Those who have come across my previous post about Microsoft Lync 2010 and Avaya RCC integration:
Lync Server 2010 & Avaya RCC Integration? Not yet as of June 7, 2011
https://blog.terenceluk.com/lync-server-2010-avaya-rcc-integration/
… may remember that I was working with a client who had an Avaya AES server that was more than 2 versions behind the current offered by Avaya which cause the new Lync deployment project I was in to come to a screeching halt. Fast forward to almost a year later, we finally got approval for the new upgrade licenses and have thus upgraded the AES (Application Enablement Services) server to the latest version: r6-1-2-32-0.
I was extremely anxious to get back into the client’s office to retry getting the RCC going and also managed to find an Avaya document which provides step-by-step instructions:
Implementation notes on Integration of Avaya Aura Application Enablement ® Services with Microsoft® Lync® 2010 Server.
https://support.avaya.com/css/P8/documents/100144425
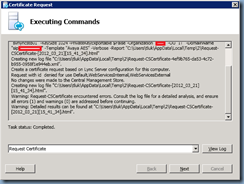
As straight forward as the instructions were, I did run into an issue from the beginning where I was required to request a certificate with the Lync certificate request tool. The challenge here was that I had to use to the certificate request tool to request a certificate with a customized template that included Client Authentication (the regular Web Server template only included Server Authentication). What I immediately found was that as soon as I tried to request the certificate for the Lync standard server, I would get the following error:
Request CertificateRequest-CSCertificate -New -Type Default,WebServicesInternal,WebServicesExternal -CA “svrcert02.contoso.internalcontoso Re” -Country BM -State “Hamilton” -City “Hamilton” -FriendlyName “svrlyncstd01” -KeySize 1024 -PrivateKeyExportable $False -Organization “contoso” -OU “IT” -DomainName “sip.contosore.com” -Template “Avaya AES” -Verbose -Report “C:UserstlukAppDataLocalTemp2Request-CSCertificate-[2012_03_21][15_41_34].html”Creating new log file “C:UserstlukAppDataLocalTemp2Request-CSCertificate-4ef9b765-da53-4c72-b955-0958f1e944eb.xml”.Create a certificate request based on Lync Server configuration for this computer.Request with id denied for use Default,WebServicesInternal,WebServicesExternalNo changes were made to the Central Management Store.Creating new log file “C:UserstlukAppDataLocalTemp2Request-CSCertificate-[2012_03_21][15_41_34].html”.Warning: Request-CSCertificate encountered errors. Consult the log file for a detailed analysis, and ensure all errors (1) and warnings (0) are addressed before continuing.Warning: Detailed results can be found at “C:UserstlukAppDataLocalTemp2Request-CSCertificate-[2012_03_21][15_41_34].html”.
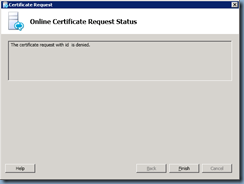
The certificate request with id is denied.
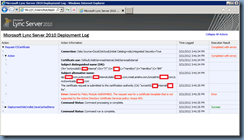
Those who have come across the The certificate request with id is denied. error would know that this error message usually includes number after the id but in my case, it didn’t. Reviewing the Microsoft Lync Server 2010 Deployment Log gave me a bit more information as to why the request failed but solution to the problem wasn’t obvious:
Error: Denied by Policy Module 0x80094800, The request was for a certificate template that is not supported by the Active Directory Certificate Services policy: Avaya AES.
