I’ve recently worked with a client to troubleshoot RADIUS authentication issues between their Cisco Nexus as a RADIUS client and their Microsoft Windows 2012 R2 NPS (Network Policy Server) server as the RADIUS server and after determining the issue, the client asked me why I never wrote a blog post on the steps that I took to troubleshoot issues like these so this post serves as a way to demonstrate the process.
The first place I look when a RADIUS client is not able to successfully authenticate against Active Directory through a Windows 2012 R2 NPS server is the directory:
C:WindowsSystem32LogFiles
Where the following IN####.log (YYMM) logs are found:
Each of the IN logs contain connection attempts from RADIUS clients over a month so if I am troubleshooting RADIUS issues that are occurring at that point in time then I would:
- Open the latest log file
- Move the cursor to the last entry of the log file
- Use the Find feature (CTRL + F) and search for the RADIUS client’s IP address
The following is an example of an entry from a client with an IP address 10.92.9.11 that I am troubleshooting:
Being able to locate the IP address of the problematic client in the log above allows me to:
- Verify that the client is indeed reaching out to NPS server with the RADIUS request
- Determine the exactly time of the request
Item #2 is important to have because the next step is to open the event logs of the NPS server and navigate into the Security events:
Those who have ventured into these logs would know that a lot of entries are written into this log especially if it was a domain controller. The timestamp obtained in the log file above will allow us to navigate to the section of the logs where we’ll find the relevant entries. Since the error message on the Nexus login was an “invalid password or user name”, I went ahead and filtered the Security events with the Keywords: Audit Failure:
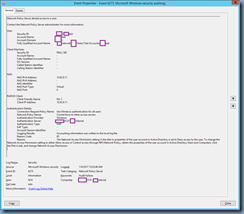
Navigating to the entries with the same timestamp displays event IDs 6273 and 4625 entries that provide information about why the login failed:
Network Policy Server denied access to a user.
Contact the Network Policy Server administrator for more information.
User:
Security ID:
domainargotest
Account Name:
argotest
Account Domain:
domain
Fully Qualified Account Name:
domain.internal/domain/Users/Test Accounts/argotest
Client Machine:
Security ID:
NULL SID
Account Name:
–
Fully Qualified Account Name:
–
OS-Version:
–
Called Station Identifier:
–
Calling Station Identifier:
–
NAS:
NAS IPv4 Address:
10.92.9.11
NAS IPv6 Address:
–
NAS Identifier:
–
NAS Port-Type:
Virtual
NAS Port:
0
RADIUS Client:
Client Friendly Name:
NX-1
Client IP Address:
10.92.9.11
Authentication Details:
Connection Request Policy Name:
Use Windows authentication for all users
Network Policy Name:
Connections to other access servers
Authentication Provider:
Windows
Authentication Server:
SVRARDC01.domain.internal
Authentication Type:
PAP
EAP Type:
–
Account Session Identifier:
–
Logging Results:
Accounting information was written to the local log file.
Reason Code:
65
Reason:
The Network Access Permission setting in the dial-in properties of the user account in Active Directory is set to Deny access to the user. To change the Network Access Permission setting to either Allow access or Control access through NPS Network Policy, obtain the properties of the user account in Active Directory Users and Computers, click the Dial-in tab, and change Network Access Permission.
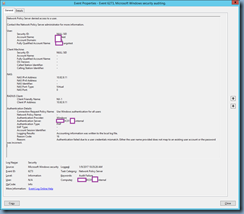
Network Policy Server denied access to a user.
Contact the Network Policy Server administrator for more information.
User:
Security ID:
NULL SID
Account Name:
argotest
Account Domain:
domain
Fully Qualified Account Name:
domainargotest
Client Machine:
Security ID:
NULL SID
Account Name:
–
Fully Qualified Account Name:
–
OS-Version:
–
Called Station Identifier:
–
Calling Station Identifier:
–
NAS:
NAS IPv4 Address:
10.92.9.11
NAS IPv6 Address:
–
NAS Identifier:
–
NAS Port-Type:
Virtual
NAS Port:
0
RADIUS Client:
Client Friendly Name:
NX-1
Client IP Address:
10.92.9.11
Authentication Details:
Connection Request Policy Name:
Use Windows authentication for all users
Network Policy Name:
–
Authentication Provider:
Windows
Authentication Server:
SVRARDC01.domain.internal
Authentication Type:
PAP
EAP Type:
–
Account Session Identifier:
–
Logging Results:
Accounting information was written to the local log file.
Reason Code:
16
Reason:
Authentication failed due to a user credentials mismatch. Either the user name provided does not map to an existing user account or the password was incorrect.
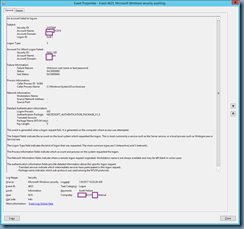
An account failed to log on.
Subject:
Security ID:
SYSTEM
Account Name:
SVRARDC01$
Account Domain:
domain
Logon ID:
0x3E7
Logon Type: 3
Account For Which Logon Failed:
Security ID:
NULL SID
Account Name:
argotest
Account Domain:
domain
Failure Information:
Failure Reason:
Unknown user name or bad password.
Status:
0xC000006D
Sub Status:
0xC000006A
Process Information:
Caller Process ID:
0x384
Caller Process Name:
C:WindowsSystem32svchost.exe
Network Information:
Workstation Name:
Source Network Address:
–
Source Port:
–
Detailed Authentication Information:
Logon Process:
IAS
Authentication Package:
MICROSOFT_AUTHENTICATION_PACKAGE_V1_0
Transited Services:
–
Package Name (NTLM only):
–
Key Length:
0
This event is generated when a logon request fails. It is generated on the computer where access was attempted.
The Subject fields indicate the account on the local system which requested the logon. This is most commonly a service such as the Server service, or a local process such as Winlogon.exe or Services.exe.
The Logon Type field indicates the kind of logon that was requested. The most common types are 2 (interactive) and 3 (network).
The Process Information fields indicate which account and process on the system requested the logon.
The Network Information fields indicate where a remote logon request originated. Workstation name is not always available and may be left blank in some cases.
The authentication information fields provide detailed information about this specific logon request.
– Transited services indicate which intermediate services have participated in this logon request.
– Package name indicates which sub-protocol was used among the NTLM protocols.
– Key length indicates the length of the generated session key. This will be 0 if no session key was requested.
Reviewing the events above should give you more insight as to why the authentication process is failing but note that the information could be misleading at times as if you read all of the events above, it would seem like the authentication process is failing because the user name and password is incorrect but the problem in the situation above was that an incorrect group was placed into the actual NPS policy thus causing the authentication to fail.
Hope this helps anyone who may be looking for information on how to troubleshoot NPS authentication issues.







2 Responses
Looking for a solution to this, tough problem to solve as it is happening on Network Policy Server in Windows 2016 using RADIUS with Cisco Meraki. Hopefully more solutions will follow.
This comment has been removed by the author.