Problem
I was recently asked to configure Zoom with ADFS as per the following documentation:
Configuring Zoom With ADFS
https://support.zoom.us/hc/en-us/articles/202374287-Configuring-Zoom-With-ADFS
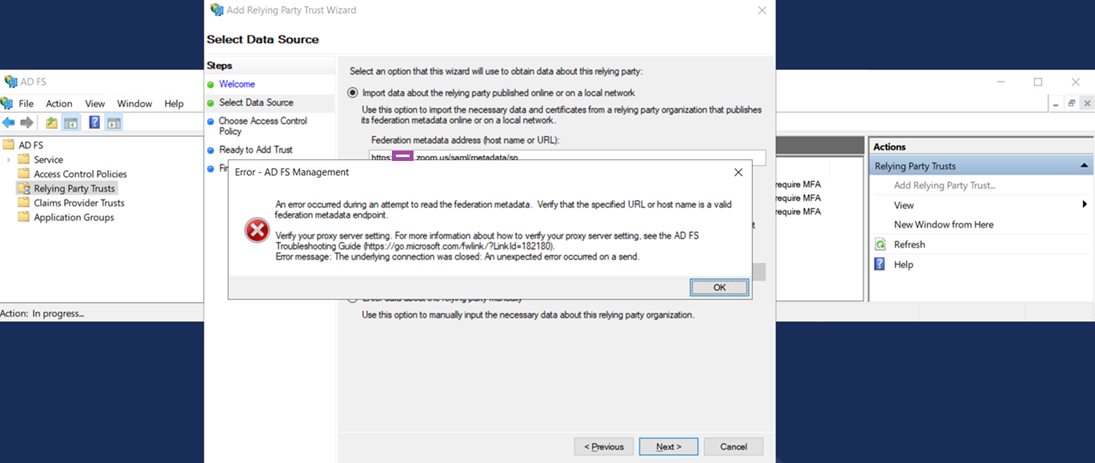
… and was not able to complete the process because the following error was displayed when importing the federation metadata:
An error occurred during an attempt to read the federation metadata. Verify that the specified URL or host name is a valid federation metadata endpoint.
Searching on the internet earlier this year did not return any posts that helped resolve this issue and opening up a ticket with Zoom had us wait months before we received a reply (escalated by the client’s account manager). To give Zoom some credit, the support engineer who reached out to us was extremely quick with response and very helpful. I am unsure if searching for this error will yield the KB he forwarded to us so this post serves to help anyone who may run into the same problem.
Solution
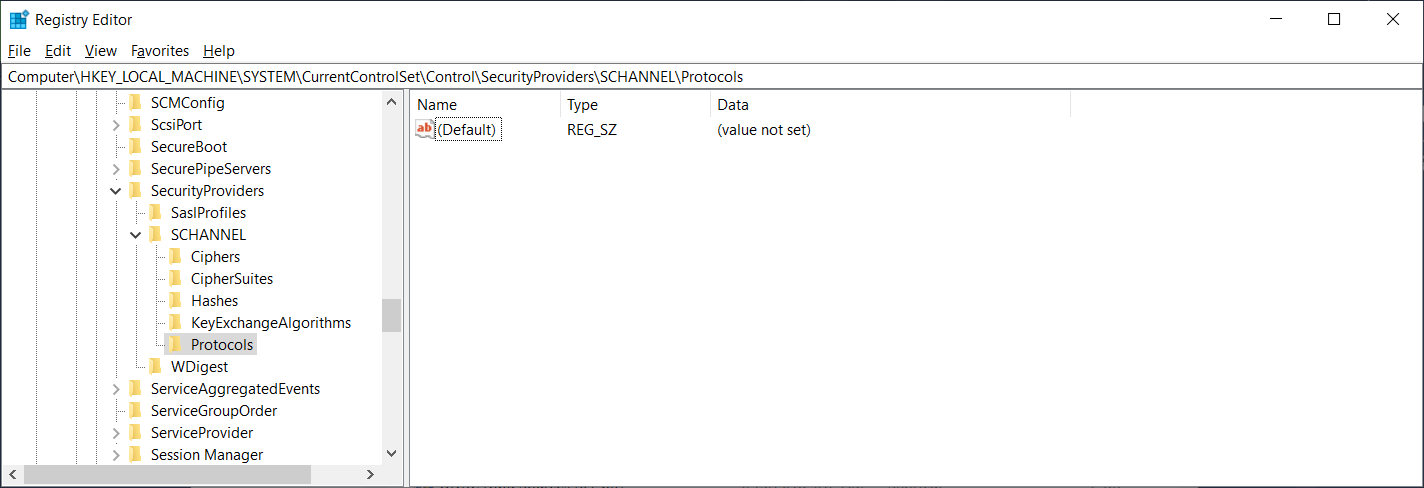