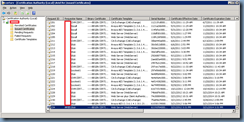
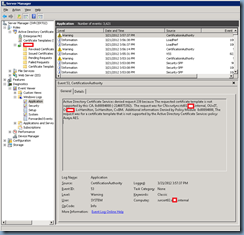
I’ve also gone ahead to review the certificate authority’s issued certificates and noticed that no certificate was issued after the error was thrown:
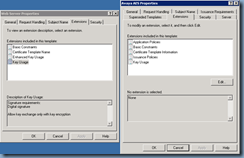
From here, I went ahead to review the settings of the template and noticed that the Minimum key size for the template was set to 2048 and not 1024 as the guide instructs you to use so I went ahead and changed it:
I also went ahead to compare the Web Server template with the Avaya AES custom template I created and other than a few extra properties, I didn’t notice anything out of the ordinary:
Reviewing the certificate authority’s event logs showed a warning message that was similar to the error I got from the Microsoft Lync Server 2010 Deployment Log:
To confirm that it was indeed the certificate template I was using which was the problem, I went ahead to try and use the Lync certificate tool to issue a certificate but to use the default Web Server template and noticed that the request would complete without errors.
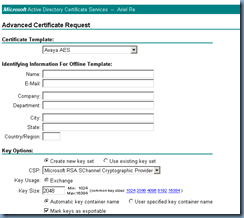
After fiddling around with the encryption bit from 1024 to 2048 and other settings I could think of, I gave up and went directly to the certificate authority’s /certsrv webpage to try and request the certificate from there:
Note that the settings I used which is worth mentioning are:
CSP: Microsoft RSA SChannel Cryptographic Provider
Key Size: 2048
One I got the certificate to successfully issue, I went ahead to assign the certificate to the Lync pool, completed the PowerShell cmdlets to create the static routes, trusted application pools, etc and immediately got RCC going.
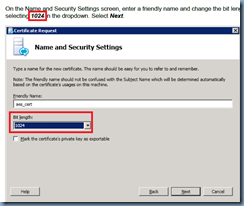
Note that I am aware that the document clearly states the following for the certificate:
On the Name and Security Settings screen, enter a friendly name and change the bit length by
selecting 1024 in the dropdown. Select Next.
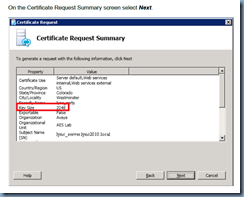
Yet shows that the Key Size in the summary screen as 2048:
I’m not exactly sure what key size we’re supposed to use by the instructions appear to suggest it’s 1024 and not 2048. The only concern I initially had was that the Avaya AES server does not support key sizes larger than 1024 but since RCC is working, I supposed it does.
Hope this helps anyone out there who may come across this problem.


![clip_image001[4] clip_image001[4]](https://lh5.ggpht.com/-AYTX3YCj270/T24FsE--4uI/AAAAAAAAN34/Gw8_W5fY-6k/clip_image0014_thumb.png?imgmax=800)
![clip_image001[6] clip_image001[6]](https://lh3.ggpht.com/-6VE6sz8nqAg/T24FthXWQOI/AAAAAAAAN4I/fXcYkSf2MK0/clip_image0016_thumb.png?imgmax=800)


3 Responses
Thank you for this post. I am currently upgrading an OCSR2 environment with AES RCC to Lync 2010 with AES RCC. This came in handy.
Great blog, thanks Terence.
I seem to be missing something here. On the AES, I've imported the CA trusted cert for my domain's Microsoft CA. That is all I have done on the AES side.
On the Lync side, I have applied a new cert that uses the Client/Server auth, at 1024 bits, and successfully applied it via the Lync Deployment Wizard.
Successfully ran all of the Lync Command Shell commmands for static route and application pool trust.
Can't get AES and Lync to talk. When I run a diagnostic test on AES for TR/87, the first test for TR/87 TRANSPORT, it comes back with "TR/87 Self Test Result" and a BACK button, and nothing else.
Am I supposed to add another certificate to AES, besides the one for my internal CA? If so, how ?
Any info will be most appreciated. Thanks!
Ron Piecyk
I had the same issue.
I got the error request denied.
changing 1024 2048 did not work.
my solution was to publish the default webserver certificate!