One of the most common activities I’ve had to perform when working with certificates is to convert Windows .pfx or .p12 certificate formats to Apache-compatible X509/Base65 or PEM/CER format that end with .key and .cer extensions. An example of a recent configuration I made was related to installing a certificate that is issued by a public CA onto an OpenVPN Access server I was testing. I already had a PFX file containing the export of the public and private key of my certificate but the file format that the OpenVPN Access server required files that were Apache-compatible X509/Base65 or PEM/CER format.
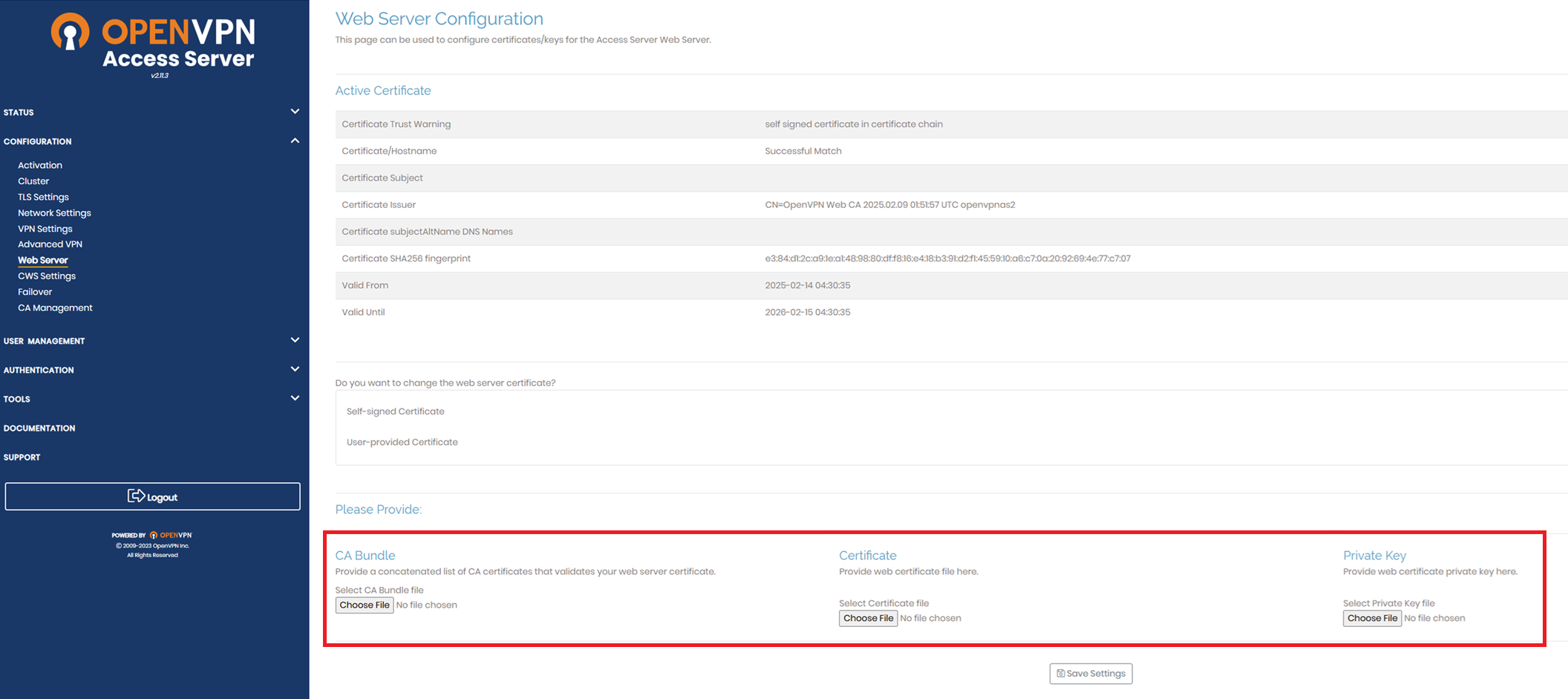
CA Bundle
Provide a concatenated list of CA certificates that validates your web server certificate.
Certificate
Provide web certificate file here.
Private Key
Provide web certificate private key here.
While the documentation from OpenVPN directs us to use the DigiCert Certificate Utility (https://openvpn.net/as-docs/tutorials/tutorial–install-ssl-certificate.html#step-2–get-your-ssl-certificate) to perform the conversion, most of us as administrators would be weary of using any external tool with our certificates. Long before this tool existed, the preferred tool is to use OpenSSL to perform the conversion and the purpose of this blog post is to provide the set of commands I use for the conversion.