One of the possible reasons why the import of the federation metadata would fail on the ADFS server is if when TLS 1.2 is not enabled on ADFS. The server in this example was a fresh install of Windows Server 2019 and navigating to the following registry showed that TLS 1.2 was not explicitly enabled:
ComputerHKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocols
To correct this issue, simply following the steps provided in this Zoom article:
How to enable TLS 1.2 on an ADFS Server (Windows Server 2012 R2)
https://support.zoom.us/hc/en-us/articles/360033739531-How-to-enable-TLS-1-2-on-an-ADFS-Server-Windows-Server-2012-R2-
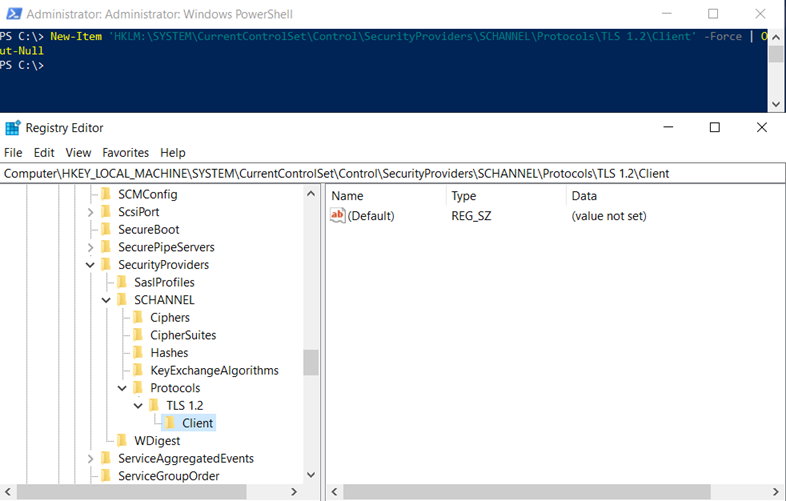
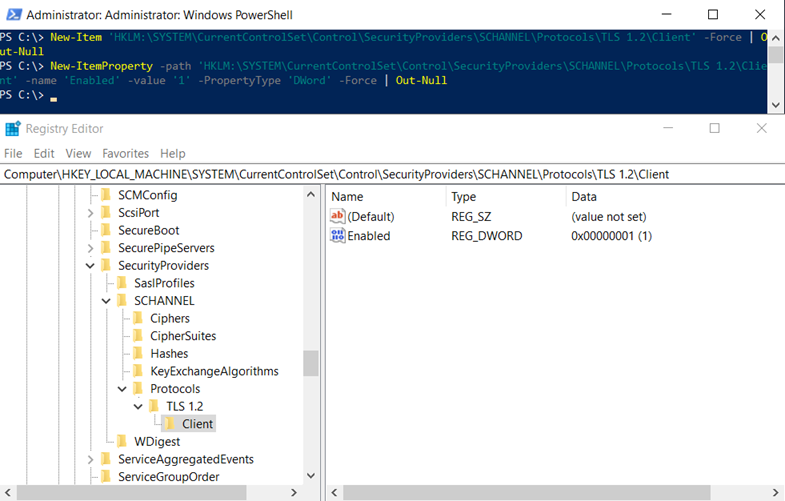
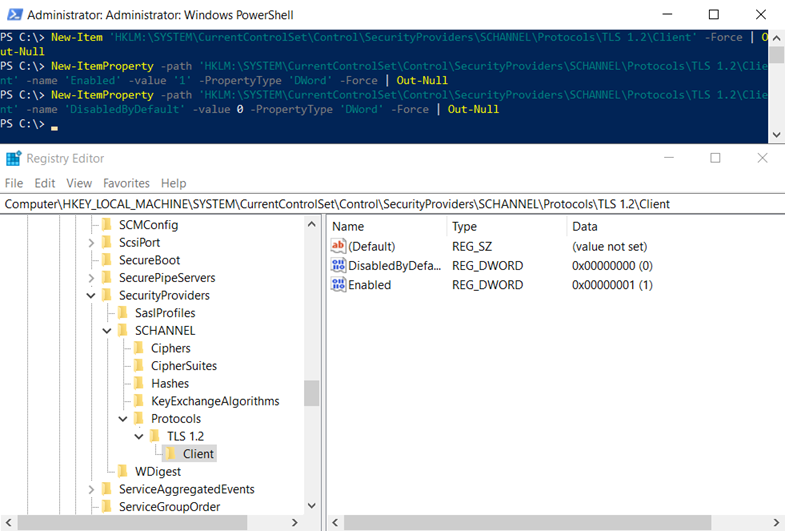
The following PowerShell cmdlets create the keys required to enable TLS 1.2:
New-Item ‘HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client’ -name ‘Enabled’ -value ‘1’ -PropertyType ‘DWord’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client’ -name ‘DisabledByDefault’ -value 0 -PropertyType ‘DWord’ -Force | Out-Null
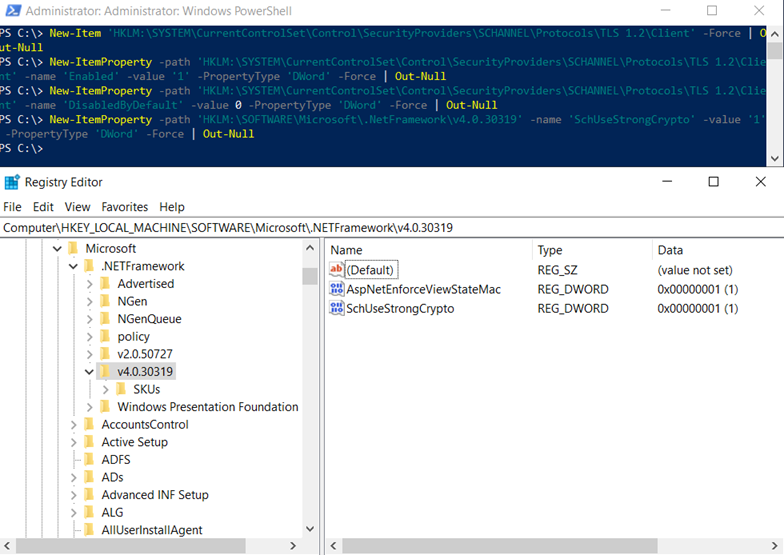
The following PowerShell cmdlet enable’s Strong Authentication for .Net Framework:
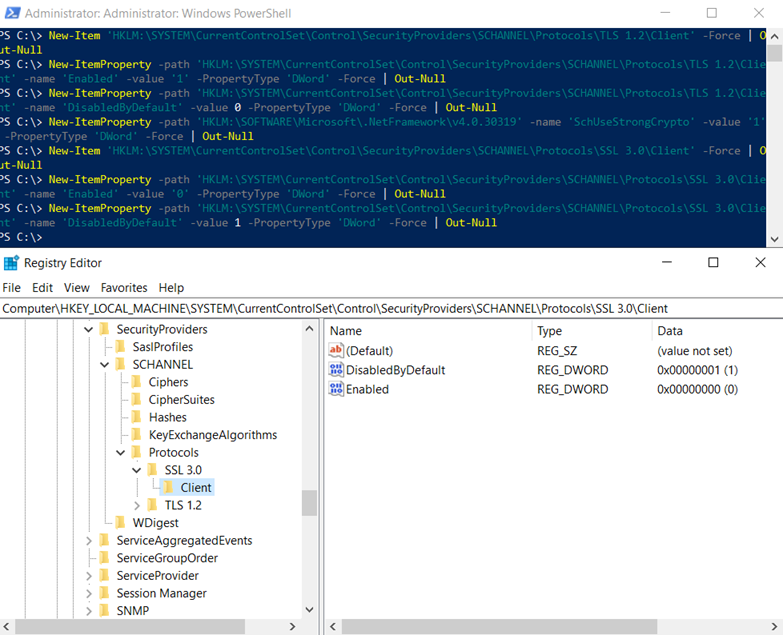
The following PowerShell cmdlets disables SSL 3.0:
New-Item ‘HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 3.0Client’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 3.0Client’ -name ‘Enabled’ -value ‘0’ -PropertyType ‘DWord’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 3.0Client’ -name ‘DisabledByDefault’ -value 1 -PropertyType ‘DWord’ -Force | Out-Null
Here is the list of cmdlets demonstrated above:
New-Item ‘HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client’ -name ‘Enabled’ -value ‘1’ -PropertyType ‘DWord’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client’ -name ‘DisabledByDefault’ -value 0 -PropertyType ‘DWord’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:SOFTWAREMicrosoft.NetFrameworkv4.0.30319’ -name ‘SchUseStrongCrypto’ -value ‘1’ -PropertyType ‘DWord’ -Force | Out-Null
New-Item ‘HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 3.0Client’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 3.0Client’ -name ‘Enabled’ -value ‘0’ -PropertyType ‘DWord’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 3.0Client’ -name ‘DisabledByDefault’ -value 1 -PropertyType ‘DWord’ -Force | Out-Null
With TLS 1.2 enabled, strong encryption enabled, and SSL 3.0 enabled, the import of the federation metadata should now succeed.