One of the most common configurations I’ve done for clients with NetScaler Appliances is to allow administration with Active Directory accounts since the nsroot account should be protected and logging in with individual user accounts can provide auditing trails. I’ve found that NetScaler documentation from Citrix is usually a hit and miss as most still demonstrate configurations with version 8 or older even though version 10 have so many of the configuration settings reorganized into different nodes. This post serves to provide a clear demonstration of configuring AD authentication with version 10 or higher.
Begin by logging into the NetScaler administration console via the NSIP:
Navigate to System > Authentication > LDAP and click on the Servers tab:
Continue by clicking on the Add button to create Active Directory Domain Controller server objects:
Note that from here, you have the option of creating Domain Controller objects that use regular LDAP on port 389 which does not encrypt traffic or LDAPS on port 636 which does. Using LDAPS requires a CA and configuration on the domain controllers. For more information, see my previous post here:
Configure LDAPs an Active Directory Domain Controller for LDAP over SSL Connections
https://terenceluk.blogspot.co.uk/2013/10/configure-ldaps-active-directory-domain.html
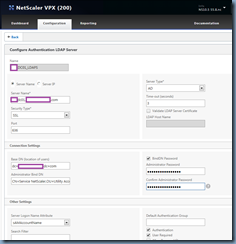
Proceed by filling in the following:
Name: <Logical name representing the domain controller>
Server Name: <You can user a DNS name or IP address>
Security Type: <PLAINTEXT, TLS or SSL>
Port: <This gets automatically assigned>
Server Type: <AD>
Time-out (seconds): <Default of 3 seconds)>
Base DN (location of users): <Where you want the NetScaler to start looking for accounts. I usually just put the root of the domain in>
Administrator Bind DN: <The Distinguished Name of the service account that will be used to authenticate the user>
BindDN Password: <The password of the Administrator Bind DN account>
Server Logon Name Attribute: <sAMAccountName>
Create as many domain controller objects as required:
Proceed by clicking on the Policies tab and then the Add button to create an authentication policy using the server objects that were created:
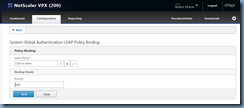
In the Create Authentication LDAP Policy window, provide a logical name for the policy then select a domain controller server object that was created for the Server field, type in ns_true for the Expression and then click on the Create button:
Repeat the same procedure for the other domain controllers:
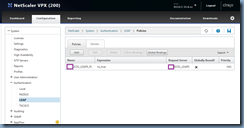
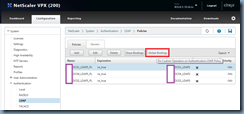
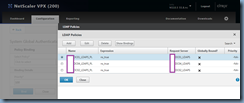
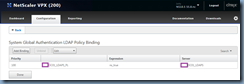
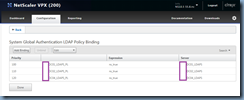
With the policies created, click on the Global Bindings button:
Add a policy created earlier and assign an appropriate priority:
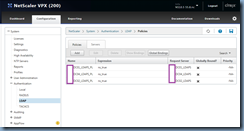
With the first policy binded, repeat the same procedure and add the other created policies by clicking on the Add Binding button:
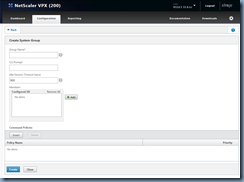
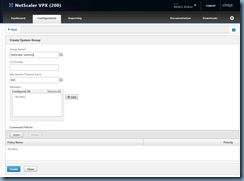
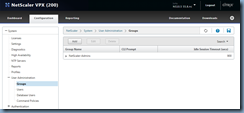
Next, navigate to System > User Administration > Groups and click on the Add button to create a group object in the NetScaler to represent the Active Directory group in the authenticating domain:
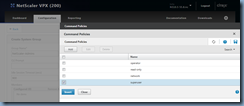
Type in the group name of the Active Directory group and make sure it is *exactly* the same then click on the Insert button under Command Policies:
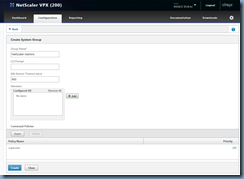
In the Command Policies window, select superuser if you would like to grant nsroot permissions then click on the Insert button:
With superuser permissions granted, proceed and click on the Create button to complete the creation of the System Group:
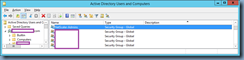
Ensure that your Active Directory group is named exactly the same:
You should now be able to log into the NetScaler appliance with domain<username> as the User Name with the appropriate AD password.









One Response
One caution with adding mutliple LDAP policies pointing to mutliple domain controllers in the same domain is premature account lockout. If you mistype your password, the failed logon attempt is recorded with each of the domain controllers you add here. To mitigate this, load balance your LDAP.