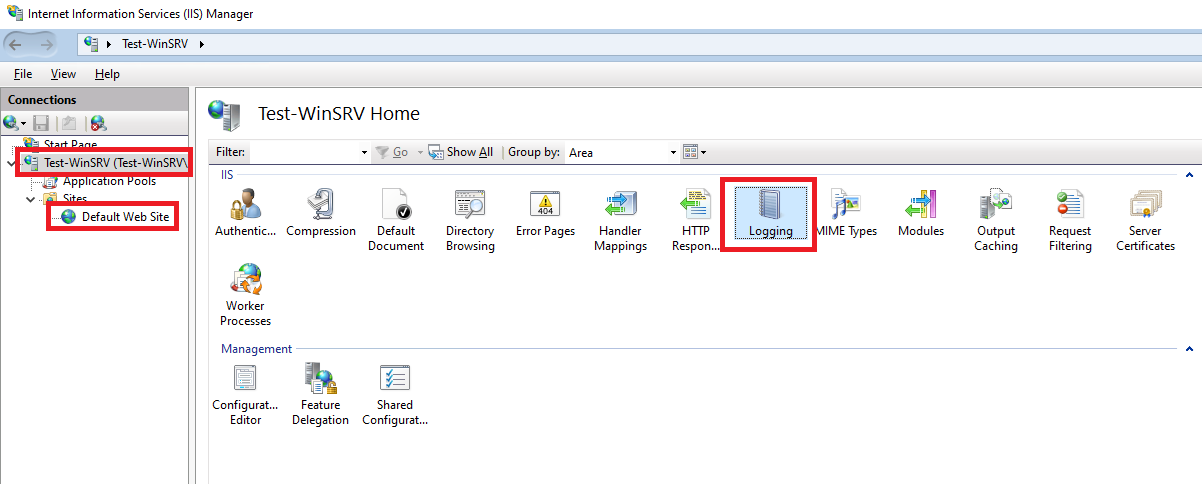
As with the NetScaler in my old blog post, the Application Gateway has and by default already forwards the X-Forwarded-for header to service it publishes and proxies traffic older. In the case of a Windows Server IIS service, all we need to do is added the X-Forwarded-for header as a field so it is written to the logs. To configure this, simply either click on the IIS web server or the website object in IIS:
Then click on Select Fields… under Log File > Format:
Add the X-Forwarded-for custom field as such:
Apply the changes and you should now see the new field in the newly created IIS log:
Note that the Application gateway inserts six additional headers to all requests before it forwards the requests to the backend. These headers are:
- x-forwarded-for
- x-forwarded-port
- x-forwarded-proto
- x-original-host
- x-original-url
- x-appgw-trace-id
More detail about the above can be found in the following Microsoft documentation: https://learn.microsoft.com/en-us/azure/application-gateway/how-application-gateway-works#modifications-to-the-request
Hope this helps anyone who may be looking for this information.