Problem
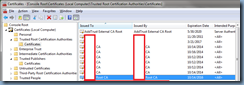
You have previously deployed multiple Active Directory Enterprise Root Certificate Authorities in the domain and because you’ve had to redeploy the CA a few times using the same name, you notice that your domain joined workstations and servers now have multiple root certificates stored in the Trusted Root Certification Authorities certificate store:
Solution
I was unsure as to whether there was an easy way to remove these root certificates in the Trusted Root Certification Authorities certificate store so I went ahead and reached out to our Microsoft partner support and the response I received was to review the following KB article:
How to remove a trusted Certificate Authority from computers in the domain
https://support.microsoft.com/kb/555894
The article’s instructions appear to be pretty straight forward as it demonstrates the user of a batch file and script to automate the process:
The first step was to download the following SDK:
Download: Platform SDK Redistributable: CAPICOM
https://www.microsoft.com/en-us/download/details.aspx?id=25281
The problem I immediately noticed was that there were a few typos in the script (namely the removeca.vbs filename):
… and when I finally launched it on a Windows 7 64-bit desktop, it would error out with:
C:TempRemoveCA>c:windowssystem32regsvr32 capicom.dll /s
C:TempRemoveCA>cscript remove.vbs
Microsoft (R) Windows Script Host Version 5.8
Copyright (C) Microsoft Corporation. All rights reserved.
C:TempRemoveCAremove.vbs(13, 1) Microsoft VBScript runtime error: ActiveX com
ponent can’t create object: ‘CAPICOM.Store’
C:TempRemoveCA>
Since it looks like Microsoft suggests to use logon scripts to clean up these root certificates, I simply went ahead and looked into using the certutil.exe command to remove certificates and then created a simplified batch file to remove the entries.
The first step was to determine the right syntax and it took quite a bit of time because I did not find the following TechNet article too straight forward:
https://technet.microsoft.com/en-us/library/cc732443(v=ws.10).aspx
In any case, the proper syntax is the following:
certutil -delstore -enterprise root “<Serial number>”
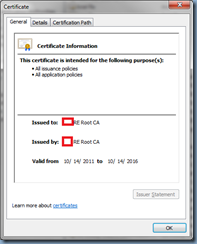
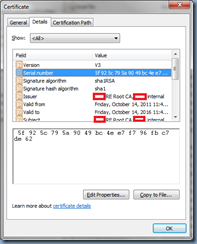
The command above will remove the certificate located in the Trusted Root Certification Authorities Computer Store of the workstation you execute this command. To determine the serial number, simply open up the certificate’s properties and navigate to the Details tab, then select the Serial number field as such:
Copy the serial number and slot it into the end of the command added quotes:
certutil -delstore -enterprise root “5f 92 5c 79 5a 90 49 bc 4e e7 f7 96 fb c7 de 62”
Once the command successfully executes (it doesn’t take long), you will see the following output:
C:>certutil -delstore -enterprise root “5f 92 5c 79 5a 90 49 bc 4e e7 f7 96 fb c7 de 62”
root
Deleting Certificate 5
CertUtil: -delstore command completed successfully.
C:>
Proceed with testing this on a workstation with all of the certificates you intend on deleting one after another and copying and pasting the command into notepad as such:
certutil -delstore -enterprise root “55 8c 2e b5 cc ae 92 89 41 5b 25 33 f7 ef 6c 2e”
certutil -delstore -enterprise root “79 7a f4 a9 9e 81 79 ba 44 b5 91 bc 85 d0 b0 df”
certutil -delstore -enterprise root “58 35 46 65 2a 6e 47 93 48 31 62 3a 49 83 eb 24”
certutil -delstore -enterprise root “27 77 84 a8 49 39 3c b2 4e c7 e9 47 8f 1b 52 60”
certutil -delstore -enterprise root “58 ed e0 1e 68 68 06 a2 4b d3 14 5d 11 f2 7a 85”
certutil -delstore -enterprise root “2e cc 73 20 fe 05 0a 88 44 d8 fb 3a 96 1a 99 5a”
certutil -delstore -enterprise root “25 a5 76 4c c6 fb ca 8a 4d c1 bd 46 e4 9c 3c 37”
certutil -delstore -enterprise root “60 15 e8 95 34 09 ff a3 42 16 26 9a fc fd 67 29”
certutil -delstore -enterprise root “5f 92 5c 79 5a 90 49 bc 4e e7 f7 96 fb c7 de 62”
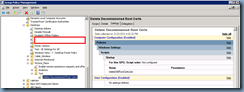
Once you have removed all of the certificates, save the notepad file as a batch file then take it to another workstation to execute verifying that all of the certificates you intend on deleting are removed. Once you have validated that the batch file works as intended, proceed with creating a new GPO in your Active Directory and apply it to the OU with the workstations you want the certificates removed:
Note that I applied this batch file to the following policy setting:
Computer Configuration –> Policies –> Windows Settings –> Scripts –> Startup
Hope this helps anyone looking for a way to clean up their root certificates.

![clip_image001[4] clip_image001[4]](https://lh6.ggpht.com/-FSmaoNoUbw8/T8DvtzCGSsI/AAAAAAAAP1k/D7UADcGvODU/clip_image001%25255B4%25255D_thumb.png?imgmax=800)
![clip_image001[6] clip_image001[6]](https://lh6.ggpht.com/-_8r8Ky7axyw/T8Dvv0lOy-I/AAAAAAAAP10/6w1FBRjy6RU/clip_image001%25255B6%25255D_thumb.png?imgmax=800)
![clip_image001[8] clip_image001[8]](https://lh6.ggpht.com/-MzjnXrDhGVM/T8Dv4NApxdI/AAAAAAAAP2k/r-8XNVSd7gE/clip_image001%25255B8%25255D_thumb.png?imgmax=800)
![clip_image001[10] clip_image001[10]](https://lh6.ggpht.com/-aeSUorFrBsU/T8Dv6Tm4-1I/AAAAAAAAP20/W6uoh8afSq8/clip_image001%25255B10%25255D_thumb.png?imgmax=800)


8 Responses
This really helped me. Thanks! So much simpler than Microsoft's official method.
This is great but I have left over Server and Client authentication certificates issued by the old CA to the computer name of the machine in the personal computer certificates store how do you remove those globally? All the serial numbers are different on each machine.
Sorry sir, can certutil delstore have command force without interacting with user? because when i tried, thats command show pop up windows and klik yes to delete the certificate.
Thanks
That works for clean-up in every machine, but, does it avoid to be replicated in new machines added to the domain if the script is deactivated after clean-up of existing machines?
Thank you
Excellent post. For those who might be having problems removing the certs via the GPO start-up script, you may need to add a bit more or less than just the "-enterprise root" arguments.
For example …
certutil -delstore root "aa bb cc dd"
certutil -delstore TrustedPublisher "aa bb cc dd"
certutil -delstore -enterprise root "aa bb cc dd"
certutil -delstore -enterprise TrustedPublisher "aa bb cc dd"
certutil -delstore -GroupPolicy root "aa bb cc dd"
certutil -delstore -GroupPolicy TrustedPublisher "aa bb cc dd"
Hi,
I referenced your article for server 2008 r2 onwards and it worked perfectly. I have a similar need for this but across a network running XP machines which have been restricted to run as if it were a thin client.
Can you assist at all? Any help/advice would be much appreciated.
Hi
Thank you for the valuable information
(・ω・)b
Hey,
Can a certificate be removed using thumbprint?
Thanks,