I recently had an ex-colleague reach out to me about configuring the integration between Citrix ShareFile and Azure Active Directory (Azure AD) as he was required to configure SAML authentication for a Citrix ShareFile portal so that it would use Azure AD as an IDP. The official documentation can be found here:
How to Configure Single Sign-On (SSO) for ShareFile
https://support.citrix.com/article/CTX208557
Tutorial: Azure Active Directory integration with Citrix ShareFile
https://docs.microsoft.com/en-us/azure/active-directory/saas-apps/sharefile-tutorial
However, the documentation wasn’t extremely clear on some of the steps and other blog posts available references the older Azure portal so I thought writing this post may help anyone who may be looking for updated information.
Step #1 – Adding Citrix ShareFile as an Enterprise Application
Begin by logging into portal.azure.com for the tenant that will be providing the Azure AD as the iDP, navigate to Azure Active Directory > Enterprise Applications:
Click on New application:
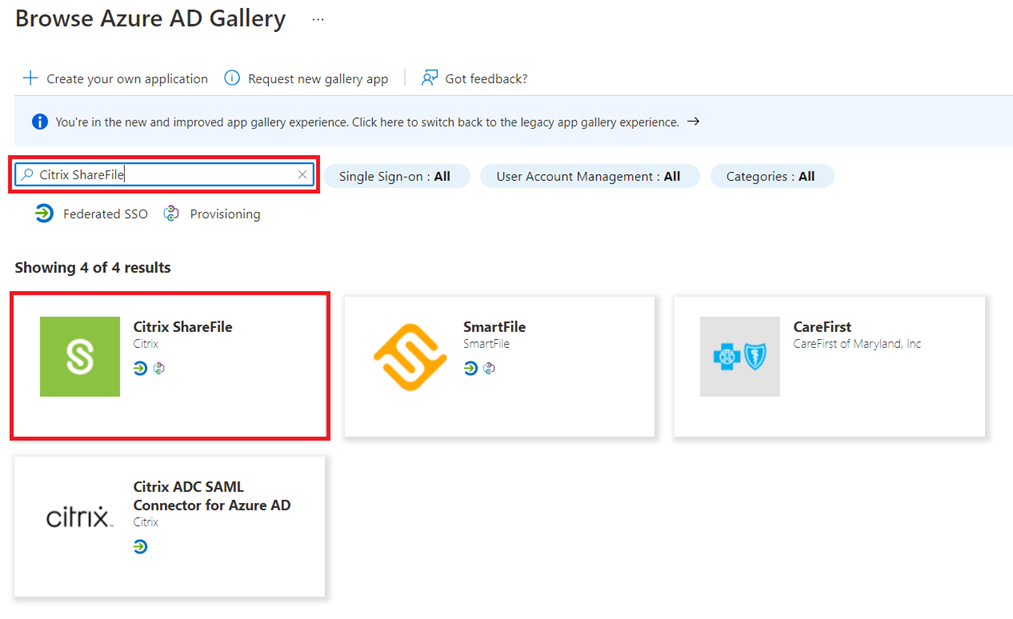
Search for Citrix ShareFile and then click on the tile:
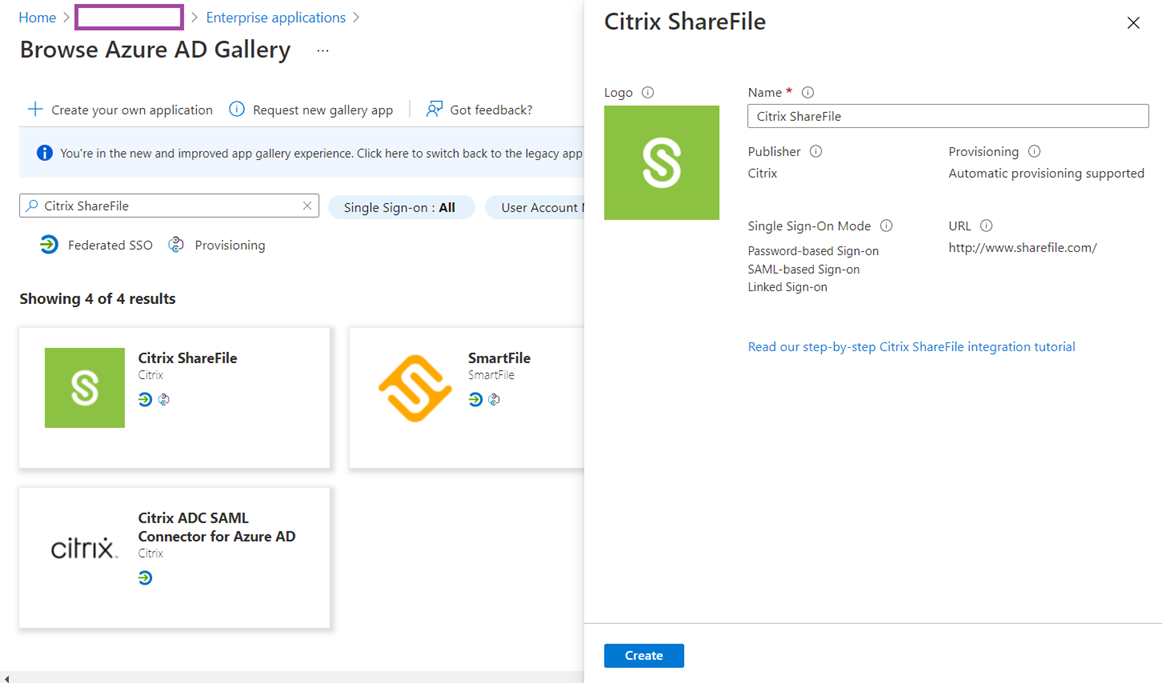
A window will slide out from the right to display the application, proceed to click on the Create button:
The creation of the application will take a few minutes and eventually finish:
Step #2 – Configure Azure ShareFile Enterprise Application
Proceed to navigate into the Single sign-on configuration in the ShareFile Enterprise Application:
Click on the SAML tile:
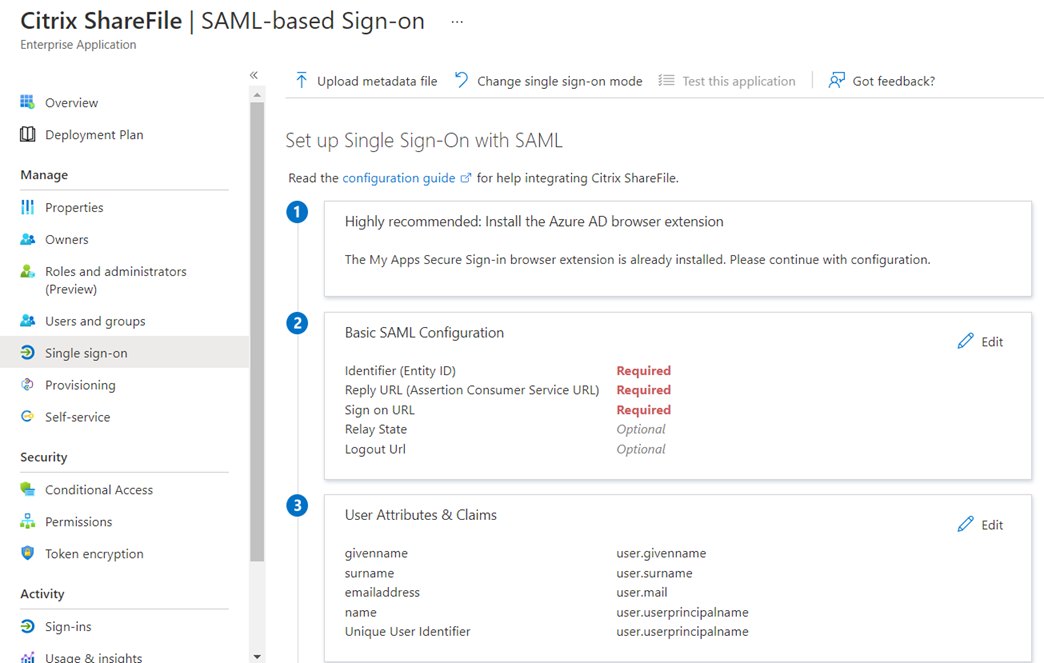
The SAML configuration will be displayed:
Click on the Edit button for the Basic SAML Configuration:
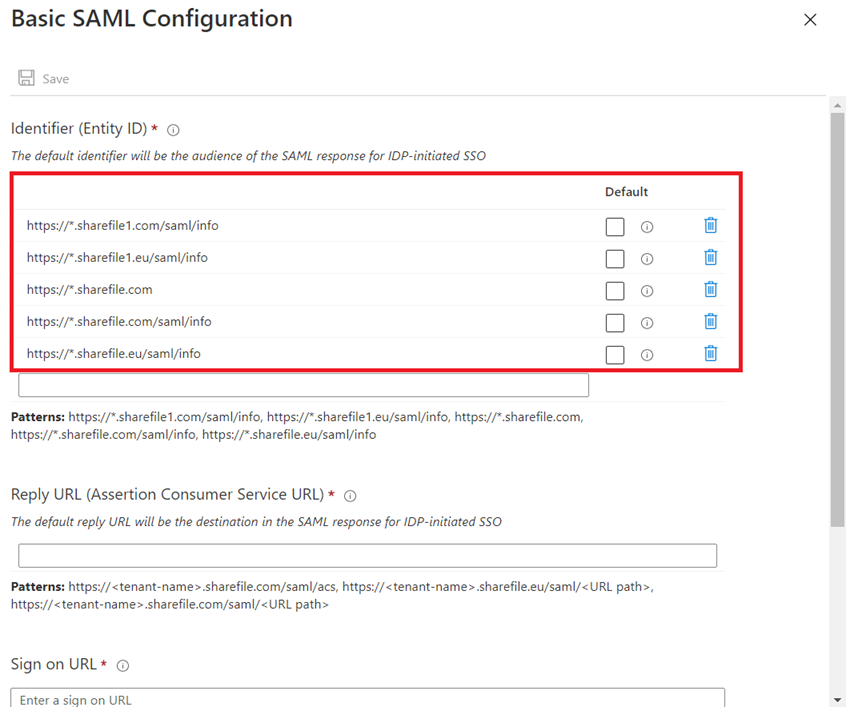
Remove the default Identifier (Entity ID) configuration:
