Problem
There are situations where an existing GPO is configured to restrict users from launching the MMC and the available snap-ins for non-administrative users to enhance security. To achieve this, an administrator can create a GPO with the following settings:
User Configuration > Administrative Templates > Windows Components > Microsoft Management Console > Restrict users to the explicitly permitted list of snap-ins: Enabled
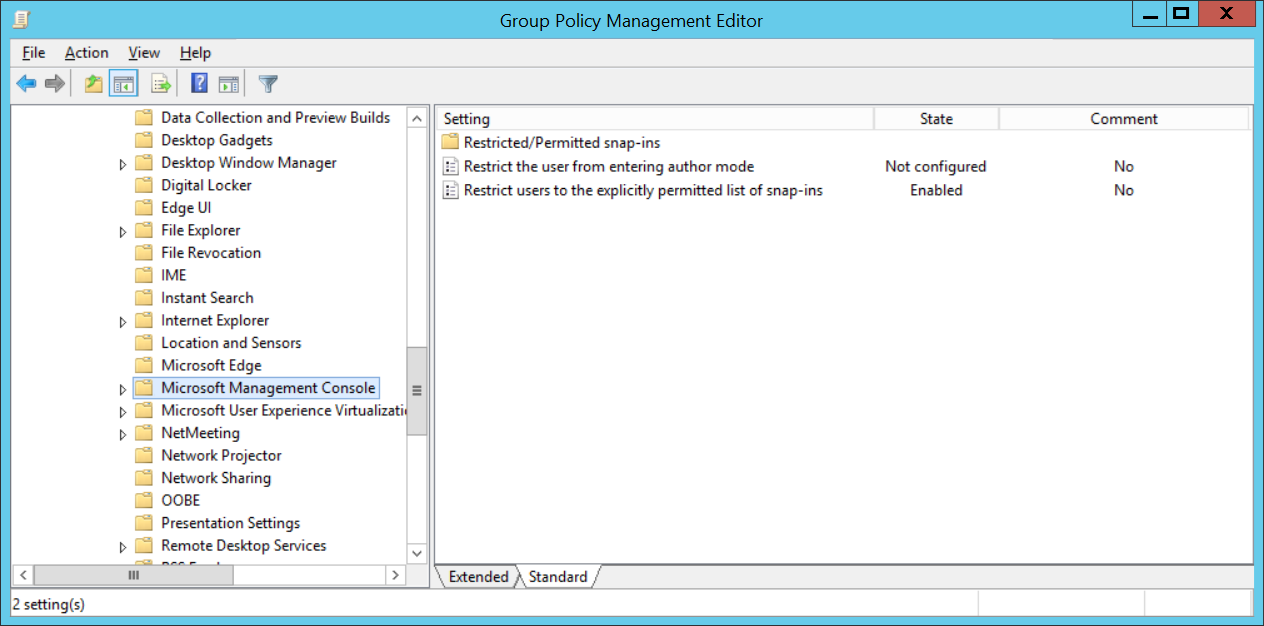
Re-enabling select MMCs are fairly straight forward as a list of consoles are provided in the sub folder: Restricted/Permitted snap-ins
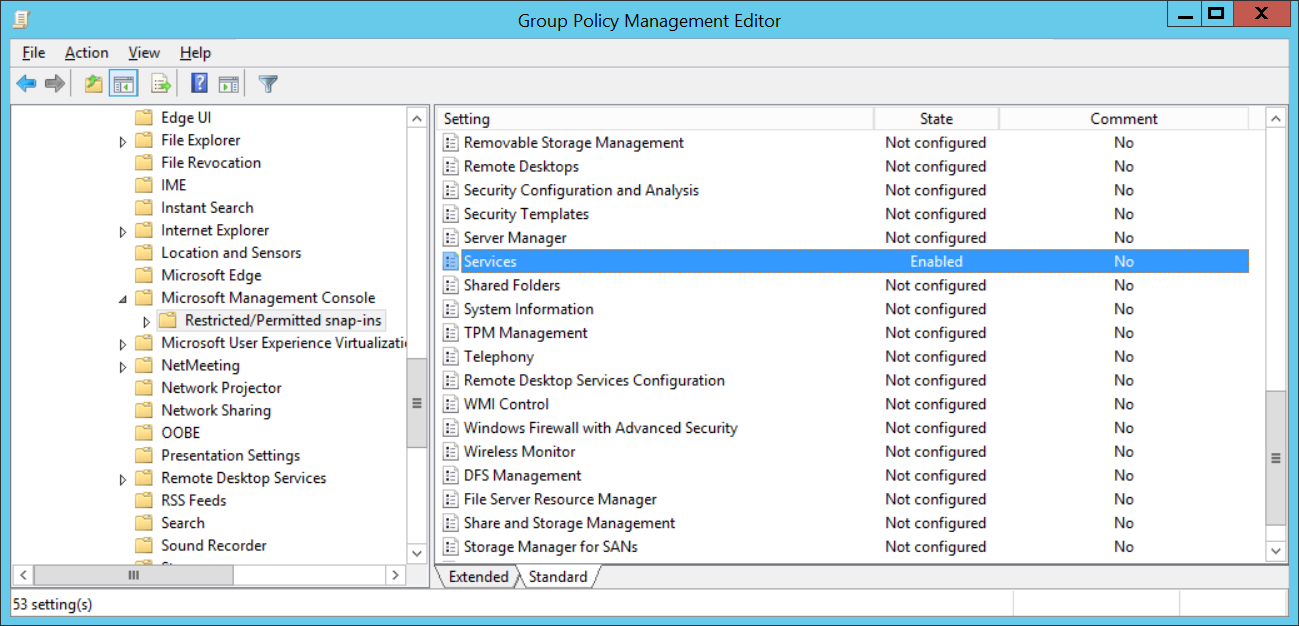
As the list provided in the default Group Policy ADM only includes default Windows Server snap-ins, attempting to add a MMC such as the following SQL Server 2919 Configuration Manager would become a problem:
Solution
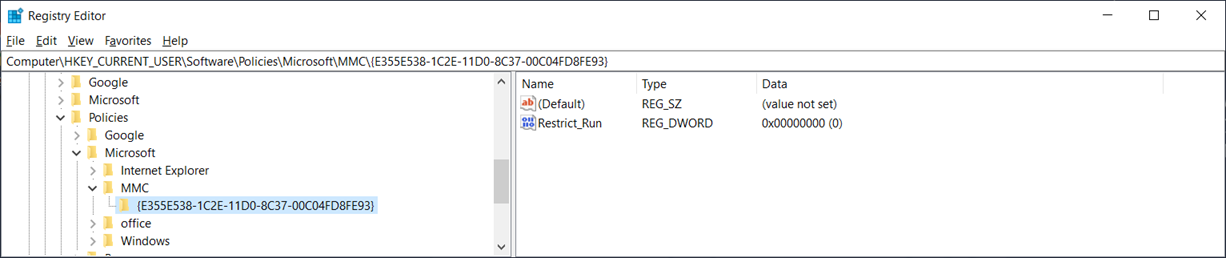
There are two methods to address this issue. The first is to create a custom ADMX file and import it into Active Directory and the second is to apply the registry key that a custom ADMX would. This document serves to demonstrate the latter method as it is simpler for one-off configurations. To achieve this, we will need to create a GPO that will create a [HKCU]SoftwarePoliciesMicrosoftMMC{MMC snap-in GUID} and set the Restrict_Run key to 0, which represents enable (1 is disabled):
