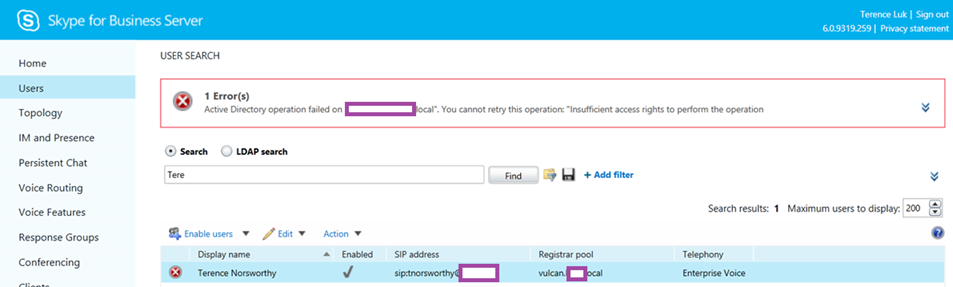
One of the most common questions I still get asked when it comes to Skype For Business is when an administrator attempts to edit an account but receives the following error:
Active Directory operation failed on “dc1.contoso.local”. You cannot retry this operation: “Insufficient access rights to perform the operation
This error has been around since Lync Server 2010 and the two ways around it are:
- Use PowerShell to edit the account
- Enable Inheritance for the Active Directory account
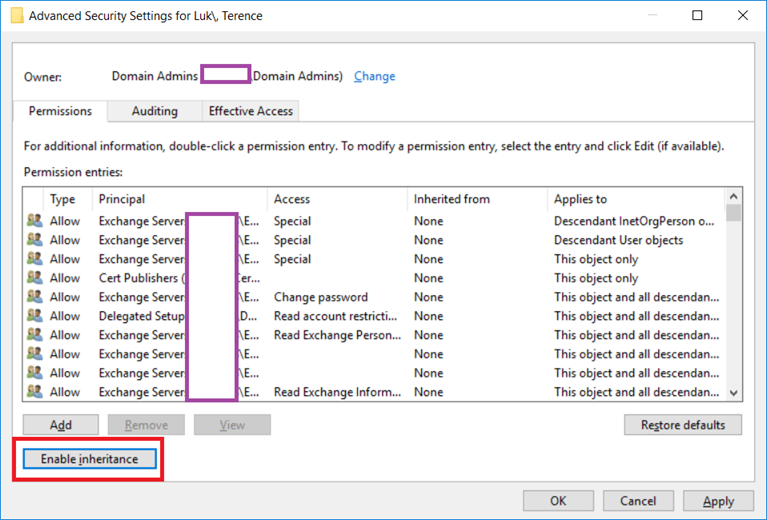
Most administrators would prefer to opt for #2 as this would allow the account to be configured in the GUI so what needs to be done is to go into the Security properties of the account, click on Advanced button, then click on Enable inheritance so that the account inherits permissions:
This isn’t too much effort for one or two accounts but not very practical in the 10s, 100s or 1000s. The following are PowerShell scripts that allows to better identify and configure these accounts:
List Accounts and their Inheritance Status and Enable Accounts that have Inheritance disabled
$ou = ‘ou=User Acccounts,ou=Contoso Organization,dc=contoso,dc=local’
$userslist = Get-ADUser -ldapfilter “(objectclass=user)” -searchbase $ou
foreach($account in $userslist)
{
# Bind the accounts
$ou = [ADSI](“LDAP://” + $account)
$sec = $ou.psbase.objectSecurity
if ($sec.get_AreAccessRulesProtected())
{
$isProtected = $false ## turn on inheritance
$preserveInheritance = $true ## retain inherited permissions
$sec.SetAccessRuleProtection($isProtected, $preserveInheritance)
$ou.psbase.commitchanges()
Write-Host “$account is now enabled for inheritance”;
}
else
{
Write-Host “$account already has inheritance enabled”
}
}
Export Accounts and Inheritance Status to CSV
$CSVexportPath = ‘C:tempAccountInheritanceStatus.csv’
$ou = ‘ou=User Acccounts,ou=Contoso Organization,dc=contoso,dc=local’
$userslist = Get-ADUser -ldapfilter “(objectclass=user)” -searchbase $ou
foreach($account in $userslist)
{
# Bind the accounts
$ou = [ADSI](“LDAP://” + $account)
$sec = $ou.psbase.objectSecurity
$UPN = $account.UserPrincipalName
$name = $account.name
$DistinguishedName = $account.DistinguishedName
#Store the information from this run into the array
[PSCustomObject]@{
UPN = $account.UserPrincipalName
Name = $account.name
DistinguishedName = $account.DistinguishedName
InheritanceEnabled = $sec.get_AreAccessRulesProtected()
} | Export-Csv $CSVexportPath -notype -Append
}
List Inheritance Status to Table
$ou = ‘ou=User Acccounts,ou=Contoso Organization,dc=contoso,dc=local’
$userslist = Get-ADUser -ldapfilter “(objectclass=user)” -searchbase $ou
foreach($account in $userslist)
{
# Bind the accounts
$ou = [ADSI](“LDAP://” + $account)
$sec = $ou.psbase.objectSecurity
$UPN = $account.UserPrincipalName
$name = $account.name
$DistinguishedName = $account.DistinguishedName
#Store the information from this run into the array
[PSCustomObject]@{
UPN = $account.UserPrincipalName
Name = $account.name
DistinguishedName = $account.DistinguishedName
InheritanceEnabled = $sec.get_AreAccessRulesProtected()
} | Format-Table -AutoSize
}



2 Responses
This comment has been removed by a blog administrator.
Hi Terence, I get this error when I run List Accounts and their Inheritance Status and Enable Accounts that have Inheritance disabled:
Exception when calling "CommitChanges" with "0" argument (s): "Violation of variations.
"
In D: Script Powershell Enable Inheritance AD USers EnableInheritance.ps1: 25 car: 1
+ $ ou.psbase.commitchanges ()
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~
+ Category information: unspecified: (:) [], MethodInvocationException
+ FullyQualifiedErrorId: DotNetMethodException
can you help me?