Enter the following for the configuration and then save it:
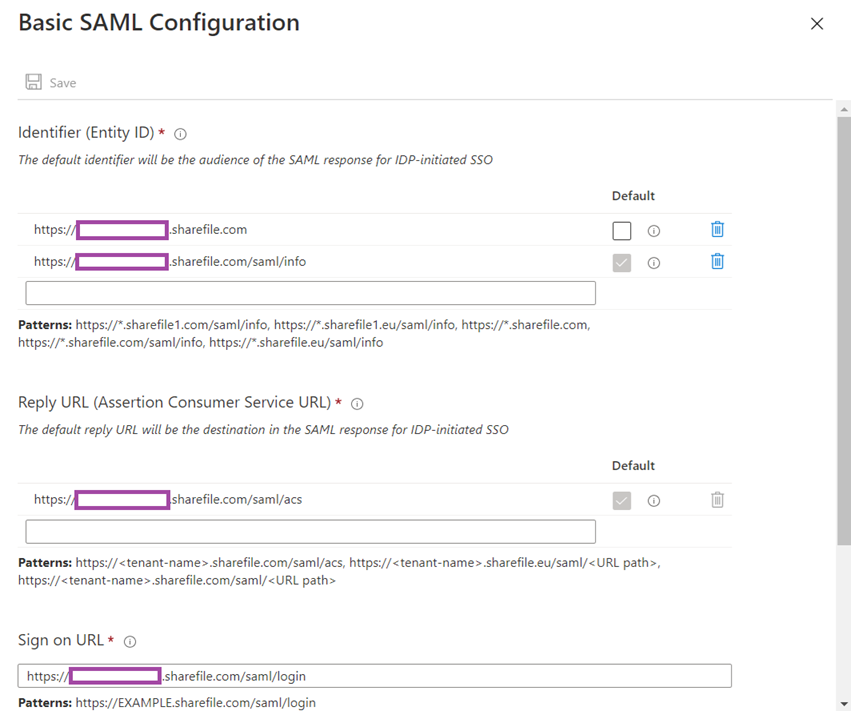
Identity (Entity ID):
https://<customDomain>.sharefile.com/saml/info < set this as default
https://<customDomain>.sharefile.com
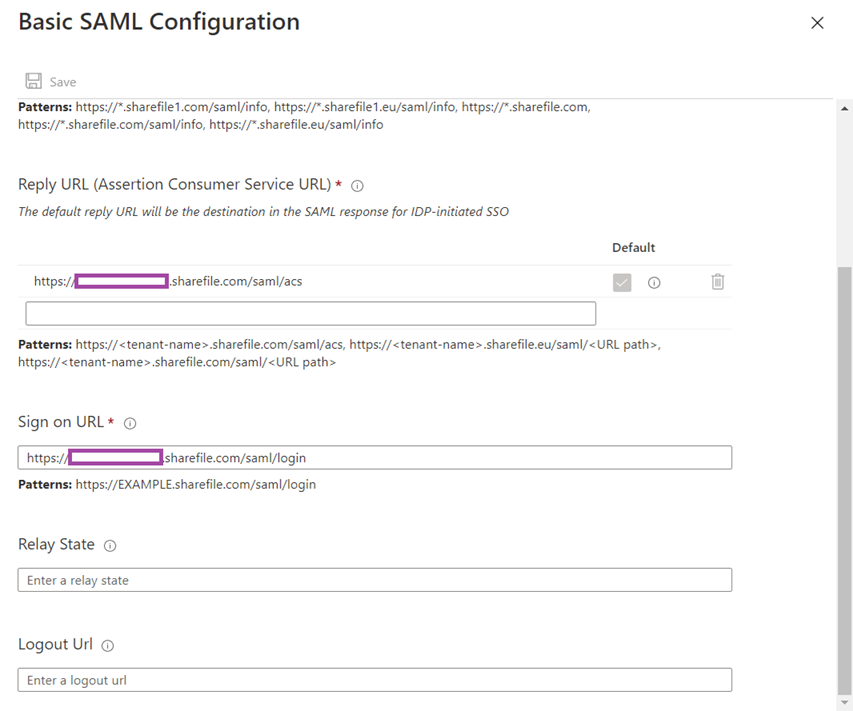
Reply URL (Assertion Consumer Service URL):
https://<customDomain>.sharefile.com/saml/acs
Sign on URL:
https://<customDomain>.sharefile.com/saml/login
Relay State:
Leave blank.
Logout Url:
Leave blank.
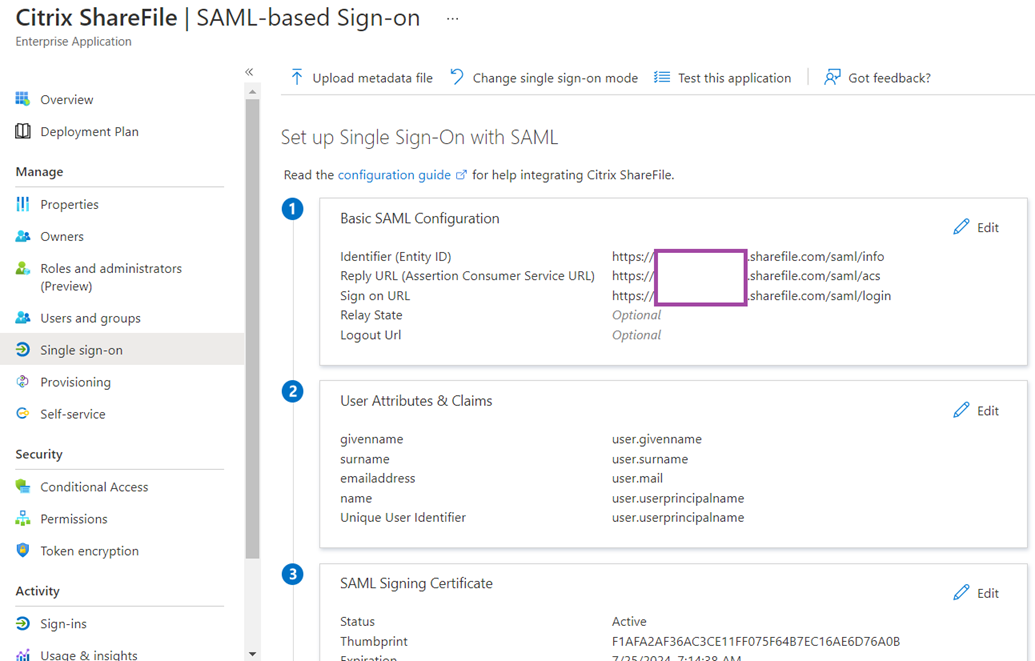
Saving the settings will now display the new configuration:
You will be prompted to test the single sign-on settings upon successfully configuring the SAML configuration but given that we have not configured ShareFile yet, select No, I’ll test later:
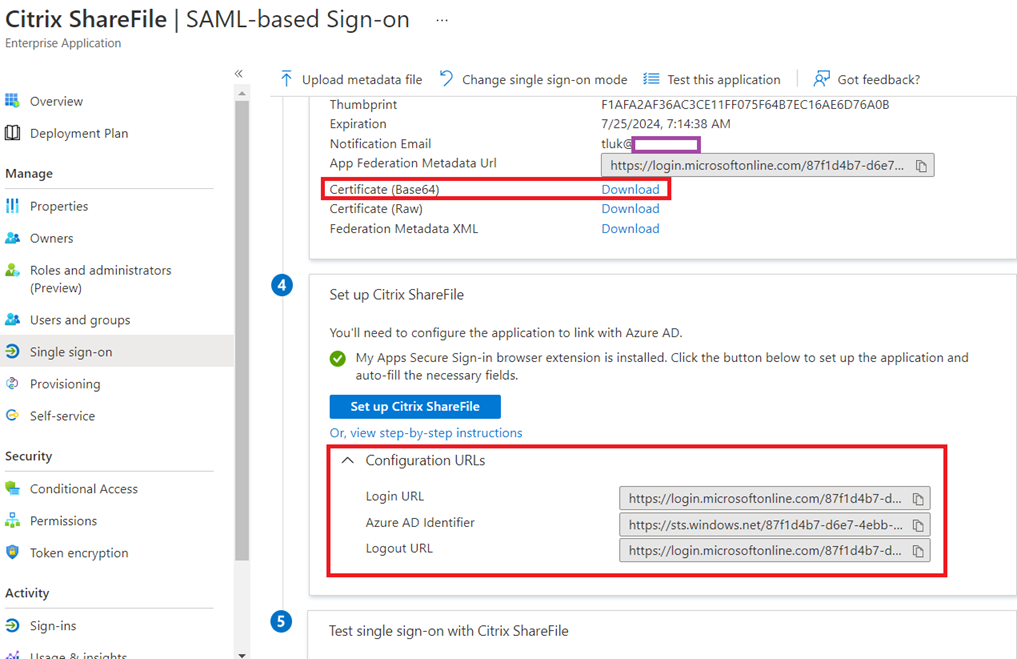
Scroll down and locate the certificate download link labeled as:
Certificate (Base64) Download