Identify the custom MMC snap-in GUID
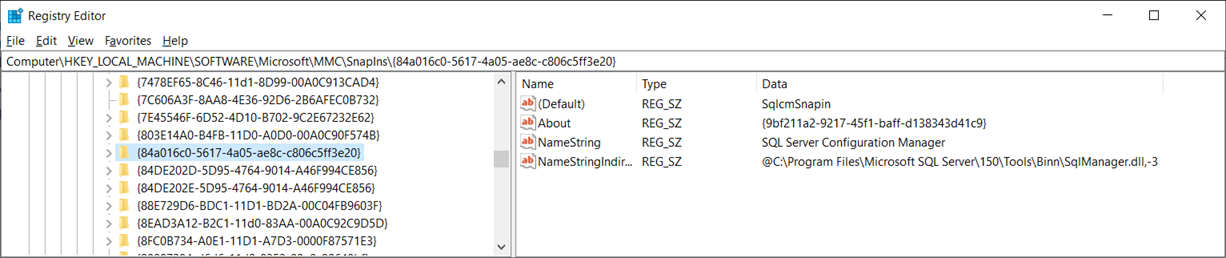
The first step is to identify the custom mmc snap-in GUID. For the purpose of this example, we will use the snap-in SQL Server 2919 Configuration Manager. Begin by navigating to:
ComputerHKEY_LOCAL_MACHINESOFTWAREMicrosoftMMCSnapIns
Then locating and copying the custom snap-in’s GUID, which is the folder’s name:
{84a016c0-5617-4a05-ae8c-c806c5ff3e20}
Create a GPO with an update registry configuration
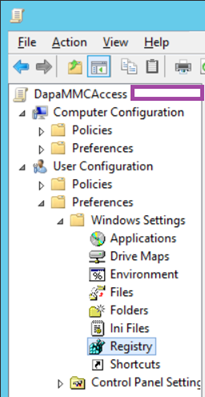
With the mmc snap-in GUID identified, proceed to create a GPO, navigate to User Configuration > Preferences > Windows Settings > Registry:
Create a registry configuration as such:
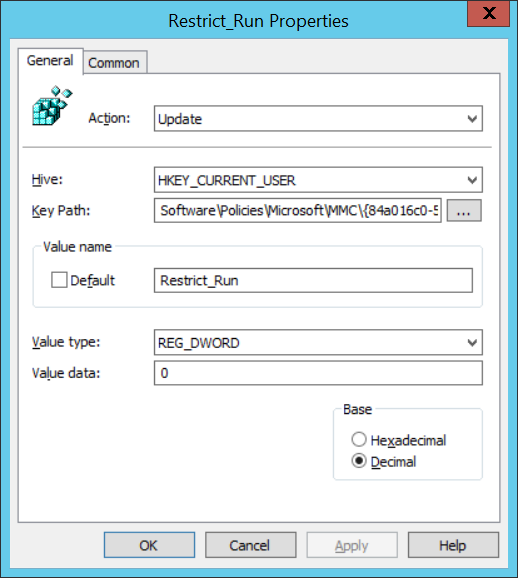
Action: Update
Hive: HKEY_CURRENT_USER
Key Path: SoftwarePoliciesMicrosoftMMC{84a016c0-5617-4a05-ae8c-c806c5ff3e20
Value name: Restrict_Run
Value type: REG_DWORD
Value data: 0
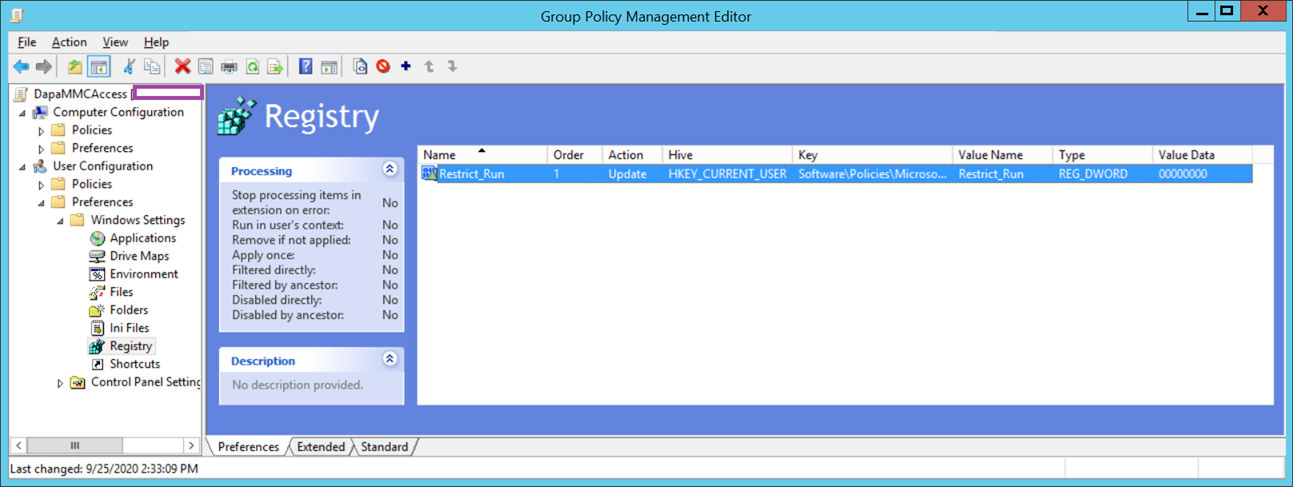
The policy should look as such once configured:
With the above policy created, have the user with this policy applied log off and back on to access the custom mmc snap-in.



4 Responses
