Duo has been one of the most common MFA solutions I’ve worked with over the past 5 years and most clients who have this as their MFA solution for on-premise services such as ADFS, tend to ask whether they can also use it for Azure AD. The short answer is yes but there the requirement of having Conditional Access (available with Azure AD Premium P1) within Azure means an additional cost would be required to replace Azure MFA with the solution (https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/concept-fundamentals-mfa-get-started). Another consideration is that certain risk detection features of Azure Identity Protection (https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/concept-identity-protection-risks) will not be available. With that said, the purpose of this post is to provide a quick walkthrough of the setup process for using Duo as the MFA for Azure AD portal.azure.com and Office 365 authentication. The official Duo documentation can be found here: https://duo.com/docs/azure-ca
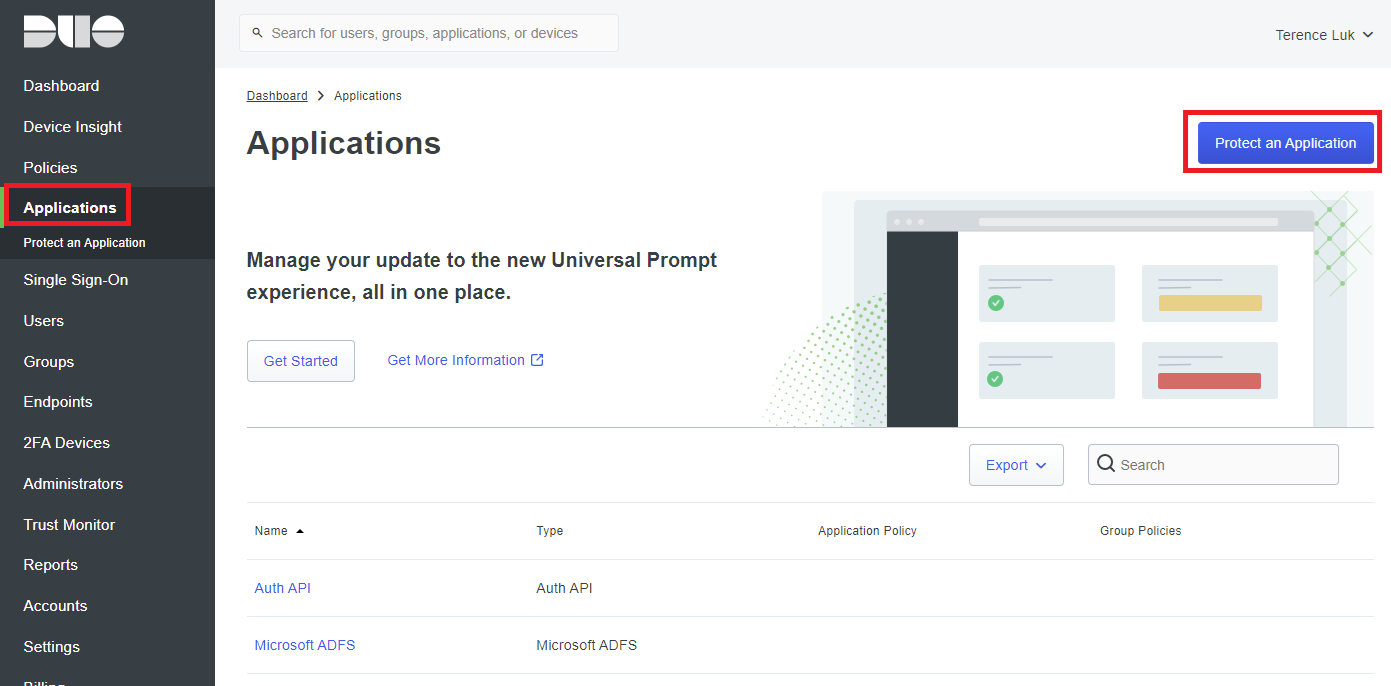
Begin by logging into the Duo administration portal: https://admin.duosecurity.com/, navigate to Applications and click on Protect and Application to register Azure as an application:
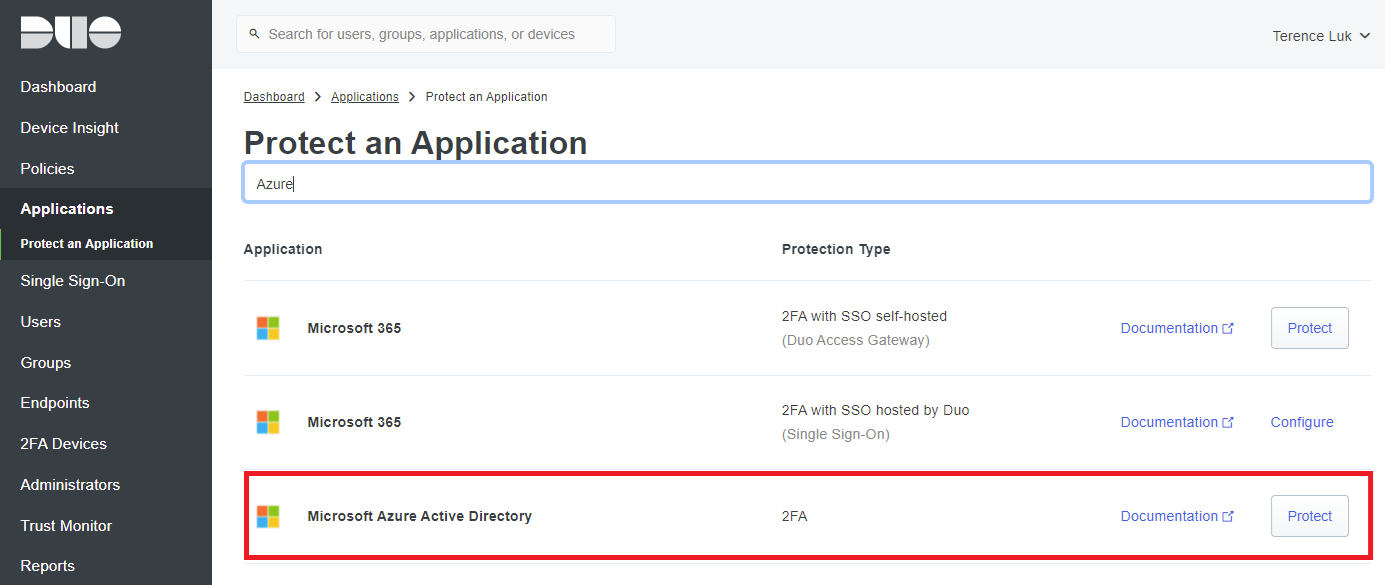
Search for Azure, select Microsoft Azure Active Directory and click on the Protect button:
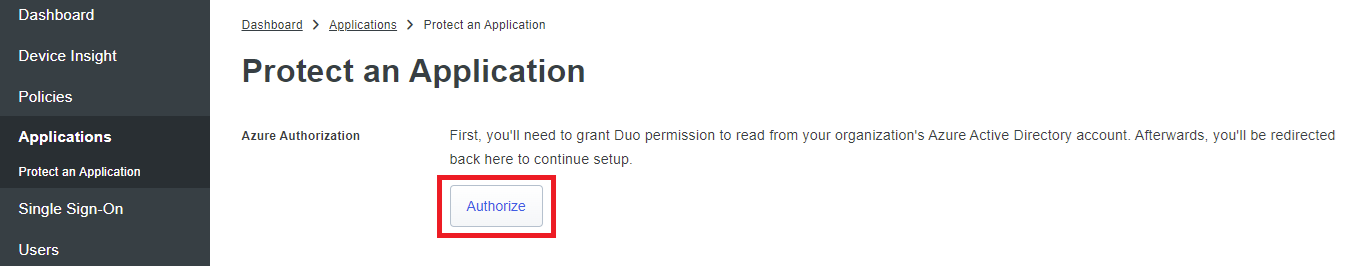
Click on the Authorize button to have Duo provide the Azure tenant sign-in prompt:
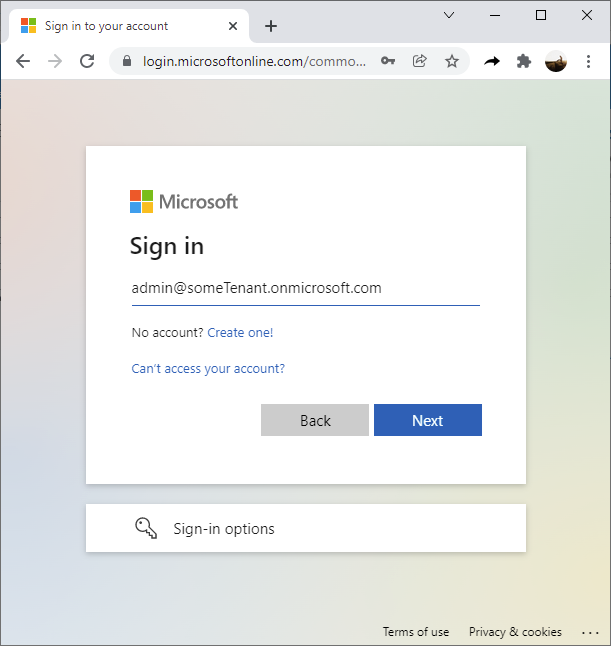
Sign into the Azure tenant with an account with global administrator permissions:
Authorize the permissions request:
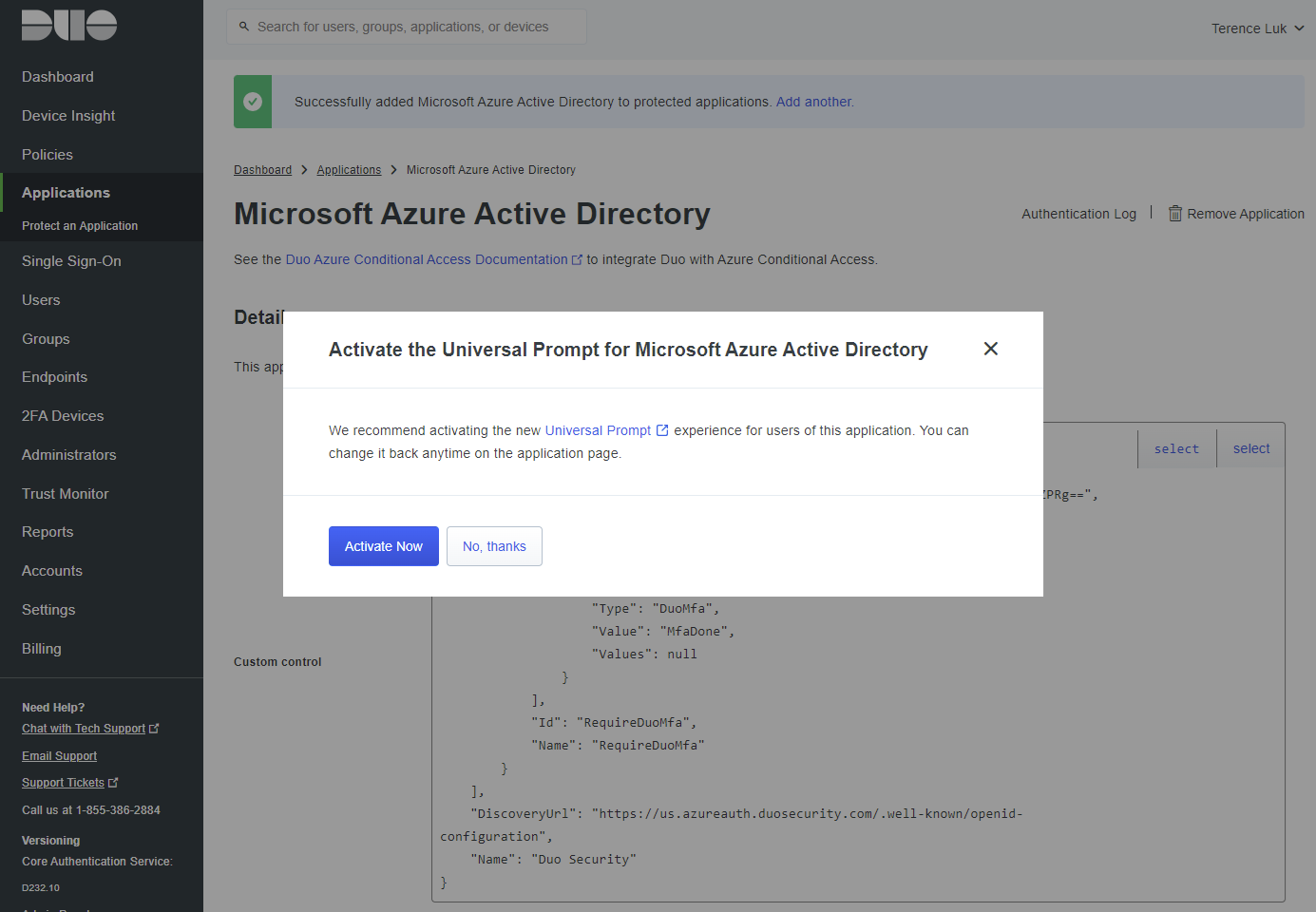
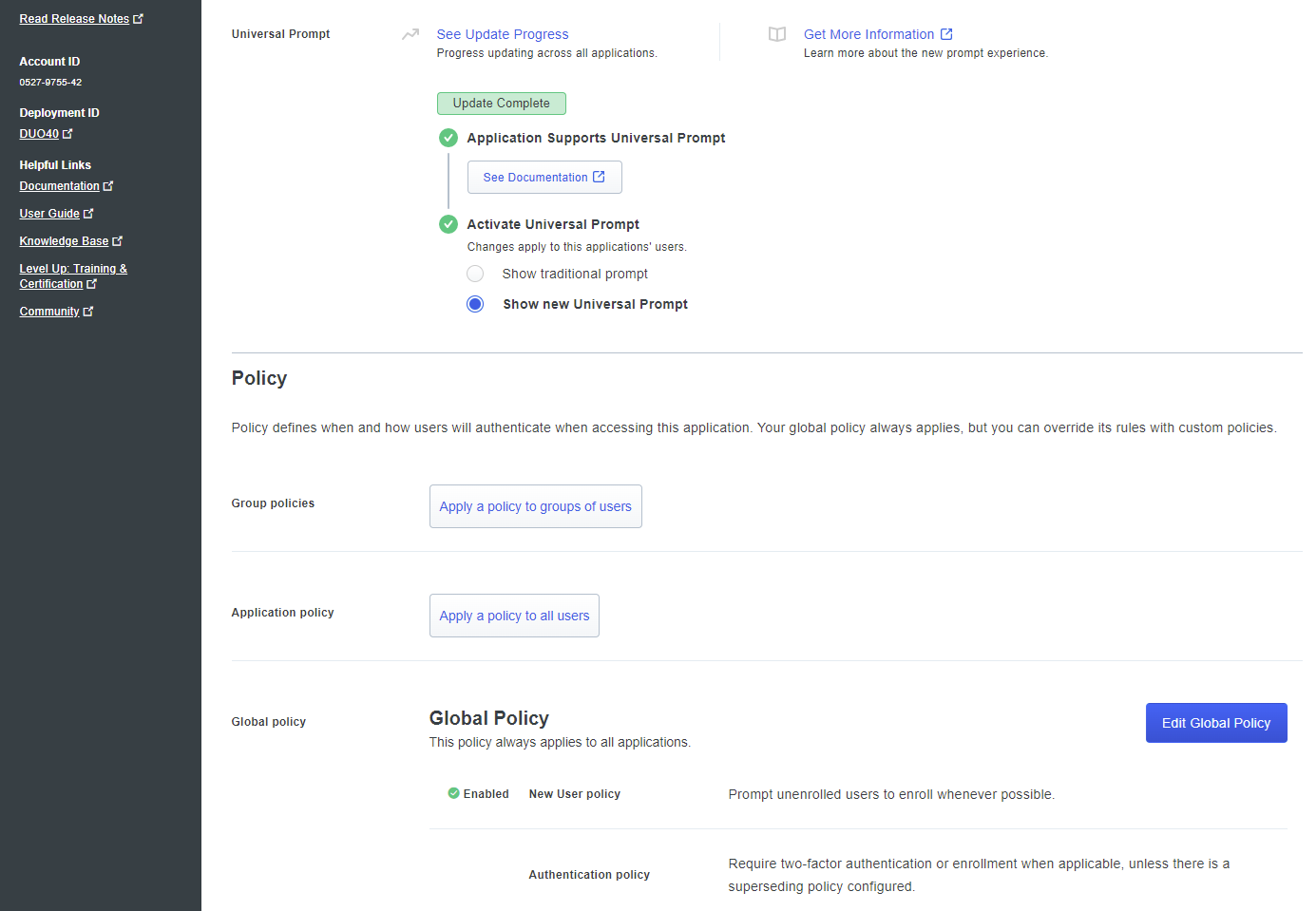
Decide on whether to activate the Universal Prompt for Microsoft Azure AD:
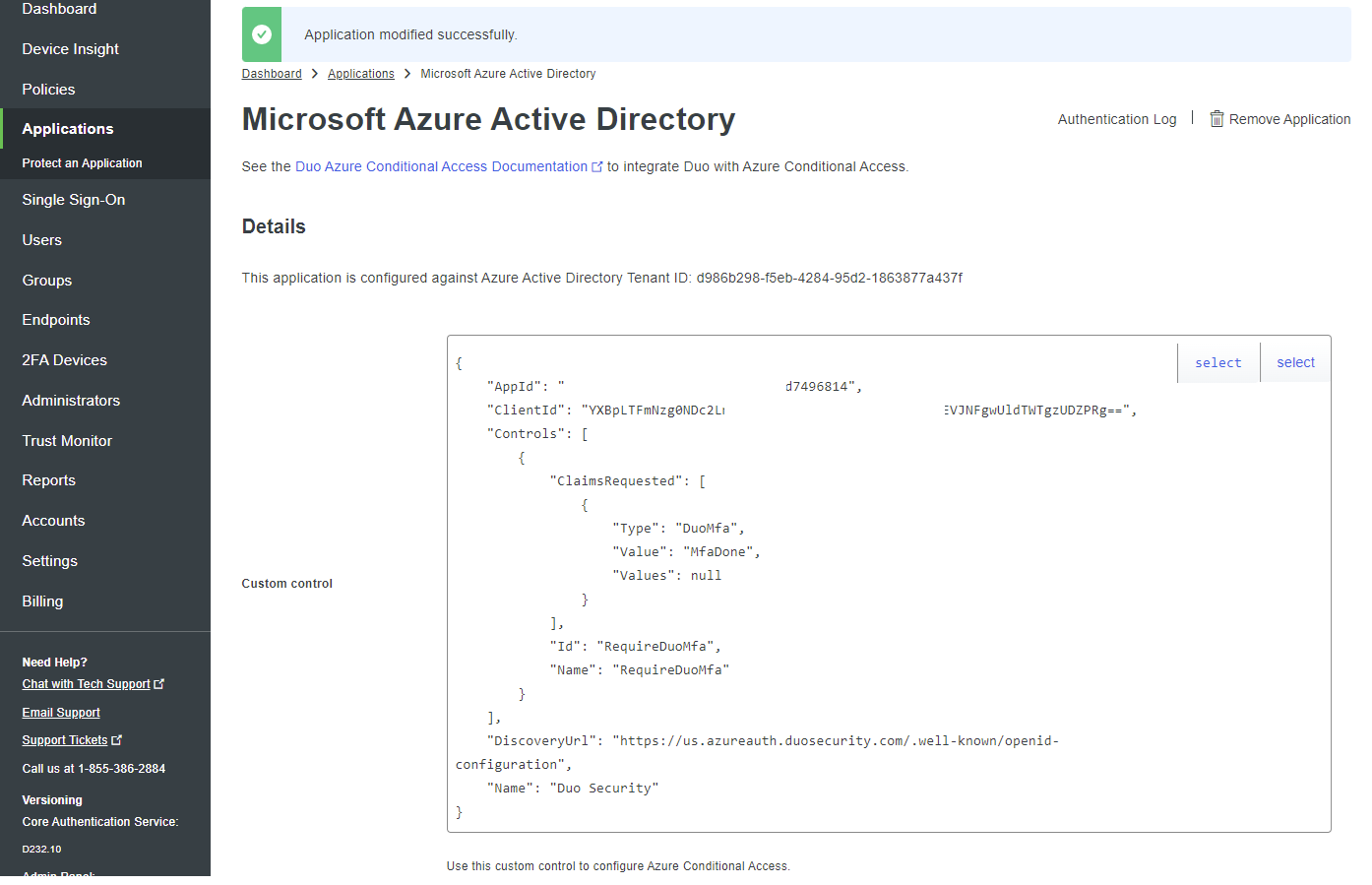
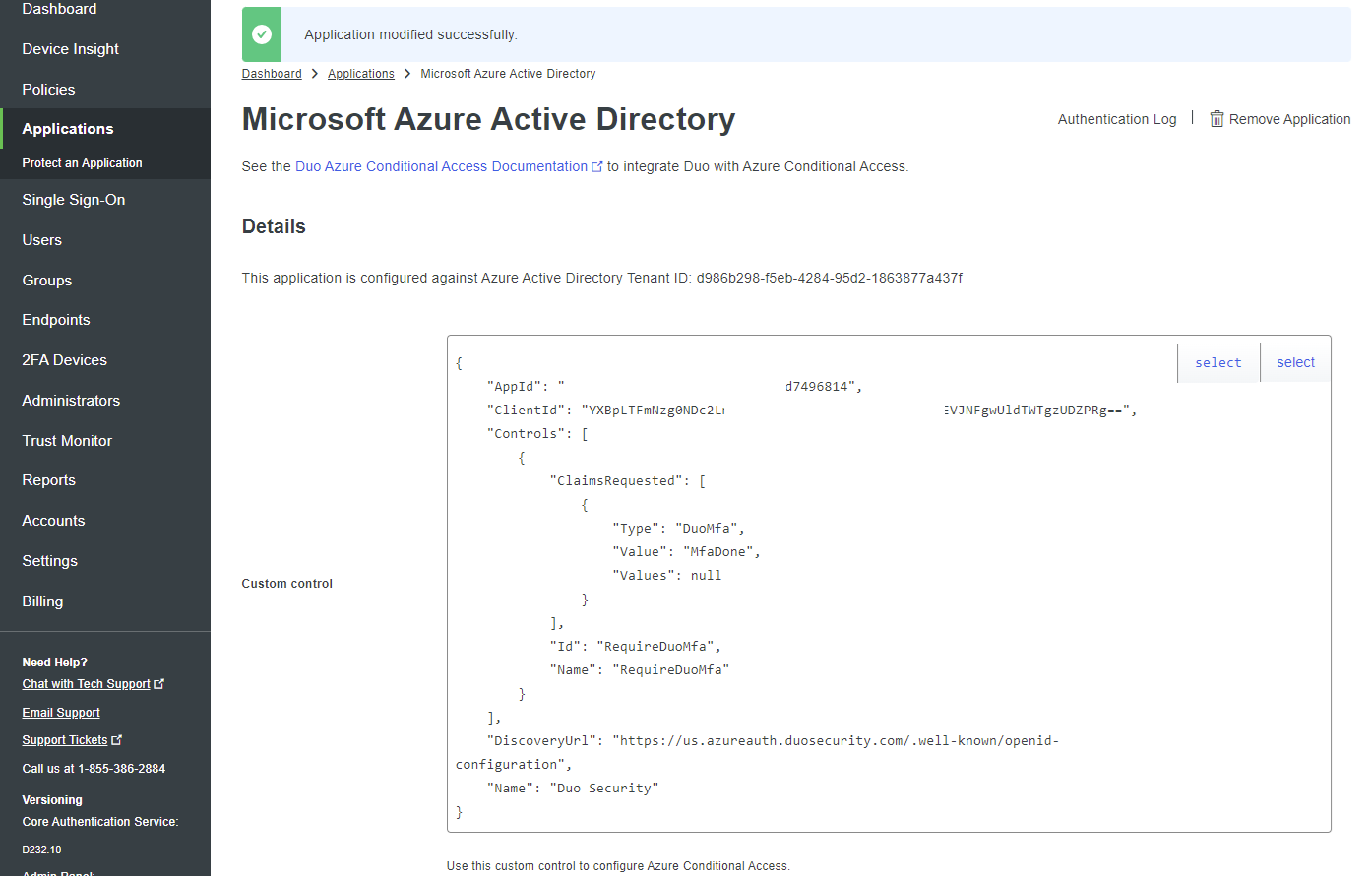
Copy the custom control code snippet into notepad as we’ll require it to configure Azure AD:
Scroll down and review the settings of the Azure AD application:
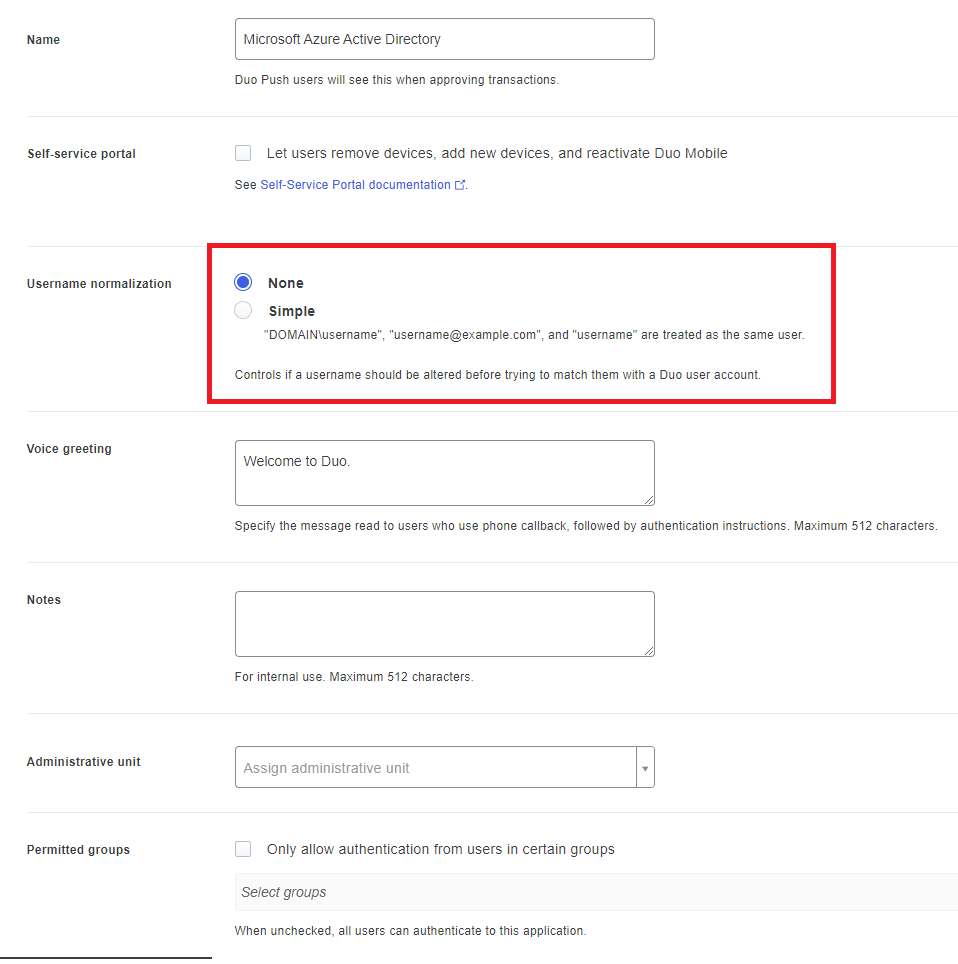
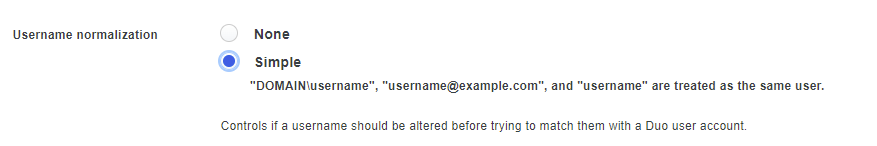
Locate the Username normalization setting and change the radio button from None to Simple. The reason why this setting is important is because failure to configuring this will cause Duo to create multiple accounts for the same user depending on the username used. For example, it may create two accounts for the logins:
- tluk
- tluk@contoso.com
- contosotluk
Proceed to save the configuration and you should now see the application created:
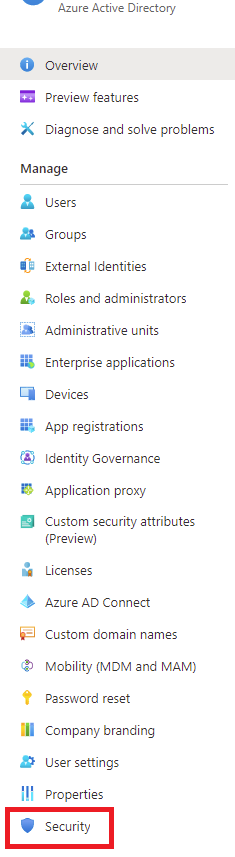
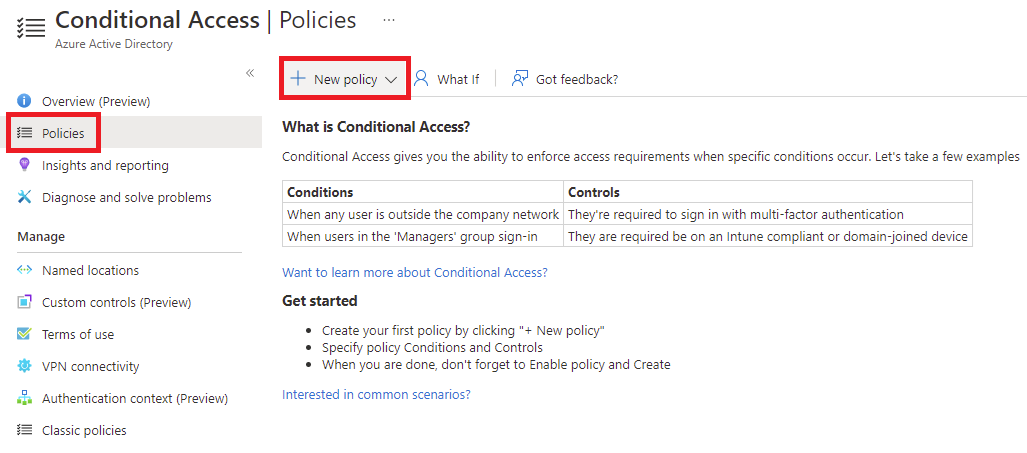
Login into https://portal.azure.com, navigate to Azure Active Directory and click on Security:
Select Conditional Access:
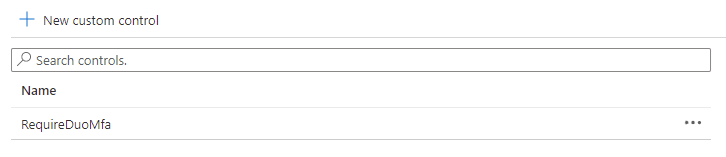
Click on Custom controls (Preview) and then New custom control:
Delete the existing content in the customized controls box:
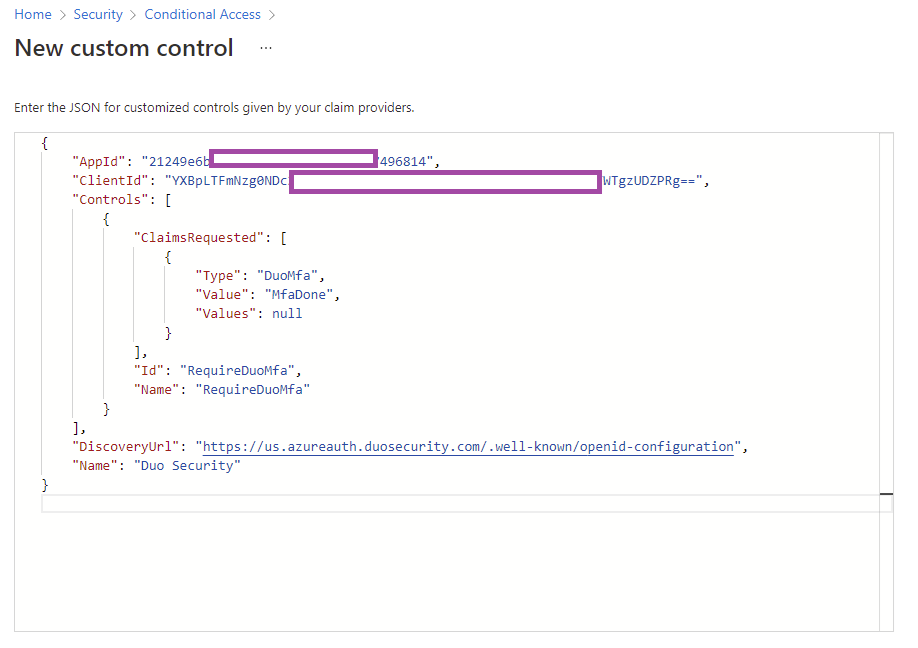
Paste the JSON snippet from Duo and click on Create:
Note the new custom control named RequireDuoMFA listed:
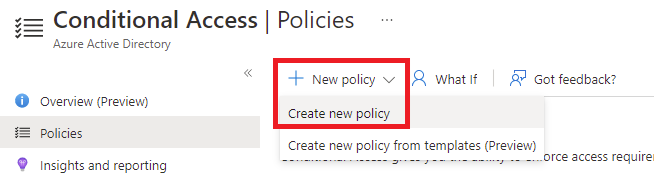
Navigate to Policies and click on New policy:
Note that if the New custom control button is greyed out then that means you do not have Azure AD Premium P1 licenses and therefore unable to use Conditional Access.
Select Create new policy:
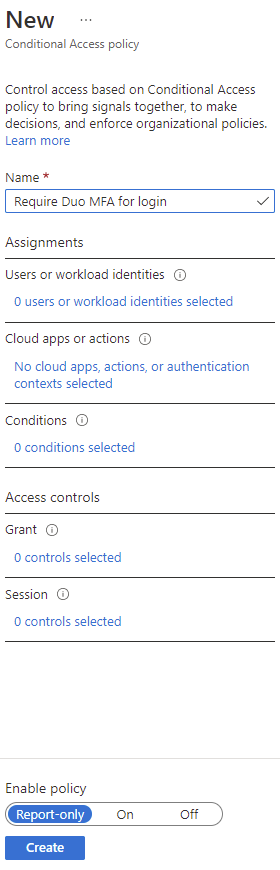
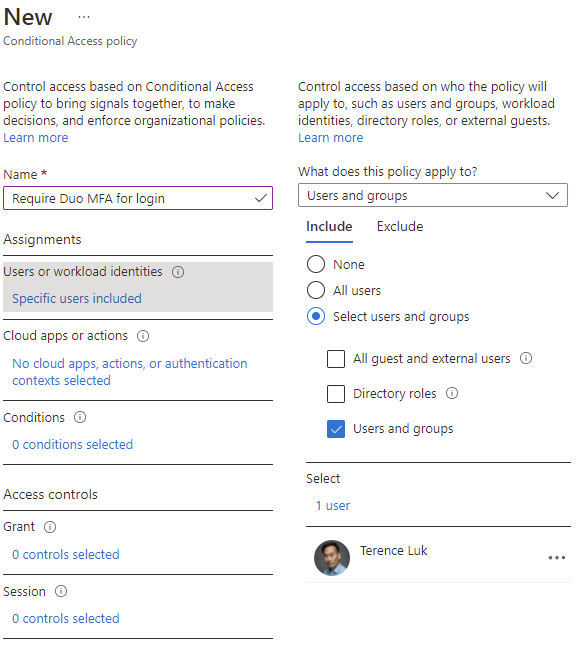
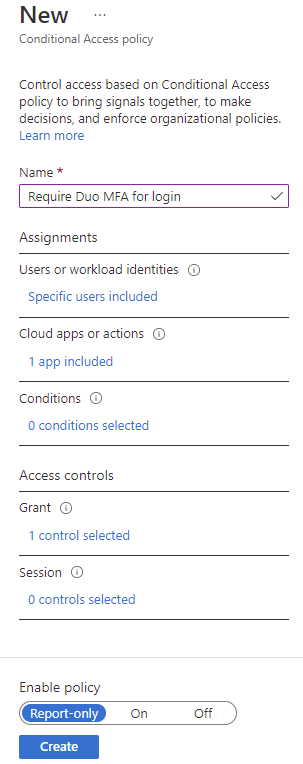
Provide a name for the policy:
Click on Specified users include under Users or workload identities and configure the users or groups that you want the policy to be applied to:
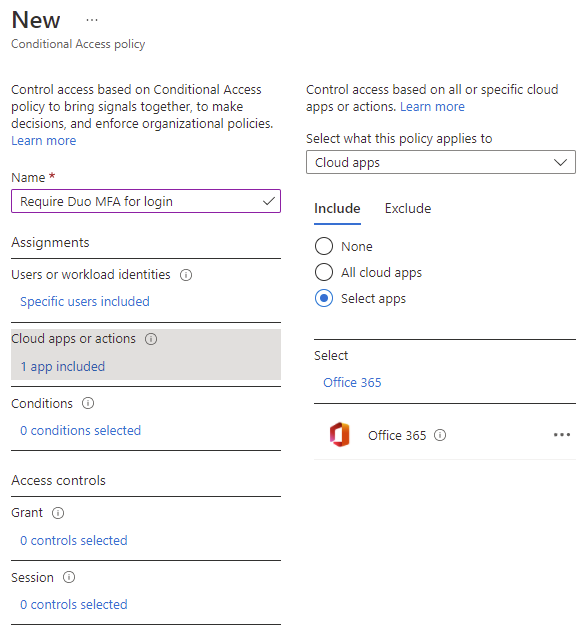
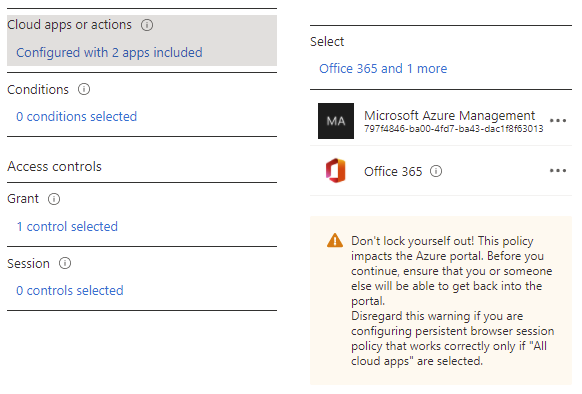
Click on No cloud apps, actions, or authentication contexts selected under Cloud apps or actions, select Select apps and configure the applications you want this policy to apply to. For this example, we’ll include Office 365 and Microsoft Azure Management:
Note that Azure reminds you to not lock yourself out as Microsoft Azure Management affects portal.azure.com. Microsoft provides guidance on having and managing emergency accounts in the following document: https://docs.microsoft.com/en-us/azure/active-directory/roles/security-emergency-access
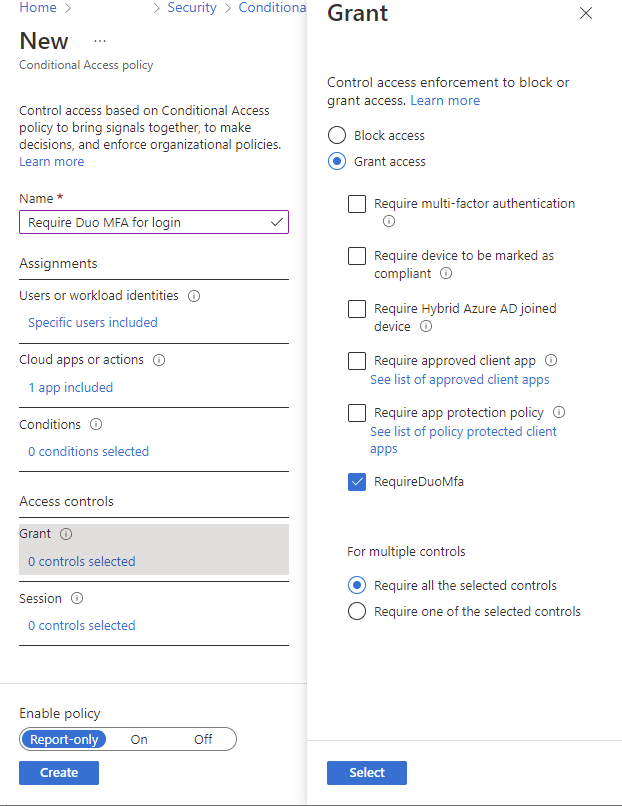
Select 0 controls selected under Access controls, select Grant access, enable RequireDuoMfa, and enable Require all the selected controls:
Note that if you do not see RequireDuoMfa then that means you skipped the custom control creation.
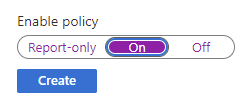
With the settings configured, you can choose to have Enable policy set as Report-only, which will only report expected behavior in the logs:
Or configured as On, which would put the policy in effect:
For this example, we will have the policy configured as On:
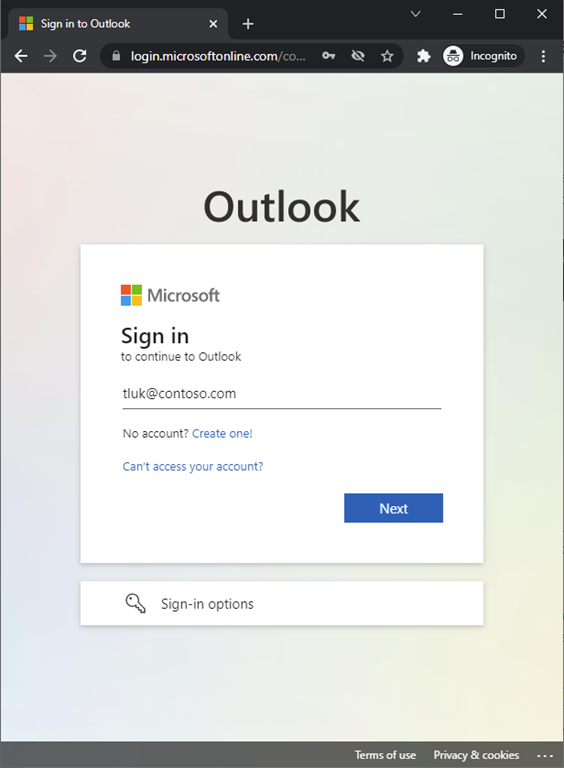
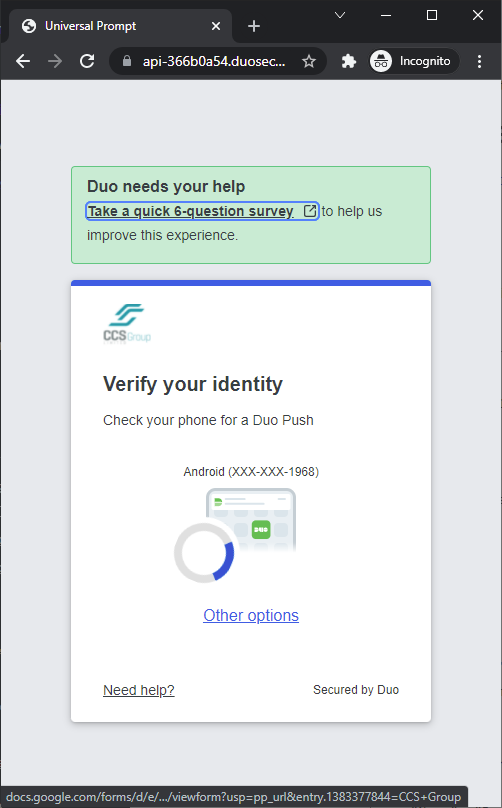
Proceed to test login and you should now see the following behavior:
Hope this provides an idea of what the process of configuring and using Duo as MFA looks like.