Download the certificate and then proceed to expand the Configuration URLs and copy the value for the following to somewhere like NotePad:
- Login URL
- Azure AD Identifier
- Logout URL
*Note that the Login URL and Logout URL values are the same and the following is a sample:
https://login.microsoftonline.com/97f1d4b7-d6e7-4ebb-842d-cce6024b0bb3/saml2
https://sts.windows.net/87f1d4b7-d6e7-4ebb-842d-cce6024b0bb2/
https://login.microsoftonline.com/97f1d4b7-d6e7-4ebb-842d-cce6024b0bb3/saml2
Step #3 – Grant Azure AD user access to ShareFile
The next step is to configure grant permissions to users and groups who will be logging into ShareFile with their Azure AD credentials. Failure to do so will throw an error indicating the user logging on is not assigned to a role for the application.
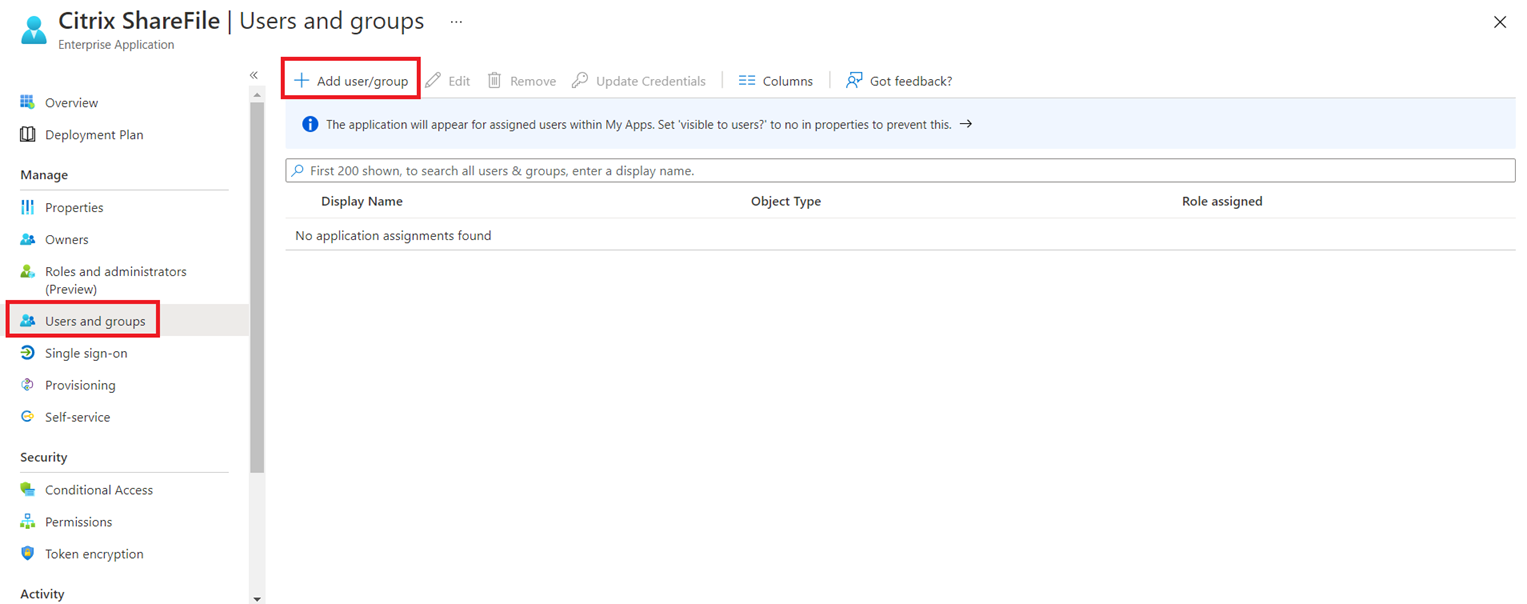
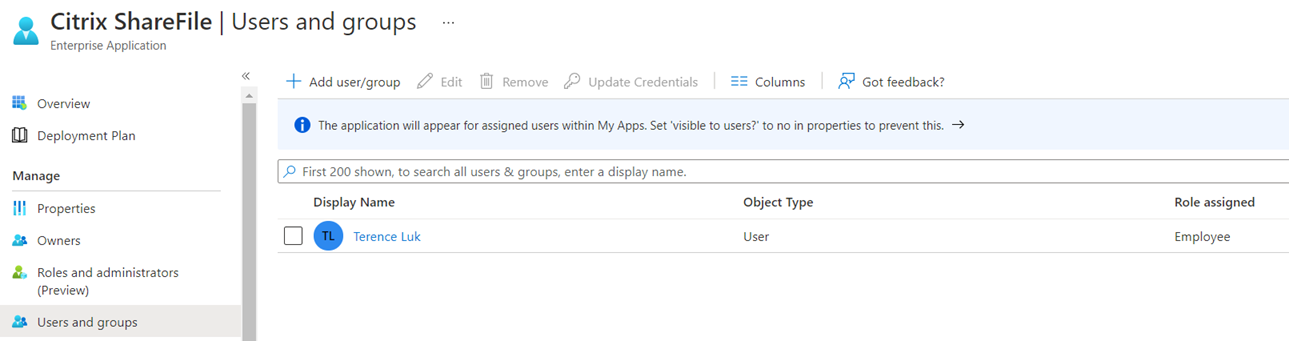
From within the Citrix ShareFile Enterprise Application, navigate to Users and groups then click on the Add user/group button:
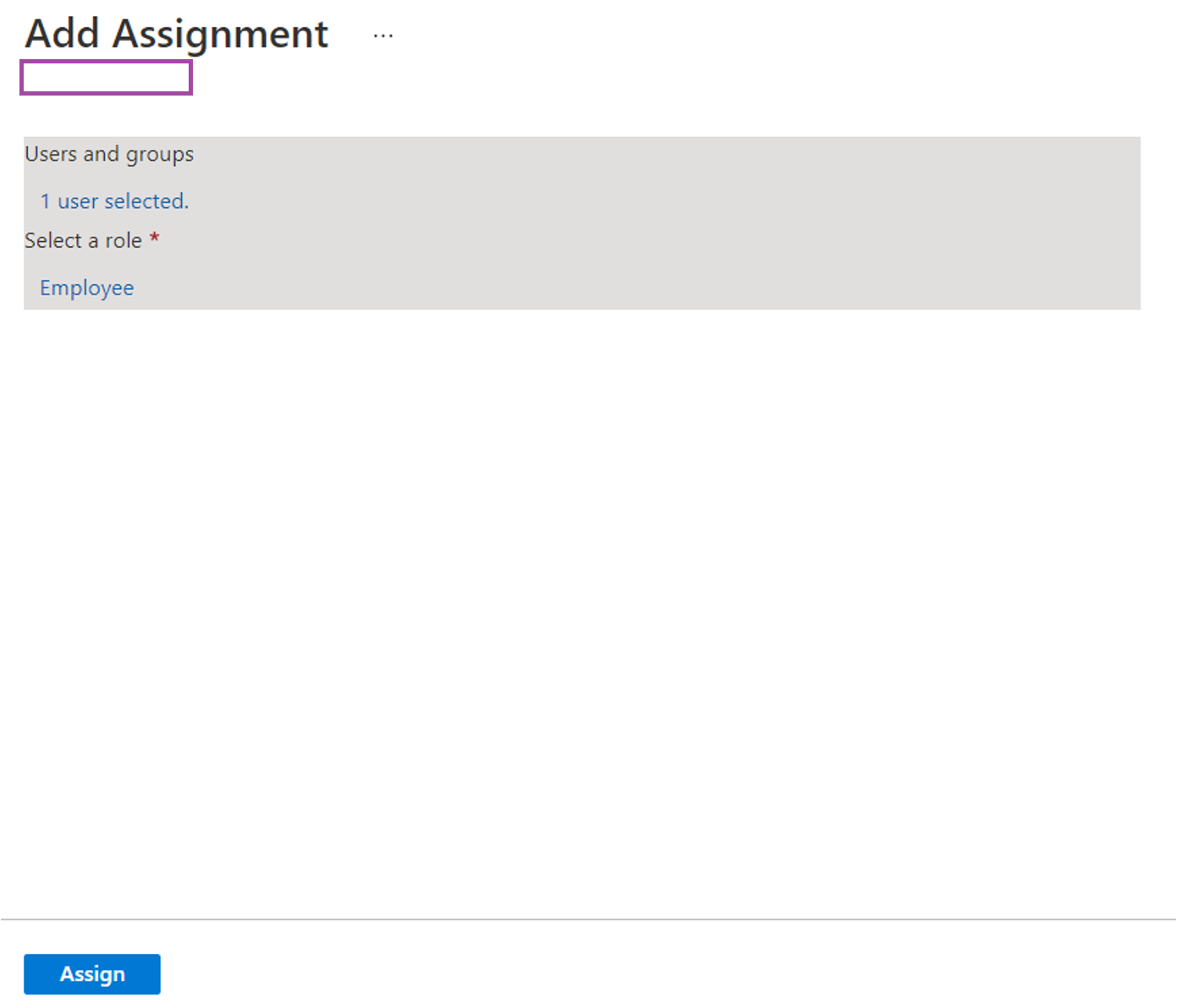
Use the User and groups link to select either a test user or a group that will log into ShareFile with their Azure AD credentials (I will use my user account for this example) and then use the Select a role link to configure a role. The Microsoft documentation indicates we can have none selected as Default Access will automatically be configured but I’ve found that the assign button does not become active until a role is selected. Other documentation I was able to find indicates the Employee role should be configured so proceed with using Employee as the role:
Proceed by clicking the Assign button:
Notice that my account is now assigned:
Step #4 – Configure ShareFile to for Single sign-on / SAML 2.0 Configuration
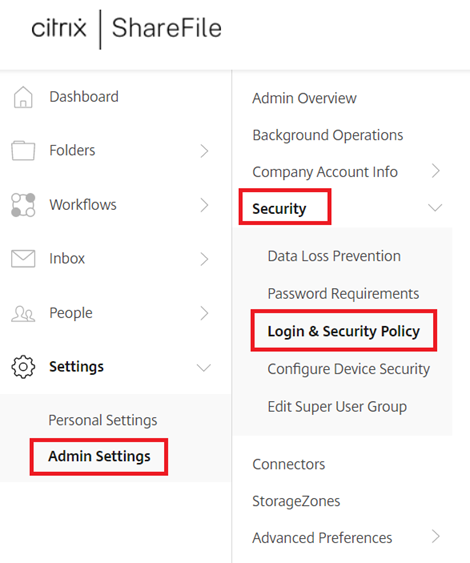
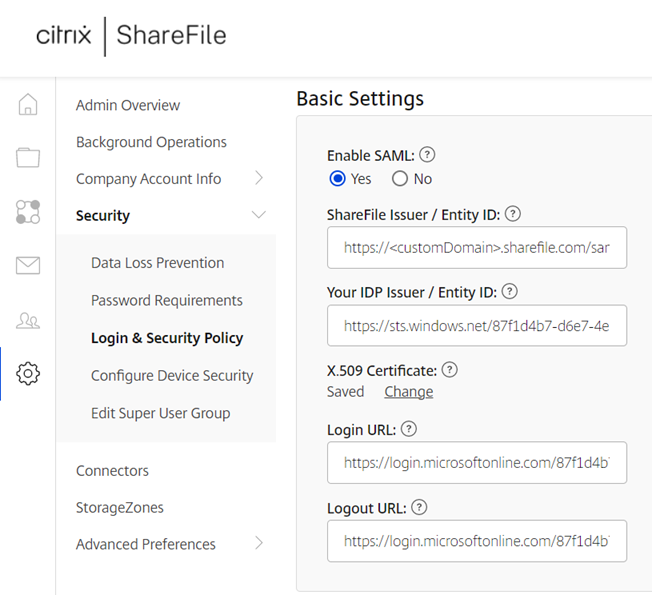
With Azure AD configured, proceed to log into the ShareFile portal as an administrator, then navigate to Settings > Admin Settings > Security > Login & Security Policy:
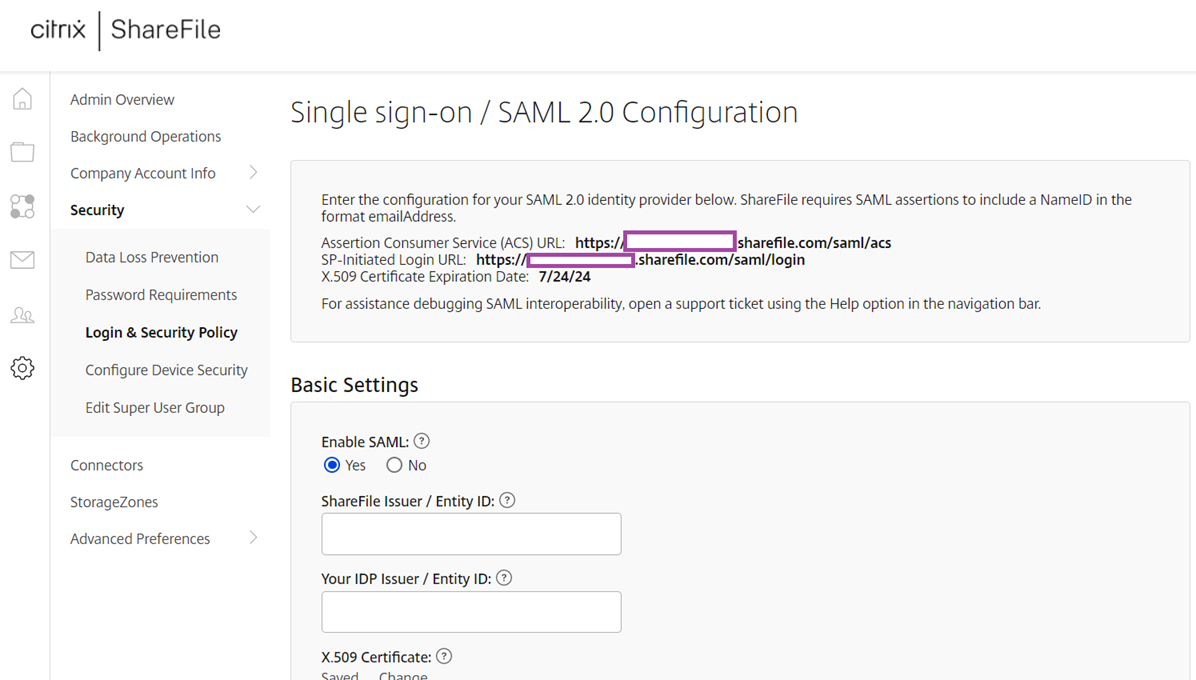
Scroll down to the Single sign-on / SAML 2.0 Configuration section and select Yes for Enable SAML:
Proceed by opening the Notepad with the Configuration URLs that were copy from Azure:
- Login URL
- Azure AD Identifier
- Logout URL
As well as opening the downloaded Citrix ShareFile.cer Certificate (Base64):
Fill in the following fields:
Field: ShareFile Issuer / Entity ID
Value: https://<customDomain>.sharefile.com/saml/info
Field: Your IDP Issuer / Entity ID
Value: Azure AD Identifier (example: https://sts.windows.net/87f1d4b7-d6e7-4ebb-942d-cce6024b0bb2/)
Field: X.509 Certificate
Value: Paste the certificate content from the downloaded Citrix ShareFile.cer Certificate into the configuration.
Field: Login URL
Value: Login URL from Azure (example: https://login.microsoftonline.com/87f1d4b5-d6e7-4ebb-842d-cce6024b0bb2/saml2)
Field: Logout URL:
Value: Logout URL from Azure (example: https://login.microsoftonline.com/87f1d4b5-d6e7-4ebb-842d-cce6024b0bb2/saml2)
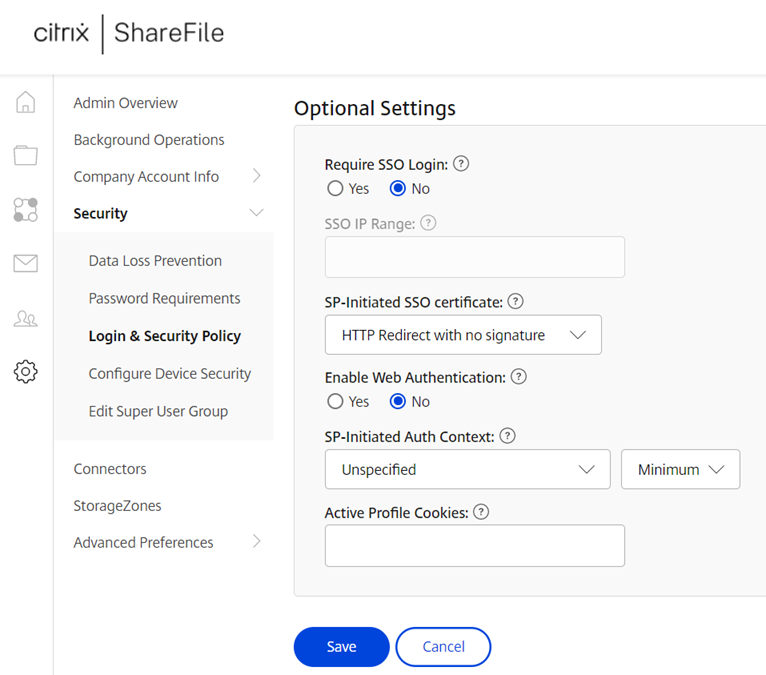
Scroll down to the Optional Settings section:
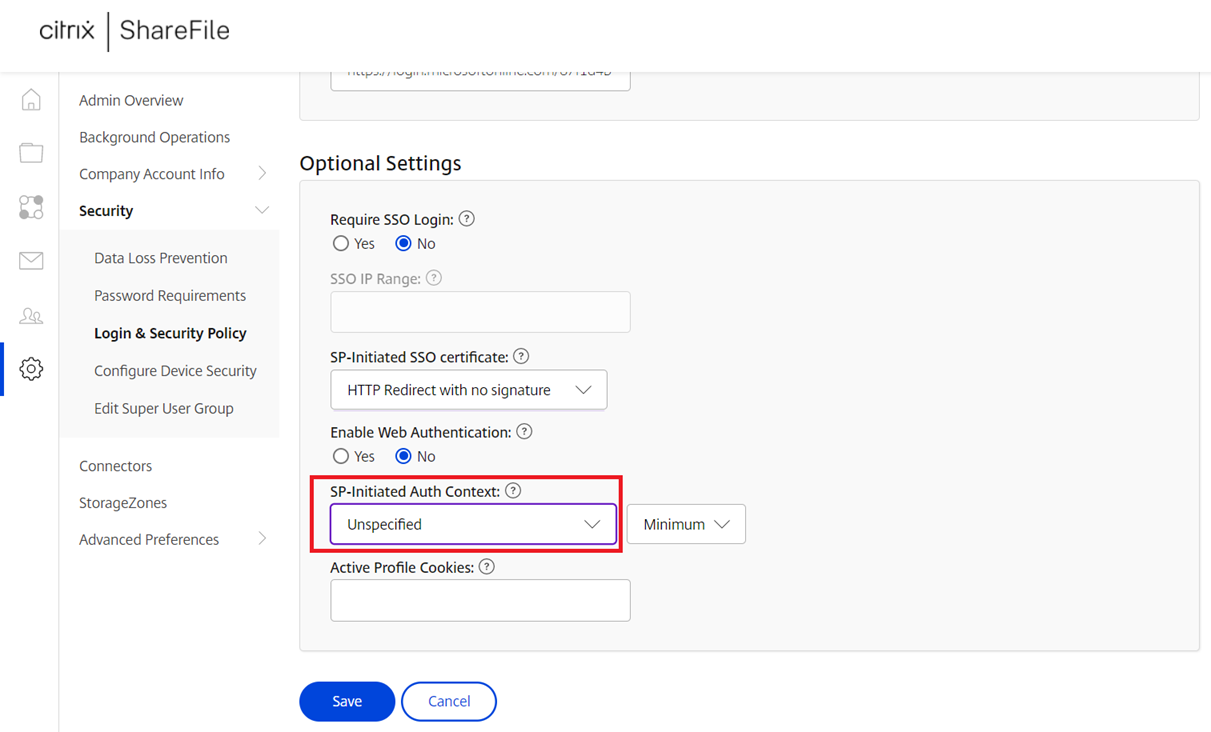
Locate the SP-Initiated Auth Context configuration:
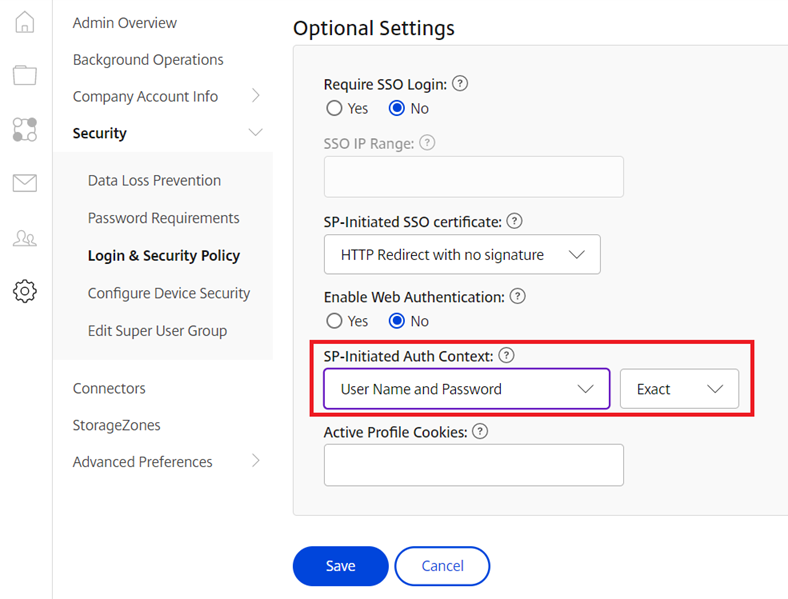
Change the configuration to User Name and Password, Exact for the field to the right, and save the settings:
Step #5 – Set up user as Employee in ShareFile
The next step is to set up the corresponding test user or ShareFile users in ShareFile. This environment uses on-premise Active Directory accounts, which are synced into Azure AD and the method I used to configure the accounts in ShareFile is the ShareFile User Management Tool (https://support.citrix.com/article/CTX214038). I will not be demonstrating the process in this post.