Hi Terence,
Citrix Studio's GUID appears as FX:{147C3FB4-2709-47cd-8745-7D4962341189}. So the key to be created under HKCU will be just 147C3FB4-2709-47cd-8745-7D4962341189 or something else?
I tested it without FX: but it did not work. Then tested with FX:{147C3FB4-2709-47cd-8745-7D4962341189}, it partially worked.
First I got an error message and after I clicked OK, Studio opened up. The error message is "The snap-in below, referenced in this document, has been restricted by policy. Contact your administrator for details. Folder." The error message doesn't seem to be normal because I am explicitly allowing Studio even if "Restrict the user from entering author mode" and "Restrict users to the explicitly permitted list of snap-ins" are enabled.
Please help.
Sorry for the spam. I figured it out. For Citrix Studio, one more GUID corresponding to Folder snap-in needs to be created. That is {C96401CC-0E17-11D3-885B-00C04F72C717}.
So two Keys under HKCUSoftwarePoliciesMicrosoftMMC
1. Citrix Studio snap-in
2. Folder Snap-in
Both keys will have "Restrict_Run"= dword:00000000
Wow! Cool, thank you very much man!
Just working on a bunch of computers, which will be accessed by external app installers, I tired to restrict everything and this is a good catch!
Cheers, Jim