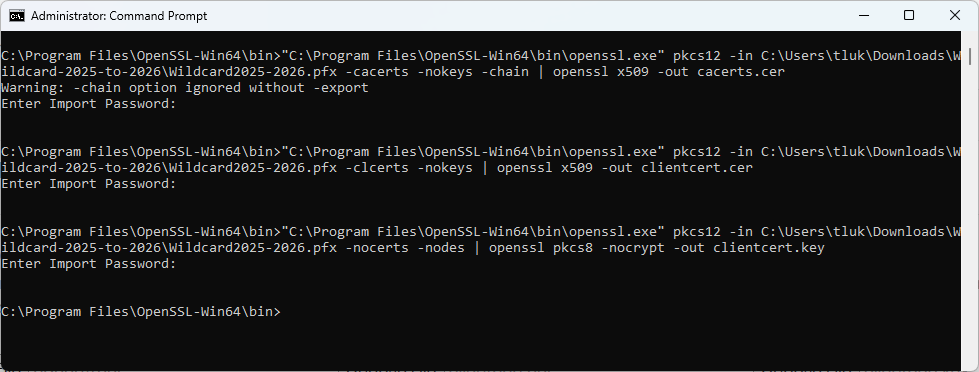
The following are the 3 set of commands that will allow us to generate the 3 files that OpenVPN accepts for configuring a user provided certificate:
CA Bundle
“C:\Program Files\OpenSSL-Win64\bin\openssl.exe” pkcs12 -in C:\Users\tluk\Downloads\Wildcard-2025-to-2026\Wildcard2025-2026.pfx -cacerts -nokeys -chain | openssl x509 -out cacerts.cer
Certificate (No Key)
“C:\Program Files\OpenSSL-Win64\bin\openssl.exe” pkcs12 -in C:\Users\tluk\Downloads\Wildcard-2025-to-2026\Wildcard2025-2026.pfx -clcerts -nokeys | openssl x509 -out clientcert.cer
Private Key
“C:\Program Files\OpenSSL-Win64\bin\openssl.exe” pkcs12 -in C:\Users\tluk\Downloads\Wildcard-2025-to-2026\Wildcard2025-2026.pfx -nocerts -nodes | openssl pkcs8 -nocrypt -out clientcert.key
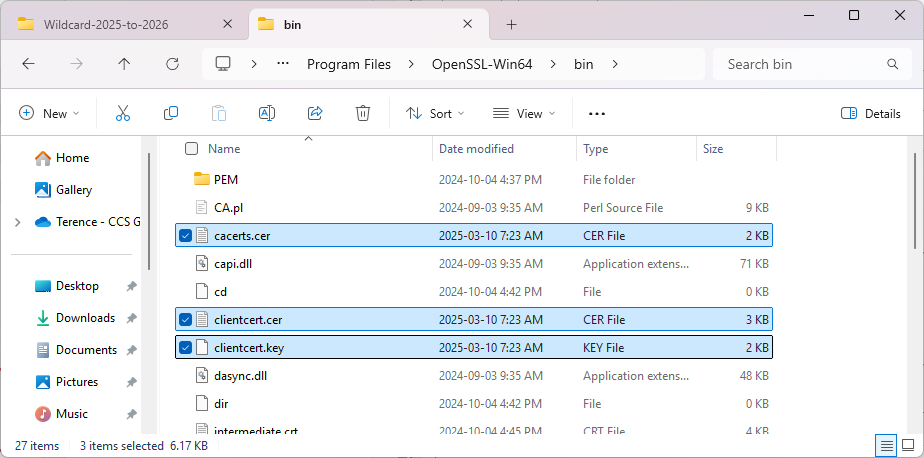
The corresponding 3 files will be created:
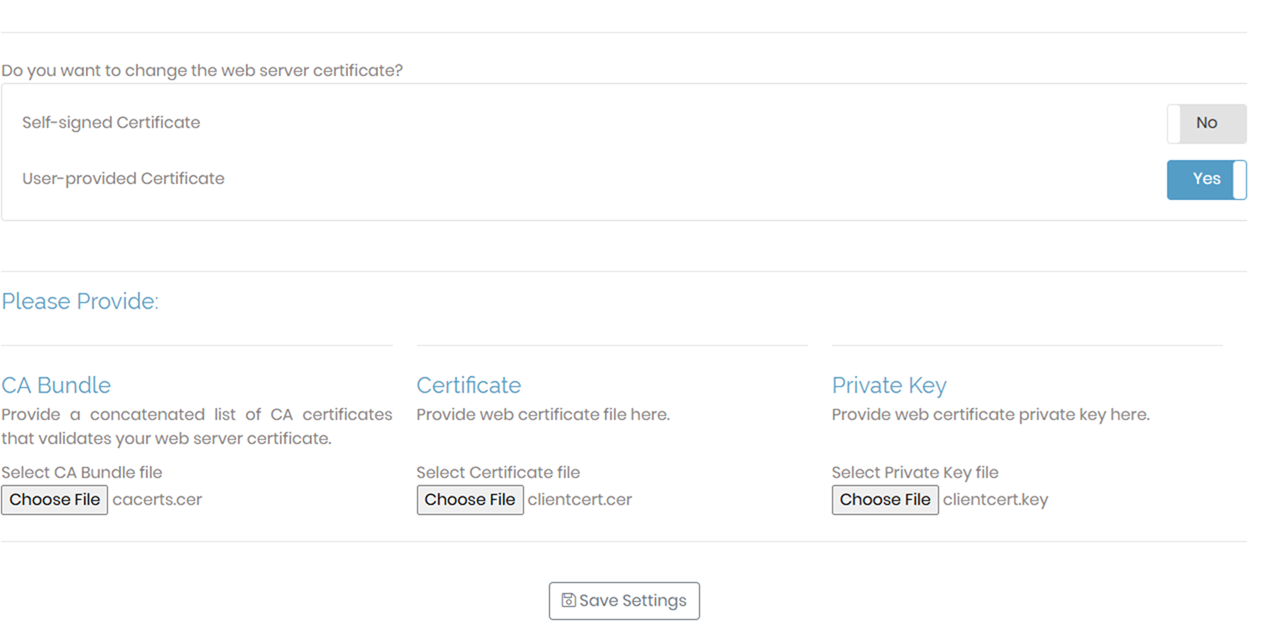
With these 3 files created, we can proceed to upload them into the OpenVPN Access Server to complete the configuration of a user provided certificate:
… and that’s it. Hope this provides anyone who may be looking for this set of commands.