Step #6 – Test SSO with SAML
The final step is to test SSO to ensure that the configuration is correct. We can begin by using the Test this application button in the Citrix ShareFile Enterprise Application in Azure portal:
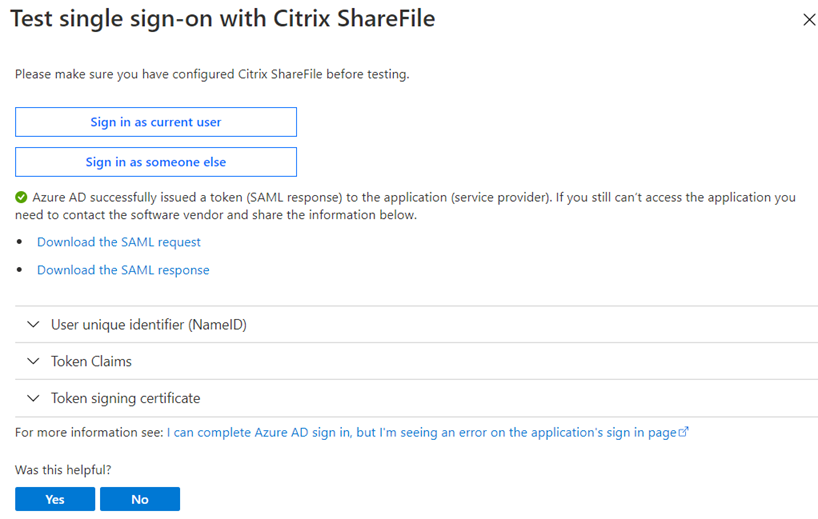
A successful test will display the following:
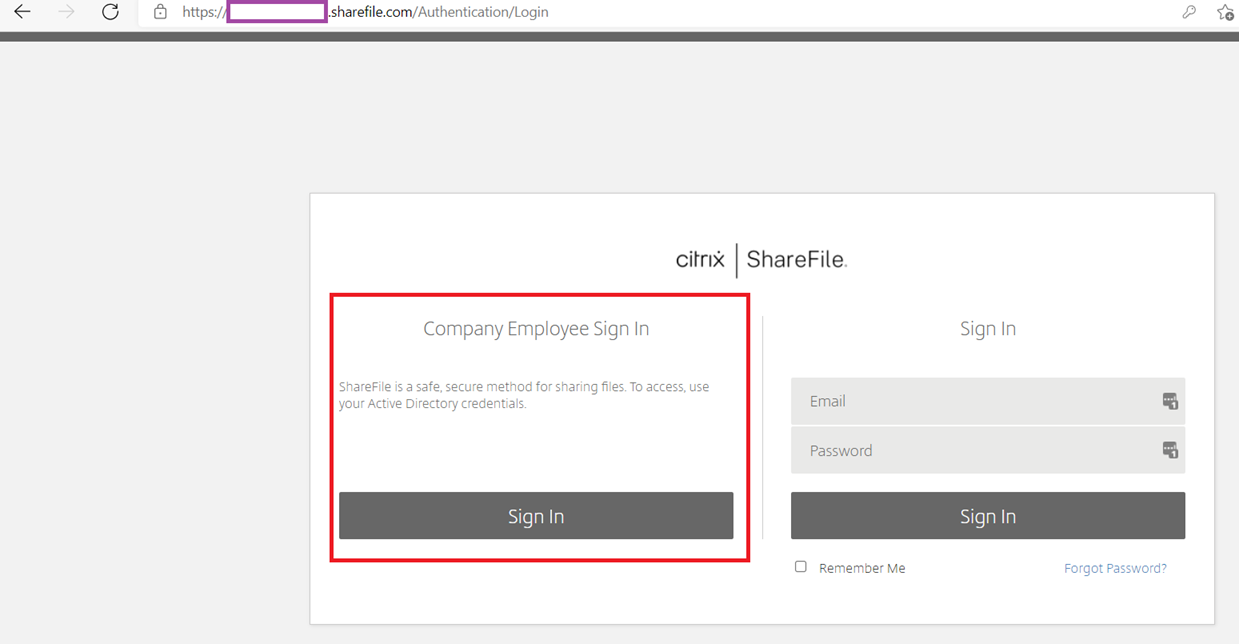
Next, navigate to the Sharefile login portal and you will notice the additional Company Employee Sign In option for logging in:
Proceed to login and confirm that the process is successful.