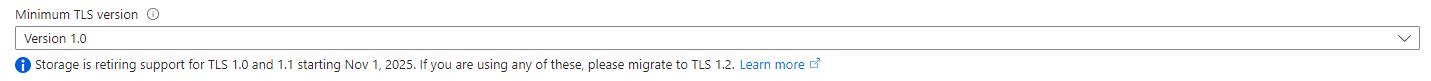
One of the projects I was involved in last year was a security audit for a set of Azure Data Lake storage accounts that stored sensitive data and one of the configuration settings I noticed immediately was that many of the storage accounts had the Minimum TLS version set as Version 1.0. What further increased the risk was that the public endpoints were enabled.
I can’t stress enough about how vulnerable TLS 1.0 (first defined in the year 1999) and 1.1 (first defined in April 2006) are but my assumption was that these storage accounts were either:
- Deployed a long time ago
- Had applications that still required TLS 1.0 for connectivity
- Whoever created these resources decided to use Version 1.0 without understanding the risks of this vulnerable protocol version
Regardless of the reason, our remit was to migrate the configuration to Version 1.2 because of security concerns as well as because Azure is retiring support for TLS 1.0 and 1.1 by November 1, 2024. I left the project before remediation was complete but I provided guidance on how to migrate to TLS 1.2 to the engineering team.
I received an email today from Microsoft indicating that the retirement of TLS 1.0 and TLS 1.1 will be delaying the retirement to August 31, 2025.
———————————————————————————————————————————————————————————————-
Update on retirement of TLS 1.0 and TLS 1.1 versions for Azure Services
Following the announcement on 10 November 2023, we’re continuing our transition to requiring TLS 1.2 or later for all connections to Azure services.
To minimize disruption to customer workloads, several services will continue supporting TLS 1.0 and TLS 1.1 versions and complete their transitions by 31 August 2025 when TLS 1.2 or later will be required for all connections to Azure services (unless explicitly indicated in service documentation). The list of remaining services will be updated as transitions to TLS 1.2 or later complete.
While the Microsoft implementation of TLS 1.0 and TLS 1.1 versions isn’t known to have vulnerabilities, TLS 1.2 or later versions provide improved security features, including perfect forward secrecy and stronger cipher suites.
Customers still using TLS 1.0 or 1.1 should transition their workloads to TLS 1.2 or later versions to ensure uninterrupted connectivity to Azure services.
Recommended action
To avoid potential service disruptions, confirm that your resources that interact with Azure services are using TLS 1.2 or later. Then:
- If they’re already exclusively using TLS 1.2 or later, you don’t need to take further action.
- If they still have a dependency on TLS 1.0 or 1.1, transition them to TLS 1.2 or later.
Help and support
Read more about the update to TLS 1.2. If you have questions, get answers from community experts in Microsoft Q&A. If you have a support plan and you need technical help, please create a support request.
———————————————————————————————————————————————————————————————-
Navigating to the Azure portal, into a Storage Account’s configuration, shows the date of November 1, 2025. I’m not sure which one is correct but every organization should move towards requiring TLS 1.2 as soon as possible and hopefully not wait until August or November 2025.
The challenge with the data lake storage accounts for the client I was working with was that they had many different services accessing the contents stored in these storage accounts. As I worked on this project in 2023, Microsoft had not published the following article:
Enforce a minimum required version of Transport Layer Security (TLS) for requests to a storage account
https://learn.microsoft.com/en-us/azure/storage/common/transport-layer-security-configure-minimum-version?tabs=portal
The article above provides great guidance for how to determine what external connections are still accessing the storage account through the use of Log Analytics so I won’t need to post the similar KQL queries I used for reviewing inbound connections from client applications. Additionally, it also provides recommendations for using Azure Policies for auditing as well as enforcing the minimum TLS version.
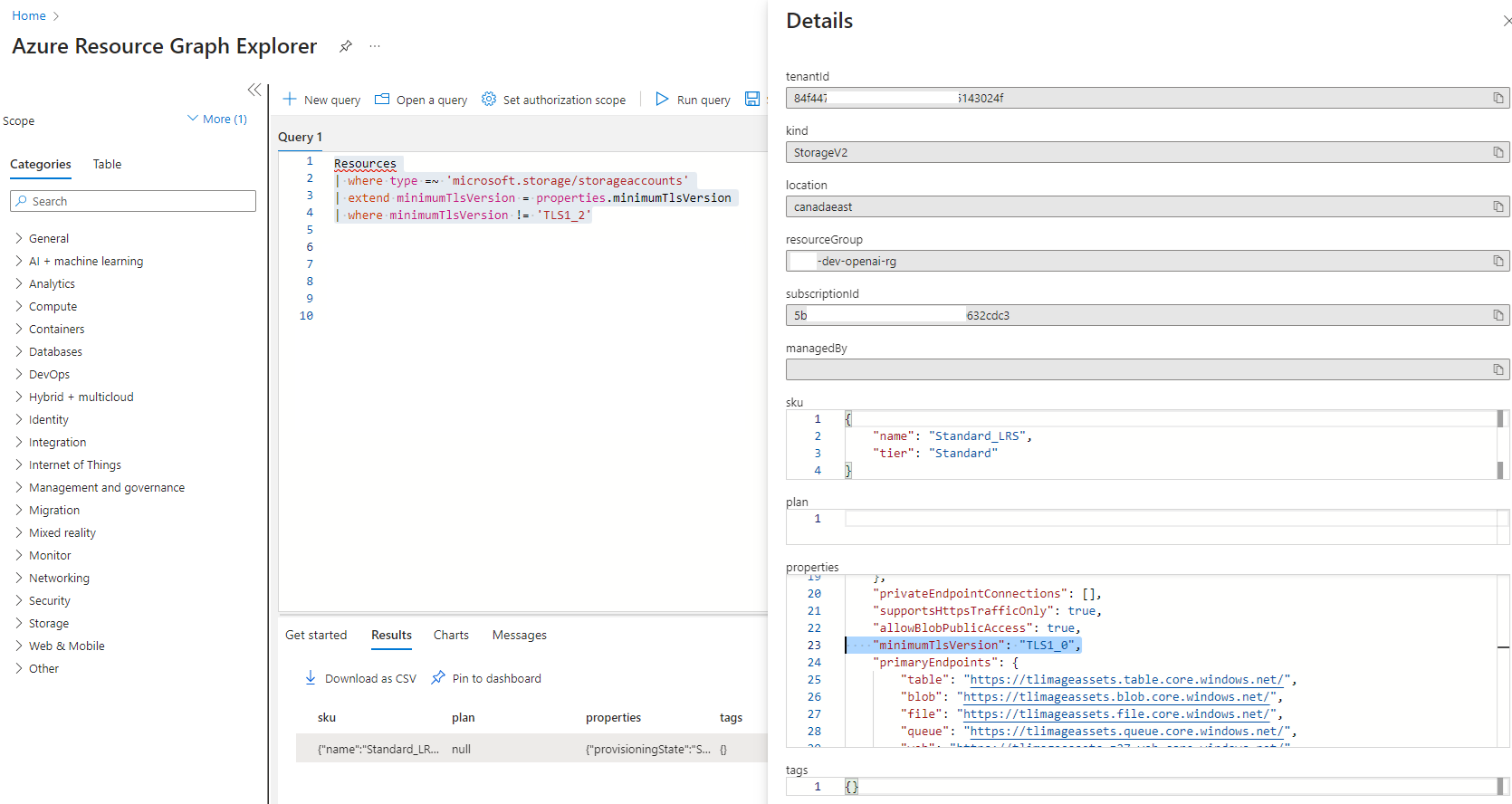
This leaves me with the only item that the article does not provide and that is how to gather a list of Azure Storage Accounts that do not have the Minimum TLS version set as Version 1.0. The method I prefer to use is via the Azure Graph Explorer where I would query of all microsoft.storage/storageaccounts resource type, and look for the minimumTlsVersion key value pair of the resource’s properties:
If you want to look for all storage accounts that are configured as TLS 1.2 then you can change the != to ==:
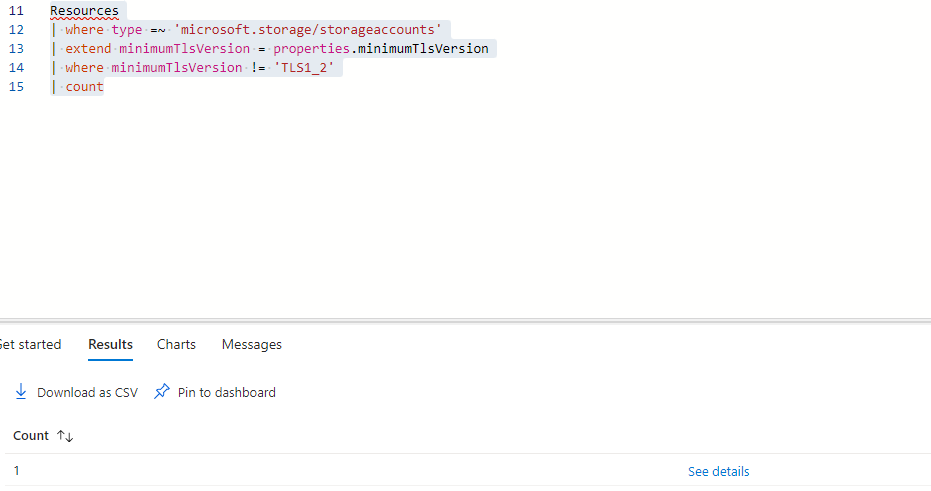
If you want to just perform a count then you can use the following query: